Microsoft Threat Intelligence has uncovered a severe macOS security vulnerability that could allow attackers to steal sensitive user data typically protected by Apple’s privacy controls, including information cached by Apple Intelligence systems.
The vulnerability, dubbed “Sploitlight,” represents a significant security risk for Mac users and has already been patched by Apple.
Vulnerability Details and Impact
The Sploitlight vulnerability exploits macOS Spotlight plugins to bypass Transparency, Consent, and Control (TCC) protections, which are designed to prevent unauthorized access to users’ information.
Unlike previous TCC bypasses, this vulnerability poses more severe risks due to its ability to extract sensitive data cached by Apple Intelligence, including precise GPS coordinates, photo and video metadata, face recognition data, search history, and user preferences.
The attack method involves manipulating Spotlight importers – plugins that help macOS index files for search functionality.
Attackers can create malicious plugins that exploit the privileged access these importers have to sensitive files, effectively bypassing Apple’s security restrictions.
Particularly concerning is the vulnerability’s ability to access Apple Intelligence caches stored in protected directories like the Pictures folder.
Data Exposure Risks
The compromised data includes highly sensitive information that could severely impact user privacy.
Attackers could potentially access GPS coordinates associated with photos and videos, creating detailed location histories that reconstruct users’ movements over time.
Face and person recognition data, sometimes linked to contact names, could also be exposed along with photo albums and shared library details.
The vulnerability’s impact extends beyond individual devices due to iCloud’s cross-device synchronization.
An attacker gaining access to one macOS device could potentially extract information about other devices linked to the same iCloud account, including data from the victim’s iPhone.
Additionally, threat actors could access other Apple Intelligence cached files, such as email summaries and notes created with AI assistance.
Response and Mitigation
Microsoft discovered the vulnerability during proactive security research and responsibly disclosed it to Apple through coordinated vulnerability disclosure procedures.
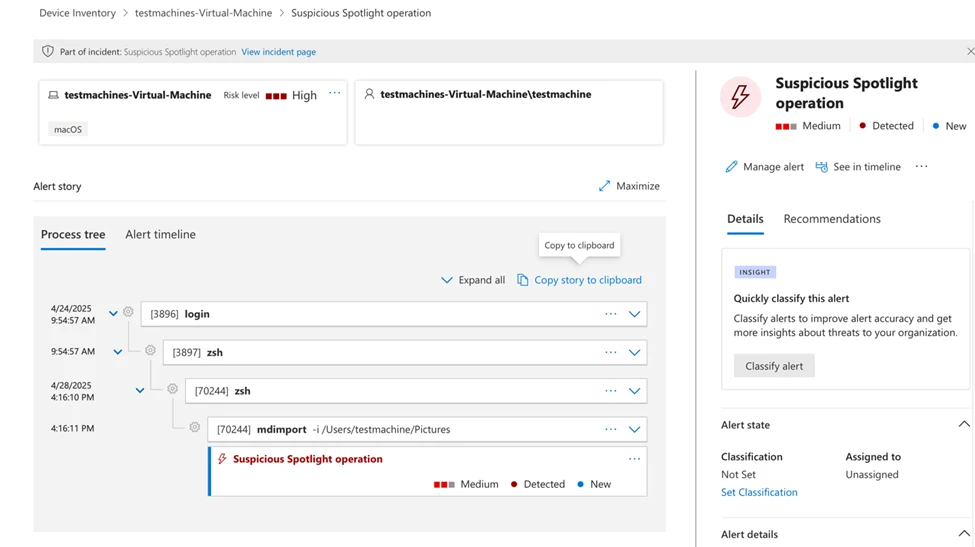
Apple has since addressed the issue, assigning it the identifier CVE-2025-31199, and released security updates for macOS Sequoia on March 31, 2025.
Microsoft has enhanced its Defender for Endpoint security solution to detect suspicious Spotlight plugin installations and unusual indexing activities targeting sensitive directories.
The company emphasizes the importance of continuous collaboration between security vendors and the broader cybersecurity community to identify and mitigate such vulnerabilities before they can be exploited.
Security experts strongly recommend that all macOS users immediately apply Apple’s security updates to protect against this vulnerability.
The incident highlights the evolving nature of cybersecurity threats and the critical importance of maintaining up-to-date security patches on all devices, particularly as AI-powered features become more prevalent in consumer technology.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates