A recent wave of sophisticated malware campaigns has been uncovered by the Acronis Threat Research Unit (TRU), highlighting evolving attack techniques that blend fake indie game hype, social engineering, and hijacked branding to compromise Windows systems.
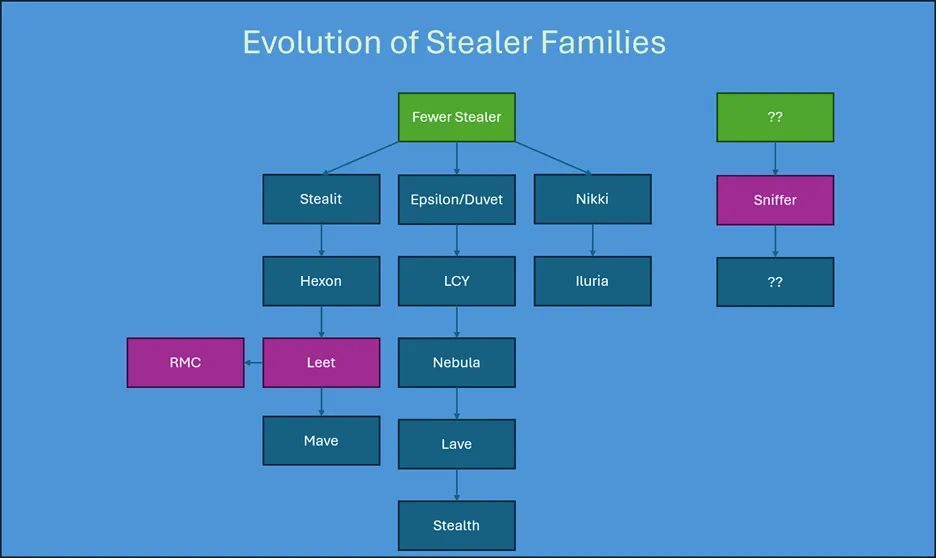
Campaigns distributed via fraudulent websites, YouTube channels, and primarily Discord leverage three Electron-based stealer families.
Malicious Campaigns Hijack Indie Game Hype
Leet Stealer, its customized variant RMC Stealer, and the independently developed Sniffer Stealer.
The attackers target gamers with fake installers disguised as unreleased or early-access indie games such as Baruda Quest, Warstorm Fire, Dire Talon, and WarHeirs, using legitimate branding assets stolen from popular titles to foster trust.
Distribution is driven by engaging promotional content including fabricated websites, stolen game artwork, and lively YouTube trailers for games that, in reality, do not exist.
Download links are often routed through Discord, where the gaming community readily shares beta access files and new game announcements.
To further the illusion, Android and macOS downloads from these fake sites redirect to legitimate unrelated software, while Windows downloads deploy the actual malicious payload.
The campaign’s primary goal is to harvest sensitive user data including browser credentials, Discord tokens, payment details, cryptowallets, and private messages through clever exploitation of the Electron framework for cross-platform desktop apps.
Advanced Stealer Functionality
Technical investigation revealed that Leet Stealer, first appearing in late 2024 as a “malware-as-a-service,” underpins much of this activity and has spawned numerous derivatives.
RMC Stealer, for example, was created as a custom modification for threat actors, confirmed through code overlap.
Attackers distribute their wares for a recurring subscription fee via Telegram channels and offer bespoke versions on request.
While Leet Stealer and its variants are closely related, Sniffer Stealer appears to be developed independently, though sharing many common behaviors and targeting goals.
A key discovery occurred when TRU researchers found that the Baruda Quest sample inadvertently included the original, unobfuscated source code within its Electron ASAR archive providing rare insights into the malware’s construction.

The executable itself, a bloated NSIS installer exceeding 80MB, enjoys a very low detection rate among antivirus solutions, mainly due to its size and the inherent obfuscation provided by embedding the Electron runtime and JavaScript bytecode.
Once extracted, analysis shows robust sandbox detection mechanisms, which examine virtual machine artifacts and hardware configurations to thwart security researchers.
Should the malware sense a sandbox, it generates a convincing error message, mimicking game crashes or misconfigurations to avoid suspicion.
Upon successful execution, the malware aggressively harvests browser data including cookies, passwords, and form data from all major Chromium-based browsers.
Leveraging browser debug mode, it extracts credentials and compresses stolen data for exfiltration via third-party file sharing services such as gofile.io, file.io, catbox.moe, and tmpfiles.org.
Discord credential theft is a prime focus; stolen tokens enable attackers to impersonate victims, propagate malware further, scam users, and, in some cases, extort victims for account access.
In addition to Discord, the stealers target Microsoft, Steam, Epic Games, Growtopia, MineCraft, WhatsApp, Telegram, and unofficial Discord modifications like BetterDiscord.
Further, these threats can download and execute additional malicious payloads, demonstrating a modular design adaptable to ongoing campaigns.
Notably, evidence points to a Brazilian origin for the campaign; many default languages are set to Portuguese, and virus submission telemetry shows a predominance of victims in Brazil, with a significant footprint in the United States, likely owing to Discord’s global user base.
According to the report, These attacks mark a significant evolution in stealer campaigns, leveraging both technical and psychological manipulation to maximize reach and effectiveness.
Electron-based architecture enables cross-platform deployment, while social engineering and credible branding hoodwink even savvy gamers.
With the rapid spread of malware via Discord and YouTube, vigilance and enhanced endpoint protection are crucial, as traditional detection engines lag in identifying such threats.
Indicators of Compromise (IOC)
| Filename | Stealer Family | SHA256 |
|---|---|---|
| babacan32 Setup 1.0.0.exe | Leet | 5c7c70ab9734838795050a91f08f1af9e3cb479caf20bd34944282e8ac455ea7 |
| BarudaQuest.exe | RMC | 813e5923e6d4df56055f5b5200db2e074e89f64dea3099e61fbde78c0fc23597 |
| BillieBust.exe | Sniffer | 567fb96e8b101abc45f2dfba470ea8a7298063f7428409d8b7e5c8f4326b6dc0 |
| Brosxa 1.0.0.exe | Leet | b9adcf54b09475ed2023f5b3c03e23013e65195b4e8bfbb82c8c13fde194b2d4 |
| Depthcan.exe | Leet | 798eee15a3e93ee0d261501df979dc3b61a9e5992188edeada5beaba0b30b8df |
| DireTaloGaSetup.exe | Sniffer | 35ad1623694496ec91bc853b391c8bebdfa1aeaea2c4dcf74516e2cd13ab44f4 |
| Sokakcan.exe | Leet | a3636b09302a77ed7a6c75c5e679ba9ed0dbe12892f5fe94975ab3ef6be7ade8 |
| SpectraLauncher.exe | Sniffer | cee750d6cb834b766a214b6609ed4eca62b0330a9904cf2f77b184a77e70f4d3 |
| SteppulGame.exe | Leet | 6f441dc6a45fd6dac4fe19707c6338b8bca1aabfb7842d7ebf94fb2fab2f12d5 |
| SumaleDepth Setup 1.0.0.exe | Leet | 051028c2acc74cb55f5a5e28c7ba1613fd4a13dcf5f6a6325557ae1b88900ee8 |
| Terrnua Setup 1.0.0.exe | Leet | 767f575d30deb66244b29bafae51111fdb869ba26d1df902e3f839bdb64725f9 |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates