Microsoft has announced a major security upgrade for Teams administrators, enabling rule-based management of third-party apps via Message Center update MC1085133 (Roadmap ID 48571).
Launching globally between mid-August and early September 2025, this feature empowers admins to control Microsoft 365-certified apps through conditional rules in the Teams admin center.
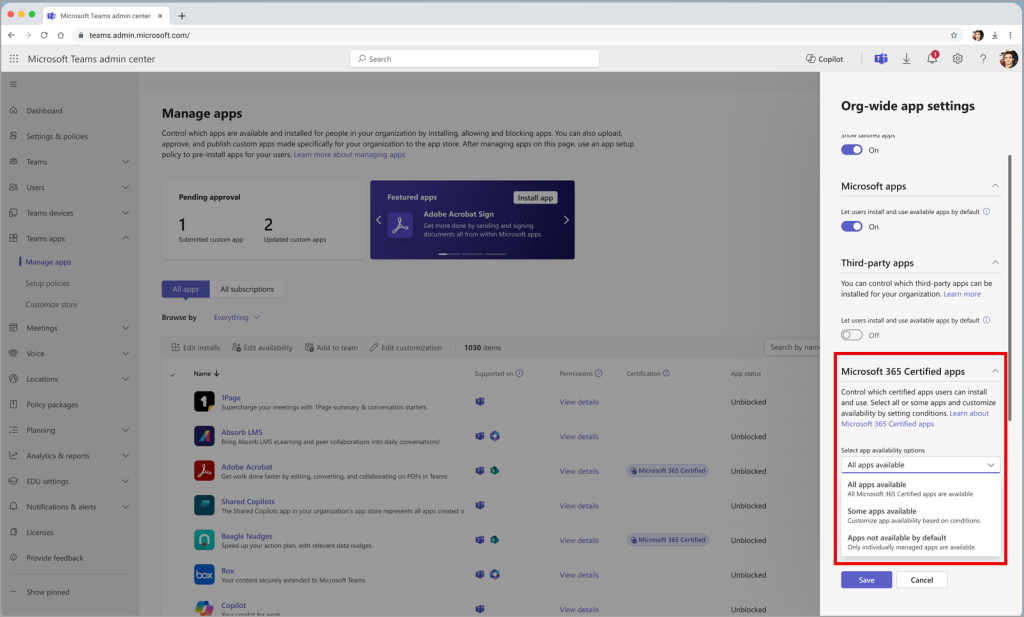
Using Org-wide app settings, admins can now customize app availability based on criteria like permissions accessed and publisher verification.
The feature defaults to “All apps available” but allows refinement via Customize availability to block high-risk integrations.
This shift replaces legacy third-party app tenant settings with dynamic, policy-driven controls for enhanced security posture.
Rollout Timeline and Operational Impact
The update rolls out automatically worldwide starting mid-August 2025, concluding by early September.
Post-deployment, admins will access the controls at Manage apps > Actions > Org-wide app settings > Microsoft 365 certified apps.
Organizations previously disabling Org-wide app settings for third-party apps face critical adjustments: A 30-day grace period post-launch allows configuration changes before settings enforce app availability.
Post-grace period, policy enforcement becomes immediate.
Tenants with existing third-party app settings enabled require no action, though Microsoft recommends auditing current configurations using PowerShell cmdlets like Get-CsTeamsAppPermissionPolicy to assess overlap risks.
Admin Preparation and Best Practices
Admins must:
- Review configurations: Audit existing app policies via the Teams admin center or PowerShell.
- Notify users: Communicate upcoming app availability changes, especially if restricting permissions like
Files.Read.AllorMail.Send. - Document adjustments: Update internal playbooks referencing Org-wide app settings paths.
Post-rollout, Microsoft Learn documentation will include new guidance (Manage org-wide app settings). - Proactive testing in Teams Developer Portal sandbox environments is advised to validate rule sets. Failure to configure within the 30-day grace period may disrupt app access for licensed users, particularly those dependent on line-of-business integrations.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates