A new wave of Android malware analyzed by CERT Polska has revealed a sophisticated NFC relay technique targeting Polish bank users. Named “NGate,” the campaign enables criminals to withdraw cash at ATMs using victims’ own payment cards without physically stealing them.
The attack merges advanced mobile exploitation with precise social engineering designed to trick users into relaying their card data.
Phishing and Social Engineering Setup
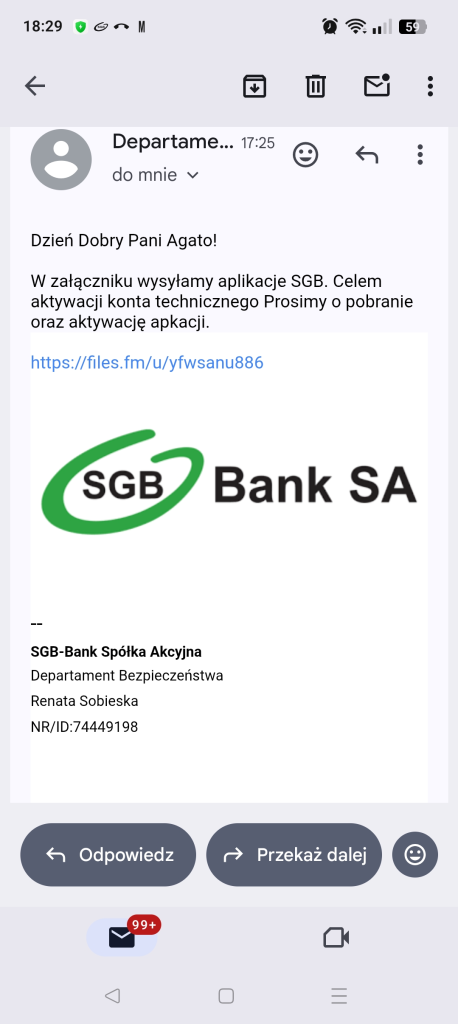
The attack chain begins with phishing messages pretending to be bank alerts about technical or security issues. Victims receive emails or SMS messages linking to malicious websites distributing a fake “bank support” application.
The app, available from a file-sharing service (files[.]fm/u/yfwsanu886), impersonates legitimate mobile banking tools. To reinforce credibility, scammers then make follow-up phone calls posing as official bank representatives and send SMS confirmations to “verify” the bank employee’s identity.
Once convinced, victims are asked to install the app and “confirm” their card by tapping it against their phone via NFC and entering the PIN using an on-screen keypad. This process covertly captures the card’s EMV data and PIN, which are transmitted in real time to an attacker’s system at an ATM.
Technical Mechanism and Relay Functionality
CERT Polska’s analysis shows that the Android app registers itself as a Host Card Emulation (HCE) payment service, allowing it to function as a virtual card. The malware operates in “reader mode,” intercepting the card’s NFC communication.
The captured data, Primary Account Number (PAN), expiry date, AIDs (Application Identifiers), and PIN are sent to the threat actor through a custom TCP-based communication protocol.
A critical discovery was the decrypted configuration file stored inside the APK. Using an XOR operation keyed with the SHA-256 hash of the app’s signing certificate, analysts recovered the command-and-control (C2) server address: 91.84.97.13:5653.
Communication with the server is performed in plaintext frames (length, opcode, body), with periodic keep-alives every seven seconds. This minimal encryption makes network traffic easily identifiable through forensic signatures.
CERT researchers found that the malware’s core logic resides in a native library, libapp.so, responsible for decrypting configuration data and initializing the network connection.
Once operational, the malware exfiltrates all card data and PINs to the remote host, enabling attackers to replay the NFC traffic at ATMs through another device acting as the “emitter.”
Real-World Impact and Mitigation
NGate’s structure shows clear support for dual roles, reader and emitter, enabling complete NFC relay attacks. With the victim’s phone capturing data and the attacker’s device emulating a payment card at the ATM, the setup allows instant cash withdrawals.
CERT Polska advises users to download only verified banking apps from official stores and always contact their bank directly if asked to install additional verification applications.
IOC
2cee3f603679ed7e5f881588b2e78ddc
701e6905e1adf78e6c59ceedd93077f3
2cb20971a972055187a5d4ddb4668cc2
b0a5051df9db33b8a1ffa71742d4cb09
bcafd5c19ffa0e963143d068c8efda92
91.84.97.13:5653
files[.]fm/u/yfwsanu886Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates