North Korean state-sponsored hackers from the APT37 group have developed sophisticated new attack methods that hide malicious software inside seemingly innocent JPEG image files, according to a comprehensive analysis by Genians Security Center.
This advanced steganography technique represents a significant evolution in cyber warfare tactics, making detection by traditional security systems complicated.
Advanced Steganographic Concealment Methods
The newly discovered RoKRAT malware variant employs a two-stage encryption process that begins with malicious shortcut files disguised as legitimate documents.
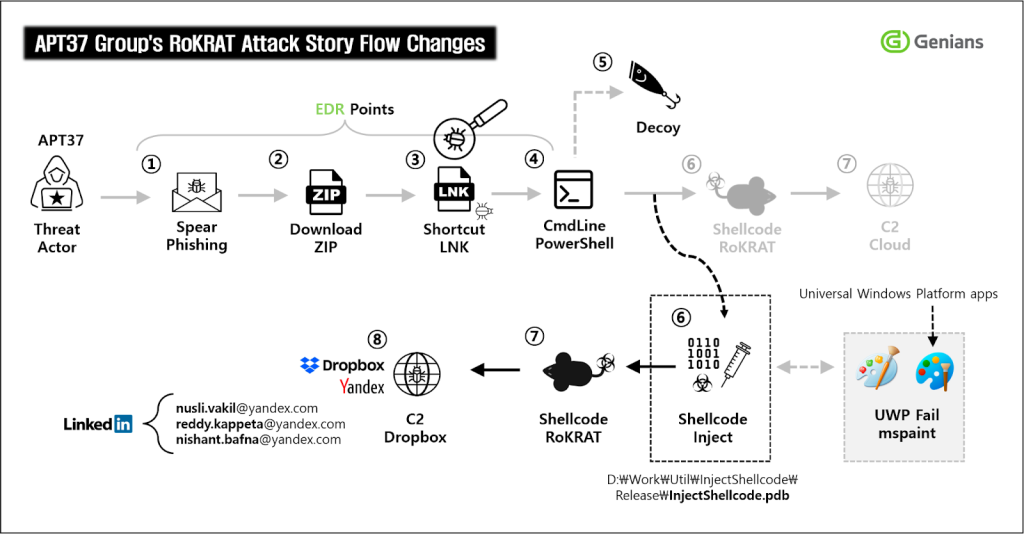
These .lnk files, huge at 54MB, contain embedded shellcode that downloads JPEG images from cloud storage services like Dropbox. However, these images contain far more than photographs.
The malicious JPEG files begin with valid image headers showing actual human faces, but hidden within their data structure lies encrypted malware code.
The attack sequence involves multiple XOR decryption operations using specific key values, first 0xAA, then 0x29, to reveal the concealed RoKRAT payload.
This technique enables cybercriminals to circumvent image-scanning security filters, which typically focus on file headers rather than analyzing complete file contents.
Security researchers identified the steganographic payload embedded at offset 0x4201 within the image files, demonstrating the attackers’ sophisticated understanding of file format structures.
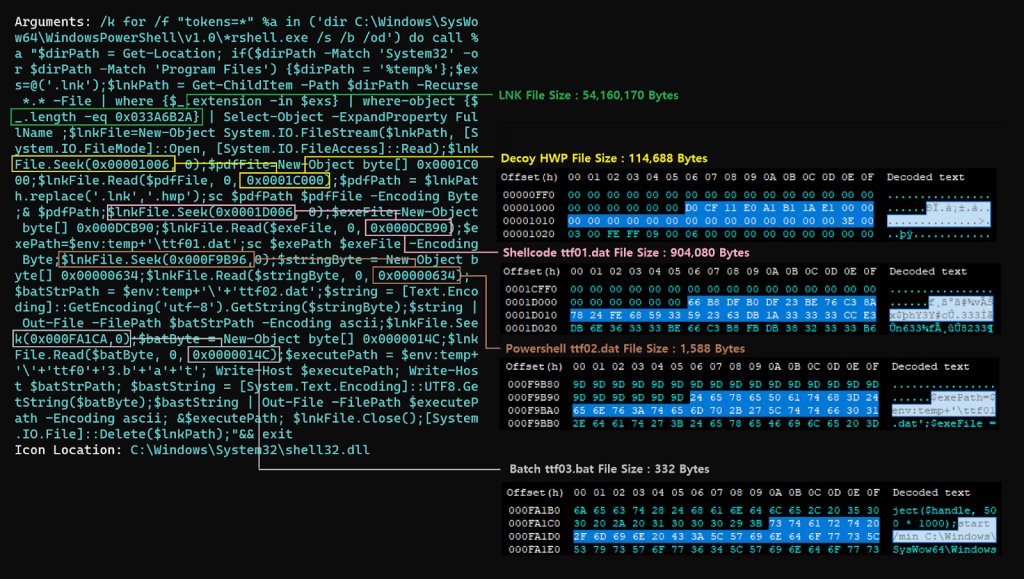
The malware creates temporary files in the %LOCALAPPDATA% directory as ‘version1.0.tmp’ before executing through rundll32.exe, making detection even more challenging.
Fileless Attacks and Cloud-Based Command Centers
Beyond steganography, APT37 has implemented fileless attack techniques that operate entirely in computer memory, leaving minimal traces on infected systems.
The malware injects shellcode into legitimate Windows processes like mspaint.exe and notepad.exe, allowing it to hide within normal system operations.
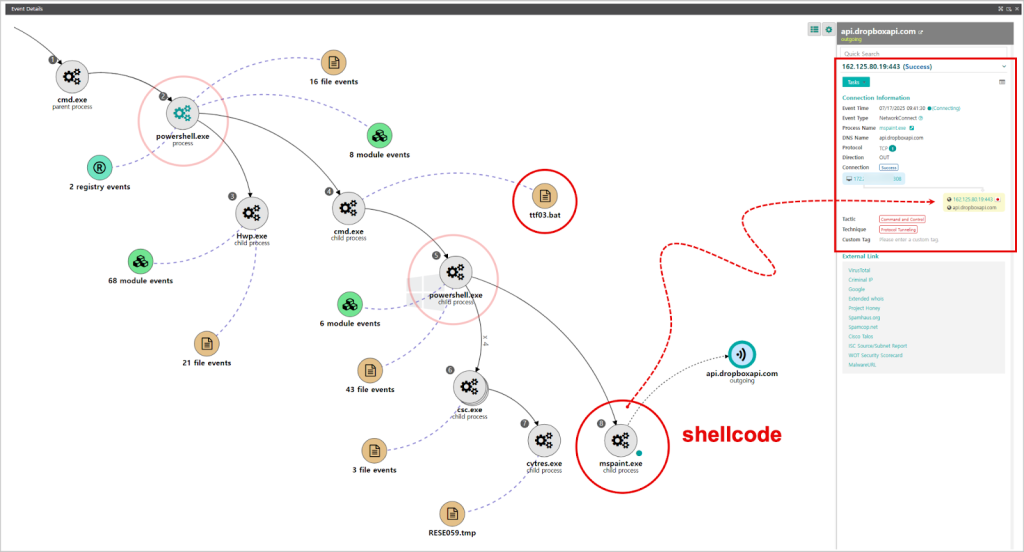
The group continues exploiting legitimate cloud services for command and control operations, using platforms including Dropbox, Yandex Disk, and pCloud.
Investigators discovered multiple access tokens linked to email addresses registered with Russian-based Yandex services, highlighting the international infrastructure supporting these operations.
Recent variants target South Korean organizations using social engineering themes related to North Korean defectors and national security topics.
The attackers distribute compressed files containing malicious shortcuts that appear to be legitimate documents but trigger complex infection chains when opened.
Security experts emphasize that traditional antivirus solutions prove inadequate against these advanced techniques.
Organizations require Endpoint Detection and Response (EDR) systems capable of monitoring behavioral patterns and detecting anomalous process activities in real-time.
The discovery underscores the escalating sophistication of state-sponsored cyber operations and the critical need for advanced security measures.
As attackers continue to evolve their methods, cybersecurity professionals must adapt their defensive strategies to address emerging steganographic and fileless attack vectors that blur the lines between legitimate files and malicious threats.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates