A comprehensive white paper presented at Virus Bulletin 2025 reveals the intricate operations of DeceptiveDevelopment, a North Korea-aligned threat actor that collaborates with fraudulent IT workers to compromise organizations worldwide.
The campaign represents a hybrid threat combining cybercrime with employment fraud, targeting software developers through elaborate social engineering schemes.
Deceptive development operators pose as recruiters on platforms like LinkedIn, Upwork, and Freelancer, offering lucrative job opportunities to unsuspecting developers.
Victims receive coding challenges or pre-interview tasks requiring them to download projects from private GitHub, GitLab, or Bitbucket repositories. These repositories contain trojanized code, often hidden in lengthy comments beyond the visible edge of code browsers.
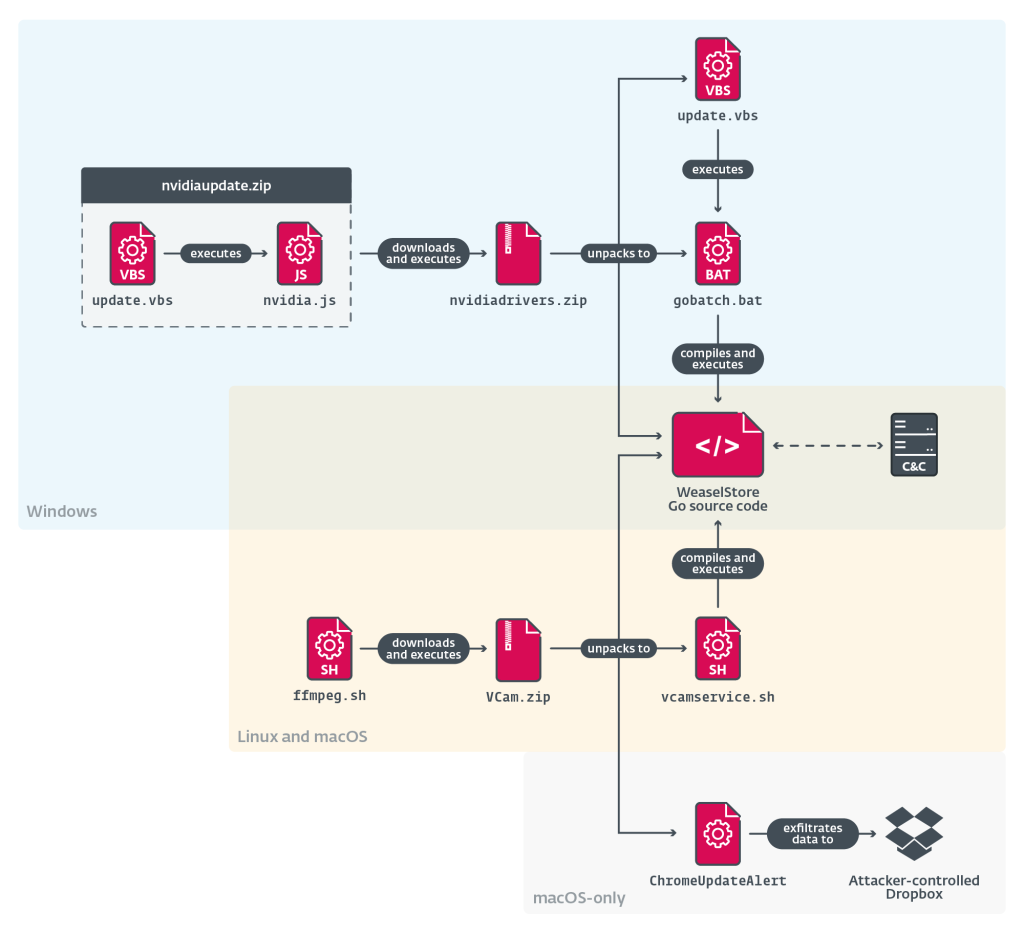
The group’s multiplatform toolset includes several sophisticated malware families. BeaverTail, an obfuscated infostealer written in JavaScript and C++, serves as the initial payload, collecting data from cryptocurrency wallets, browser credentials, and keychains.
This first-stage malware downloads InvisibleFerret, a modular Python-based RAT featuring browser data theft, remote access capabilities, clipboard logging, and AnyDesk deployment modules.
Recent campaigns have introduced WeaselStore, a Go-based multiplatform infostealer also known as GolangGhost, which uniquely delivers source code along with Go environment binaries to compile and execute across Windows, Linux, and macOS systems.
The most advanced toolkit, TsunamiKit, centers around a .NET backdoor, with components including TsunamiLoader, TsunamiInjector, and TsunamiClient, capable of deploying cryptocurrency miners such as XMRig and NBMiner.
Advanced Social Engineering Incorporates ClickFix Techniques
The threat actors have evolved their tactics to include ClickFix social engineering, directing victims to fake job interview websites with elaborate application forms.
After investing significant time completing detailed questionnaires, victims encounter camera access errors with “How to fix” links. These links provide operating system-specific terminal commands that download and execute malware, rather than resolving technical issues.
Security researchers have identified connections between DeceptiveDevelopment’s advanced backdoors, including Tropidoor and AkdoorTea, with established North Korean APT tools, such as PostNapTea, from Lazarus operations.
Code analysis reveals shared encryption methods, API resolution techniques, and command structures, suggesting collaboration or tool sharing between different North Korean cyber units.
The campaign’s connection to North Korean IT worker fraud operations creates additional risks for employers. These workers use stolen identities obtained by DeceptiveDevelopment to secure legitimate remote positions, employing AI-generated profile photos, synthetic identities, and proxy interviewers.
Internal documents reveal that teams led by coordinators set quotas and manage daily schedules of 10-16 hours, targeting European markets, including France, Poland, and Ukraine.
This hybrid approach, combining traditional cybercrime with employment fraud, represents an evolution in North Korean cyber operations, demonstrating how threat actors leverage multiple attack vectors simultaneously.
Organizations must implement comprehensive security measures covering both technical defenses and hiring verification processes to combat these sophisticated, multifaceted campaigns targeting the global technology workforce.
IoCs
Files
A comprehensive list of indicators of compromise (IoCs) and samples can be found in our GitHub repository.
| SHA-1 | Filename | Detection | Description |
| E34A43ACEF5AF1E5197D940B94FC37BC4EFF0B2A | nvidiadrivers.zip | WinGo/DeceptiveDevelopment.F | A trojanized project containing WeaselStore. |
| 3405469811BAE511E62CB0A4062AADB523CAD263 | VCam1.update | WinGo/DeceptiveDevelopment.F | A trojanized project containing WeaselStore. |
| C0BAA450C5F3B6AACDE2807642222F6D22D5B4BB | VCam2.update | WinGo/DeceptiveDevelopment.F | A trojanized project containing WeaselStore. |
| DAFB44DA364926BDAFC72D72DBD9DD728067EFBD | nvidia.js | JS/Spy.DeceptiveDevelopment.Q | WeaselStore downloader for Windows. |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates