In a new advisory, Proofpoint researchers have revealed a concerning technique that enables threat actors to sustain unauthorized access to cloud environments through malicious OAuth applications, even after user credentials are reset or multifactor authentication (MFA) is enforced.
The discovery highlights the growing sophistication of account takeover (ATO) campaigns targeting enterprise cloud infrastructures.
Malicious OAuth applications exploit inherent trust within cloud ecosystems such as Microsoft Entra ID. Attackers first compromise user accounts through phishing or reverse-proxy toolkits designed to capture credentials and session cookies.
Once inside, they create internal “second-party” OAuth applications that appear as legitimate enterprise apps, configure sensitive permission scopes such as Mail.Read and offline_access, and generate cryptographic client secrets.
These secrets act as long-lived credentials, granting continuous API-level access to resources including mailboxes, SharePoint files, Teams messages, and calendars.
Proofpoint’s researchers developed a dedicated proof-of-concept (PoC) tool to simulate how these threats operate. The tool automates the registration, configuration, and authorization of internal OAuth applications under compromised accounts.
After password resets, the researchers confirmed that the malicious applications retained functionality by generating new tokens and successfully accessing the victim’s mailbox, demonstrating complete independence from user credentials or MFA enforcement.
Because these rogue apps appear as standard internal registrations in the Entra ID portal, they often evade security scans and remain active for months or longer, depending on the validity of the client secret.
Real-World Exploitation and Persistence
Proofpoint telemetry confirmed that attackers have begun using this method in real-world incidents. One monitored case involved a four-day ATO campaign leveraging the Tycoon phishing kit.
The adversary, operating via U.S.-based VPN proxies, created a malicious internal app named “test” and assigned it Mail.Read and offline_access permissions. Even after the victim reset their password, the application continued accessing mailbox data until manual intervention occurred.
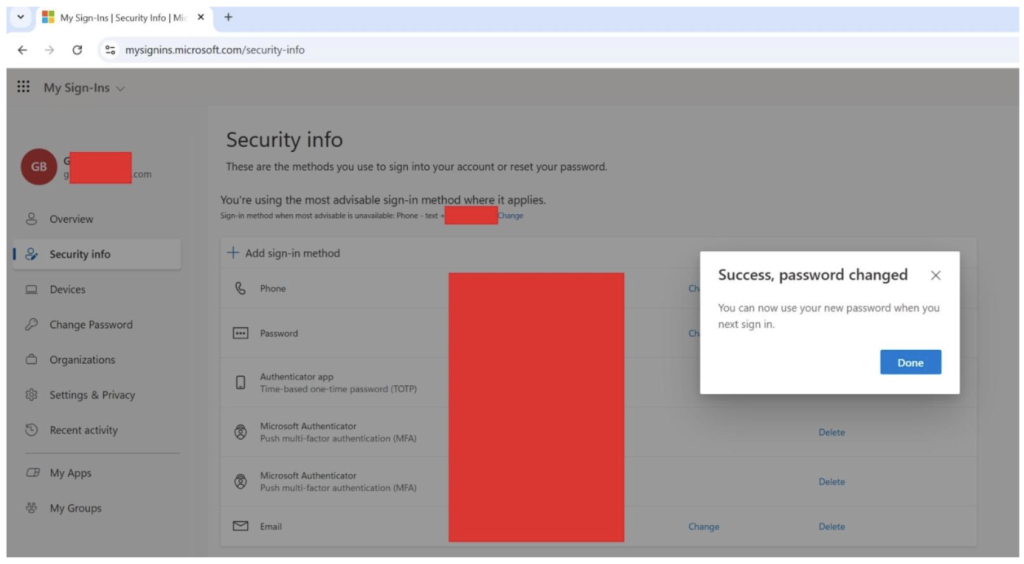
This persistence stems from the OAuth trust model itself. Since application secrets and refresh tokens remain valid until explicitly revoked, password resets or token expirations do not immediately terminate access.
The only guaranteed mitigation involves removing the malicious application, revoking all tokens and secrets, and deleting associated service principals within Entra ID.
Proofpoint urges organizations to adopt continuous OAuth monitoring, enforce strict app consent policies, and regularly audit registered applications.
Security teams should prioritize the detection of anomalous internal app registrations, unexpected permission requests, and behavioral indicators of OAuth abuse.
Training employees to identify suspicious consent prompts and unauthorized OAuth authorizations remains essential to preventing long-term cloud compromise.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates