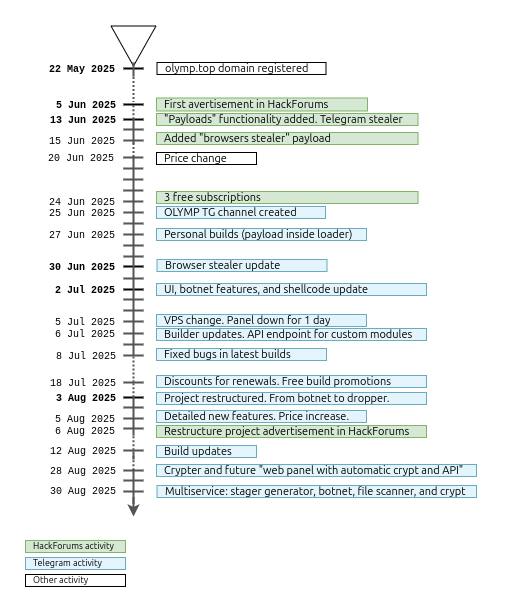
Olymp Loader, a Malware-as-a-Service (MaaS) offering from the threat actor collective “OLYMPO,” has quickly become a favored tool among low- and mid-tier cybercriminals since its first appearance on June 5, 2025.
Promoted as entirely written in assembly language and marketed as FUD (Fully UnDetectable), the loader combines rapid feature updates with integrated stealer modules, aggressive defense evasion, and automatic certificate signing to lower the barrier for commodity intrusions.
Evolution from Botnet Concept to Crypter-Focused Loader
The project initially launched under the name “Olymp Botnet,” with a centralized command-and-control panel accessible via olympl[.]top.
Early development focused on establishing a bot network, but following the departure of their web developer, the team removed all C2 functionality and rebranded the tool as Olymp Loader.
Client feedback overwhelmingly pointed to the demand for crypter capabilities, prompting a second pivot by early August.

An announcement to the Telegram channel on August 3 detailed the addition of deep XOR encryption, Windows Defender exclusion commands, and automatic certificate signing within the stub itself.
By August 27, OLYMPO staged a publicity stunt on VirusTotal, uploading samples with near-zero detections to reinforce their FUD claims.
A teaser on August 30 hinted at a unified “Olymp Projects” panel, promising a stager generator, file-scanner, and eventual botnet revival alongside the loader and crypter modules.
Advanced Stealer Modules and Flexible Payload Delivery
OLYMPO advertises three built-in stealer modules: browser, Telegram, and crypto-wallet, each embedding a proxy URL marker followed by exfiltration code.
Reverse engineering of the Telegram module (SHA256: 880461fa8d4187…) revealed Python-based logic that locates Telegram session files via registry queries, captures screenshots of all monitors, terminates Telegram processes, and bundles the data into a ZIP for POST delivery.
The browser stealer, compiled with Nuitka and loading a “brsteal.dll” from a temporary directory, targets an expanded list of saved credentials.
Although a pure C++ crypto-wallet stealer sample has yet to surface, its advertised support includes Exodus, Electrum, Atomic, and BitcoinCore.
In the wild, approximately forty-six percent of observed loader deployments delivered LummaC2, thirty-one percent deployed WebRAT (also known as SalatStealer), fifteen percent dropped QasarRAT, and eight percent ran Raccoon stealer.
On occasion, operators choose the integrated browser module instead of a third-party RAT, demonstrating confidence in OLYMPO’s own code.
Automated Pricing Tiers and Aggressive Evasion Techniques
OLYMPO’s Telegram channel lists tiered pricing that scales with customization and exclusivity. A classic stub at $50 guarantees Defender bypass, optional Defender removal functionality, single-use VirusTotal certification, and automatic certificate signing.
For one hundred dollars, buyers receive shellcode tailored to their specifications, and for two hundred dollars, OLYMPO will inject unique stub code into a legitimate program of the client’s choice.
Each build supports 32- and 64-bit architectures, as well as .NET and Java payloads, with binaries ranging from 12 to 70 megabytes, depending on the host executable.
Persistence is established via cmd.exe or PowerShell scripts that copy the loader to %AppData% or %Startup%, while an aggressive UAC-Flood elevates privileges.
To evade detection, the loader adds itself to Windows Defender exclusions, leverages custom machine-learning bypass techniques, and employs deep XOR obfuscation for both modules and payloads.
As Olymp Loader’s feature set and marketing continue to evolve, defenders must monitor underground discussions, sandbox behaviors, and API endpoints to anticipate its following developments and mitigate the growing threat.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates