Cybersecurity researchers at Silent Push have uncovered a sophisticated campaign in which threat actors are exploiting AdaptixC2, an open-source Command and Control framework designed initially for legitimate penetration testing, to deploy malicious payloads across global ransomware operations.
The investigation reveals strong connections to Russia and the Russian criminal underworld, with the framework being actively weaponized since August 2025.
AdaptixC2 represents a new generation of extensible post-exploitation and adversarial emulation frameworks available freely on GitHub.
Built with flexibility in mind, the framework features a server component written in Golang and a GUI client developed in C++ and Qt, enabling cross-platform compatibility across Linux, Windows, and macOS.
While designed for security researchers and red teams conducting authorized penetration testing, the tool has been increasingly adopted by cybercriminals for nefarious purposes.
Discovery and Attribution
Silent Push threat analysts first identified malicious AdaptixC2 activity during their investigation into CountLoader, a newly emerged malware loader.
The research team traced malicious AdaptixC2 payloads being served from attacker infrastructure at IP address 64.137.9.118, which utilized the CountLoader malware as a delivery mechanism.
This discovery prompted the development of specialized detection signatures to identify both CountLoader and AdaptixC2 infrastructure, providing comprehensive threat coverage.
The investigation led researchers to identify a potential threat actor operating under the handle “RalfHacker,” who appears to be the primary developer behind the AdaptixC2 framework.
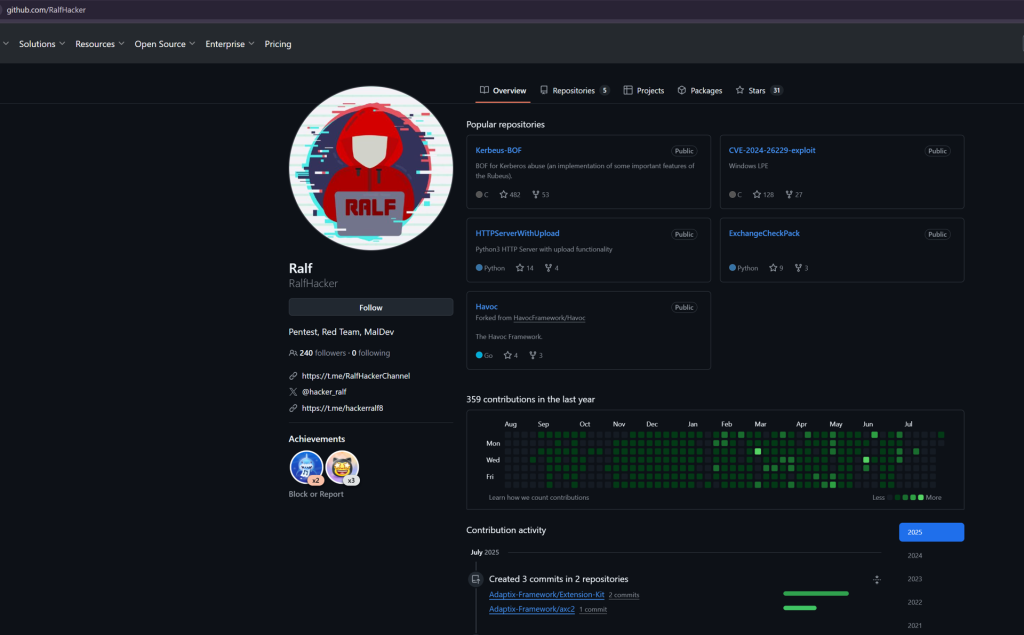
Analysis of GitHub commit history revealed RalfHacker as the most active contributor to the project repository. The individual’s GitHub profile openly identifies them as a penetration tester, red team operator, and, notably, a malware developer.
Through open-source intelligence gathering, Silent Push recovered email addresses associated with RalfHacker’s GitHub accounts, including [email protected] and an older address, [email protected].
The latter email was confirmed to appear in leaked databases from known hacking forums. Further investigation uncovered Russian-language Telegram channels managed by RalfHacker, including a group that advertised AdaptixC2 version 0.6 updates, using Russian hashtags related to Active Directory exploitation and Advanced Persistent Threat materials.
Ransomware Campaign Connections
The abuse of AdaptixC2 has been directly linked to Akira ransomware operations. According to recent DFIR reports, Akira ransomware affiliates have actively employed the framework in their attack chains.
Since March 2023, Akira ransomware has compromised over 250 organizations across North America, Europe, and Australia, generating approximately $ 42 million in ransom payments, according to CISA bulletins.
Silent Push researchers assess with moderate confidence that the ties between RalfHacker and malicious AdaptixC2 campaigns warrant continued monitoring, particularly given the framework’s predominant use by Russian threat actors and its marketing through Russian underground channels.
The research highlights the ongoing challenge of distinguishing legitimate security tools from their criminal exploitation, as threat actors frequently disguise malicious activities under the guise of ethical hacking and red teaming.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates