The Socket Threat Research Team uncovered a marked escalation in the weaponization of open source packages.
Threat actors are embedding sophisticated malware-including infostealers, remote shells, and automated cryptocurrency drainers-deep within the software supply chain by exploiting trusted package registries.
This wave of supply chain attacks leverages both automation and artificial intelligence, enabling adversaries to rapidly adapt, bypass traditional defenses, and persist within developer environments.
Threat Actors Exploit Package Registries
Open source software now forms the backbone of most modern applications. With ecosystems like npm (Node.js), PyPI (Python), Maven Central (Java), and RubyGems, developers build quickly by assembling prebuilt modules.
This agility, however, comes at a significant risk: 70–90% of a typical codebase may consist of third-party dependencies, creating implicit trust relationships ripe for exploitation.
The dependency graphs of popular packages reveal a complex web where a single update can introduce dozens of transitive dependencies, each representing a potential entry point for attackers.
The threat landscape is evolving in tandem with the tools developers use. In addition to leveraging automation, attackers are now using AI to create and publish malicious look-alike packages at scale, obfuscate their payloads, and even inject misleading comments to evade static analysis.
These advances have greatly increased both the volume and sophistication of attacks observed in public registries.
Evolving Techniques Undermining Supply Chain Security
The Socket team has identified a set of recurring adversarial techniques employed across major open source ecosystems:
The first technique, typosquatting, involves registering packages with names mimicking popular libraries-differing by just one character.
This exploits both human error and the overconfidence of code-assist AI tools. A single mistyped import can allow attackers to harvest credentials or exfiltrate sensitive data, as seen in recent PyPI incidents.
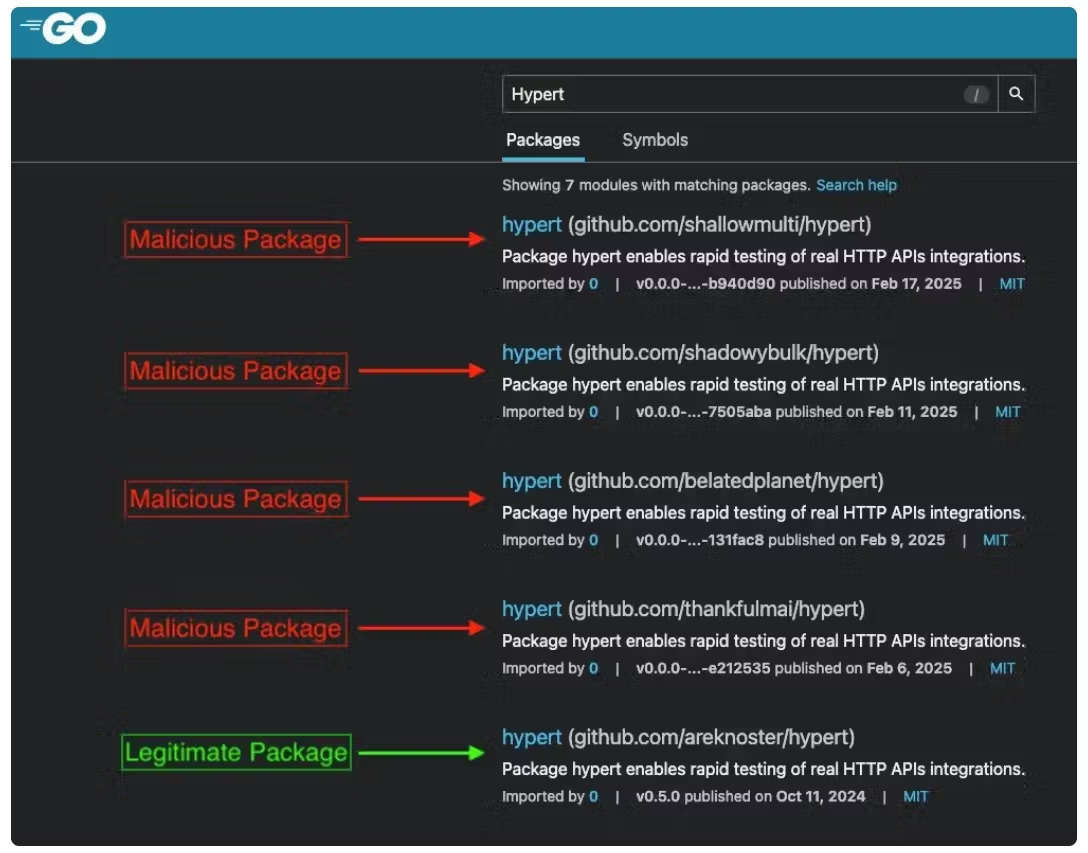
Repository and caching abuse is another vector, notably exploited in the Go ecosystem.
Attackers have backdoored clones of legitimate modules, relying on caching mechanisms like the Go Module Mirror to serve malicious payloads long after the original repository has been restored, enabling remote code execution and persistent threats.
Obfuscation is a core tactic, with malicious actors employing random variable names, dense minification, and encoded payloads to hide intent and evade scanner detection.
Obfuscated install scripts, often packed with Base64 or hex-encoded logic, are particularly effective against signature-based defenses.
Multi-stage malware further enhances stealth. Attackers deploy small, seemingly benign packages that download additional payloads post-installation.
Notably, a campaign linked to North Korean actors used this method to first harvest browser and wallet data before deploying a robust backdoor in a delayed stage, reducing the chances of immediate detection.
Automation and AI now play a pivotal role, dramatically increasing scale and speed.
Attackers use machine learning models to generate hundreds of unique, obfuscated malicious packages.
Furthermore, “slopsquatting”-registering hallucinated package names suggested by overconfident AI code assistants-has emerged as a fast-growing threat, especially as search engines and AI platforms occasionally recommend these packages by mistake.
Lastly, weaponizing legitimate services has become a favored evasion tactic. Malicious code increasingly exfiltrates data using trusted platforms like Gmail, Discord, and SaaS telemetry APIs, blending malicious activity with normal network traffic.

In some cases, standard developer libraries such as nodemailer or official error tracking tools are repurposed to send stolen credentials or impersonate legitimate error reporting.
In response, security experts recommend a multi-layered approach: automate checks for lookalike package names, analyze the actual contents of installed packages (not just source repositories), and monitor for suspicious install-time networking or downloader behavior.
Treat obfuscation as a red flag, and integrate static and behavioral scans into CI pipelines.
Critically, avoid blanket allowlisting of trusted domains, and actively monitor outbound connections-even if they target popular platforms or legitimate services.
As the open source ecosystem continues to expand and AI-powered development tools proliferate, the threat surface will only grow.
Sustained vigilance, automation, and robust package scrutiny are essential if organizations are to safeguard their software supply chains against increasingly sophisticated adversaries.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates