A team of cybersecurity researchers from multiple German institutions has disclosed a sophisticated new attack called “Opossum” that can compromise the integrity of secure TLS connections across multiple internet protocols.
The cross-protocol application layer desynchronization attack, developed by researchers from Technology Innovation Institute (TII), Ruhr University Bochum (RUB), and University of Paderborn (UPB), demonstrates how attackers can inject unexpected messages into encrypted communications, causing clients and servers to become desynchronized even when existing security countermeasures are in place.
Wide-Ranging Impact Across Common Internet Protocols
The Opossum attack represents a significant advancement in TLS-based vulnerabilities, affecting a broad spectrum of application protocols that millions of users rely on daily.
The attack specifically targets protocols that support both opportunistic TLS and implicit TLS connections, including HTTP, FTP, POP3, SMTP, LMTP, and NNTP.
This dual-support requirement creates a critical vulnerability window that attackers can exploit to break the fundamental security assumptions of encrypted communications.
Unlike traditional attacks that focus on cryptographic weaknesses, Opossum exploits subtle differences in how applications handle implicit TLS connections (where encryption is established immediately on dedicated ports) versus opportunistic TLS connections (where connections begin in plaintext and upgrade to encryption).
The attack builds upon previous research into the ALPACA vulnerability, demonstrating that even with current countermeasures in place, sophisticated attackers can still manipulate TLS authentication mechanisms to achieve their goals.
Advanced Man-in-the-Middle Exploitation Technique
The technical execution of the Opossum attack reveals a sophisticated understanding of protocol-level vulnerabilities that require precise timing and network positioning.
Attackers must establish a man-in-the-middle position to intercept client connections intended for implicit TLS services, such as HTTPS on port 443.
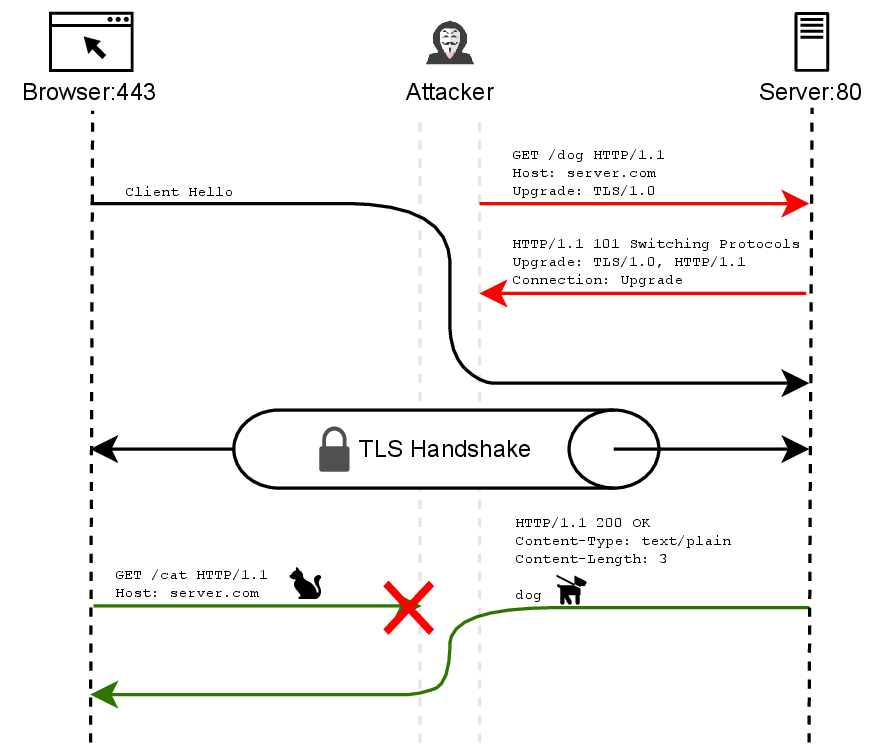
The attacker then creates their plaintext connection to the server’s opportunistic TLS port, sends malicious requests with TLS upgrade headers, and forwards the client’s connection as if it were part of their session.
The most concerning aspect of this attack is its persistence and practical impact on real-world communications.
Once the initial desynchronization occurs, the effect continues for all subsequent requests in the connection, potentially allowing attackers to manipulate responses to client requests.
The researchers demonstrated this capability by showing how a client requesting one resource could receive completely different content, fundamentally breaking the trust relationship between client and server that forms the foundation of secure internet communications.
Implications for Internet Security
The disclosure of the Opossum attack underscores the ongoing challenges in securing internet protocols and the need for comprehensive security assessments that consider cross-protocol interactions and implementation differences across various TLS deployment scenarios.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates