Security researchers have identified a sophisticated phishing technique where threat actors embed invisible Unicode characters directly into email subject lines to evade automated detection systems.
This evolution of a well-documented evasion method marks a concerning escalation in phishing campaigns targeting organizations worldwide.
The technique involves inserting soft hyphen characters (Unicode code point U+00AD) between individual letters in email subject lines using the MIME encoded-word format specified in RFC 2047.
When displayed in email clients like Microsoft Outlook, these invisible characters remain hidden from recipients while breaking up keywords that security solutions typically flag as suspicious.
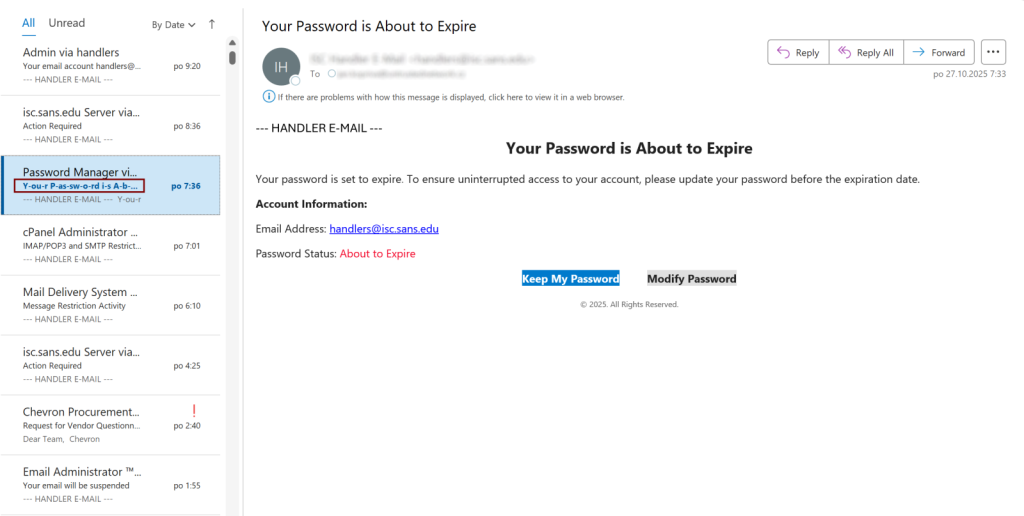
A recently analyzed phishing message demonstrated this approach, with its subject line encoded as “=?UTF-8?B?WcKtb3XCrXIgUMKtYXPCrXN3wq1vwq1yZCBpwq1zIEHCrWLCrW91dCA=?=” and “=?UTF-8?B?dMKtbyBFwq14wq1wwq1pcsKtZQ==?=” which decoded to “Your Password is About to Expire” with soft hyphens inserted between each character.
Technical Implementation Details
The attackers leveraged the MIME encoded-word format, which uses the structure “=?charset?encoding?encoded-text?=” to transmit non-ASCII characters in email headers.
By encoding the subject line in UTF-8 and Base64, they successfully embedded soft hyphen characters throughout the text.
This character, commonly represented as the “” HTML entity, functions as a formatting control character that typically remains invisible in most email clients unless text wrapping forces a line break.
Microsoft Threat Intelligence previously documented the use of invisible Unicode characters in email body content since at least 2021, noting that “attackers inserted invisible Unicode characters to break up keywords in an email body or subject line in an attempt to bypass detection”.
However, the application of this technique specifically to subject lines remains relatively uncommon and less documented than its use in message bodies.
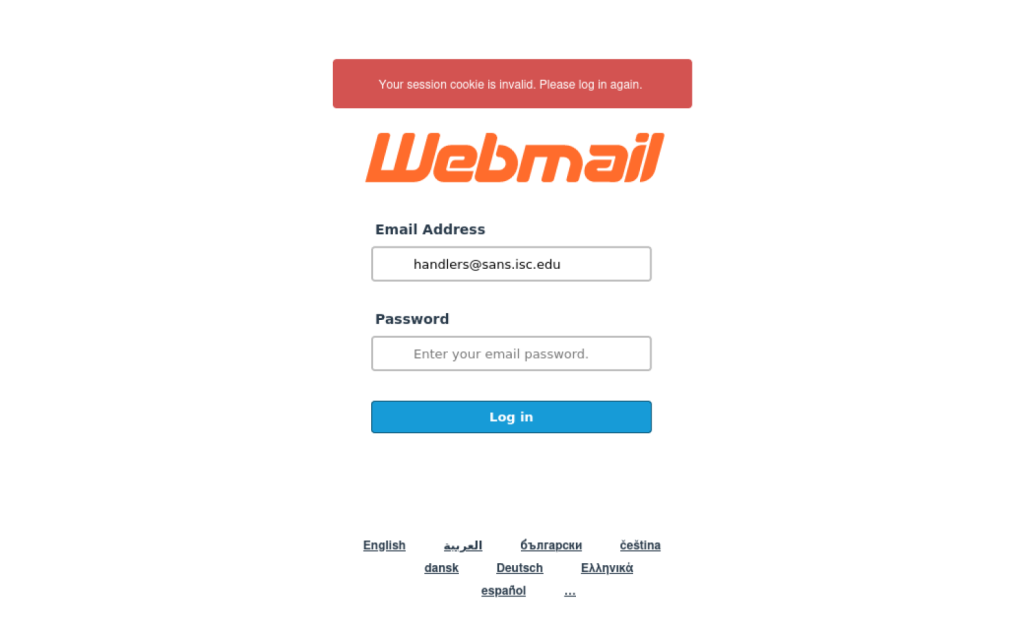
The analyzed phishing email also contained soft hyphens throughout its body, demonstrating a comprehensive evasion strategy across multiple message components.
The phishing message directed victims to a credential-harvesting page hosted on a compromised domain, presenting a generic webmail login interface designed to capture authentication credentials.
This multi-layered approach, combining subject line obfuscation, body content manipulation, and social engineering, represents an evolution in phishing sophistication that challenges traditional email security filtering mechanisms.
Security professionals should update detection rules to identify MIME-encoded words containing excessive soft hyphens or other invisible Unicode characters in subject lines, and implement advanced content analysis that decodes encoded headers before applying filtering logic.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates