Cyble Research and Intelligence Labs (CRIL) has uncovered a large-scale phishing campaign exploiting HTML attachments to steal credentials while avoiding traditional email security mechanisms.
Instead of directing victims to malicious URLs, the attackers embed JavaScript within self-contained HTML files distributed via email.
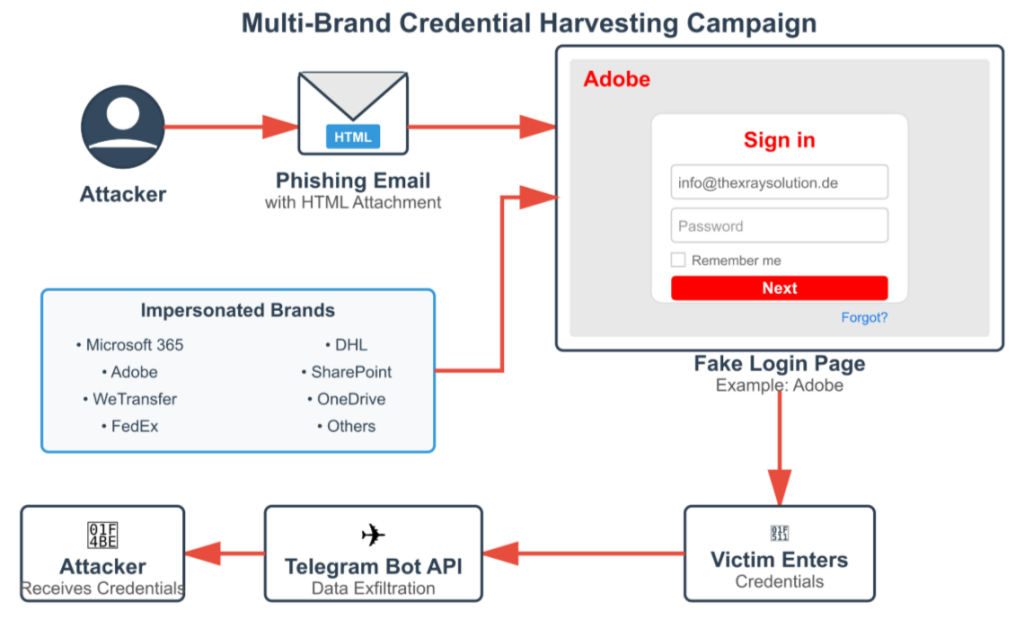
These attachments convincingly impersonate Adobe or Microsoft login pages and steal credentials directly, which are then transmitted to attacker-controlled Telegram bots through the Telegram Bot API.
The phishing emails typically mimic business-related communication, such as requests for quotations (RFQs) or invoices, using RFC-compliant filenames like RFQ_4460-INQUIRY.HTML. When opened, the HTML file loads a blurred background image of a fake invoice with a central login prompt.
Once the victim enters their credentials, the embedded JavaScript constructs a message payload and sends it through a POST request to api.telegram.org/bot<BotToken>/sendMessage. To appear legitimate, the page then displays an “invalid login” message before redirecting to the real Adobe website.
Technical Analysis and Evolving Tactics
CRIL examined multiple samples and identified two main variants. One leverages CryptoJS AES encryption (key 8525965283890, iv 4842043763) to obfuscate its logic and collect email, password, IP address, and user agent data via external services like api.ipify.org and ip-api.com.
The second version adopts the modern Fetch API for data exfiltration and includes anti-forensics measures that block developer tools, disabling F12, right-click actions, and text selection to hinder analysis.
Both variants use unique Telegram bot tokens and chat IDs to deliver stolen data directly to their operators. CRIL uncovered a network of active bots with names such as garclogtools_bot, v8one_bot, and dollsman_bot, linked to accounts including Rharfel and joedollar23telegram.
The operation spans multiple Telegram ecosystems and likely involves several independent threat actors reusing shared templates or toolkits.
Global Brand Impersonation and Regional Targeting
The campaign leverages multiple global and regional brands to improve its success rate. Impersonated brands include Adobe, Microsoft, WeTransfer, DocuSign, FedEx, DHL, and telecommunications providers such as Telekom Deutschland.
Many HTML samples display consistent design elements and language localization, indicating automated template generation.
CRIL noted heavy targeting of Central and Eastern Europe, particularly the Czech Republic, Slovakia, Hungary, and Germany, across industries such as manufacturing, education, energy, and government.
The phishing operation continues to evolve with advanced obfuscation, multilingual support, and anti-analysis defenses.
CRIL advises blocking Telegram API traffic from corporate endpoints, enhancing endpoint content inspection for HTML attachments, and monitoring for unusual POST requests to api.telegram.org.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates