A major phishing campaign is targeting LastPass users by impersonating urgent security alerts, attempting to trick recipients into downloading malicious software.
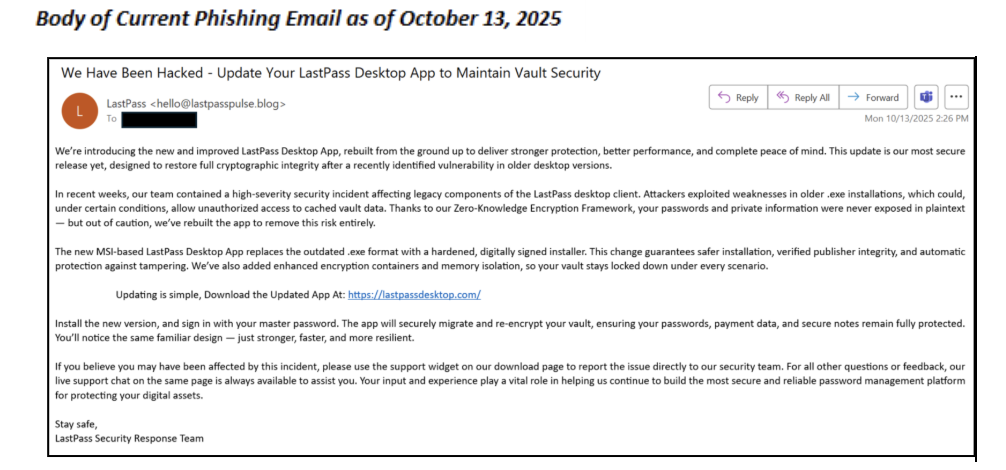
Security experts have identified a series of deceptive emails sent from addresses such as “hello@lastpasspulse[.]blog” and “hello@lastpassgazette[.]blog,” with subject lines warning, “We Have Been Hacked – Update Your LastPass Desktop App to Maintain Vault Security.”
Despite what the message claims, LastPass’s security team confirms that no breach has occurred this is a socially engineered ruse designed to accelerate victim response and maximize the impact of malware spread.
Phishing Campaign Masquerades as ‘LastPass Hack’ Alert to Spread Malware
The phishing emails direct users to malicious domains, including “lastpassdesktop[.]com” and “lastpassgazette[.]blog,” both now flagged by Cloudflare as active phishing sites.
A closely related site, “lastpassdesktop[.]app,” registered by the threat actors, signals possible future campaign variants. The sites host phishing pages under IP addresses 172.67.147[.]36 and 172.67.219[.]2, with another, 84.32.84[.]32, tied to “lastpassgazette[.]blog.”
Investigators have also linked the sites to a bulletproof hosting provider, NICENIC a known facilitator for cybercriminal infrastructure.
Technical analysis of the email headers shows the threat actors using aggressive obfuscation tactics. Forged sender names such as “LastPass hello@lastpasspulse[.]blog” and reply-to addresses matching the same fake domains reinforce the illusion of legitimacy.
Associated IPs 148.222.54[.]15 and 23.83.222[.]47 have also been flagged in connection with recent malicious campaigns targeting password managers.
The campaign’s timing, coinciding with the U.S. holiday weekend, appears strategic; threat actors often exploit periods of reduced staffing, hoping security teams will be slower to detect and respond to new activity.
Technical Details and Recommended Response
The phishing sites mimic authentic LastPass branding and prompt users to “update” their desktop app, delivering malware designed to steal credentials and exfiltrate sensitive vault information. Fortunately, Cloudflare has intervened, displaying warnings to would-be victims.
LastPass stresses that it will never ask for a master password or require immediate upgrades via emailed links.
The company urges users to scrutinize all unexpected communications, especially those invoking urgency and fear hallmarks of effective phishing. Suspicious emails should be forwarded to [email protected] for investigation.
The campaign highlights ongoing risks facing password manager users and the continuous evolution of social engineering tactics. Security teams are actively working to take down the phishing domains and neutralize associated infrastructure. Until resolution, vigilance is paramount.
Always verify suspicious emails against official LastPass channels, and never provide credentials in response to unsolicited requests.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates