Security researchers at XLab have uncovered a massive expansion of the PolarEdge botnet infrastructure, revealing more than 25,000 compromised devices and 140 command-and-control servers operating across 40 countries.
The discovery centers on a previously undocumented component, RPX_Client, that transforms vulnerable IoT devices into proxy nodes for cybercriminal operations.
XLab’s Cyber Threat Insight and Analysis System detected the threat on May 30, 2025, when IP address 111.119.223.196 began distributing an ELF file named “w” that received zero detections on VirusTotal.
The file’s clean signature initially suggested PolarEdge operators had launched a new stealth campaign, prompting researchers to conduct extensive correlation analysis that ultimately exposed the RPX_Client component and its role in building Operational Relay Box networks.
Global Scale and Primary Targets
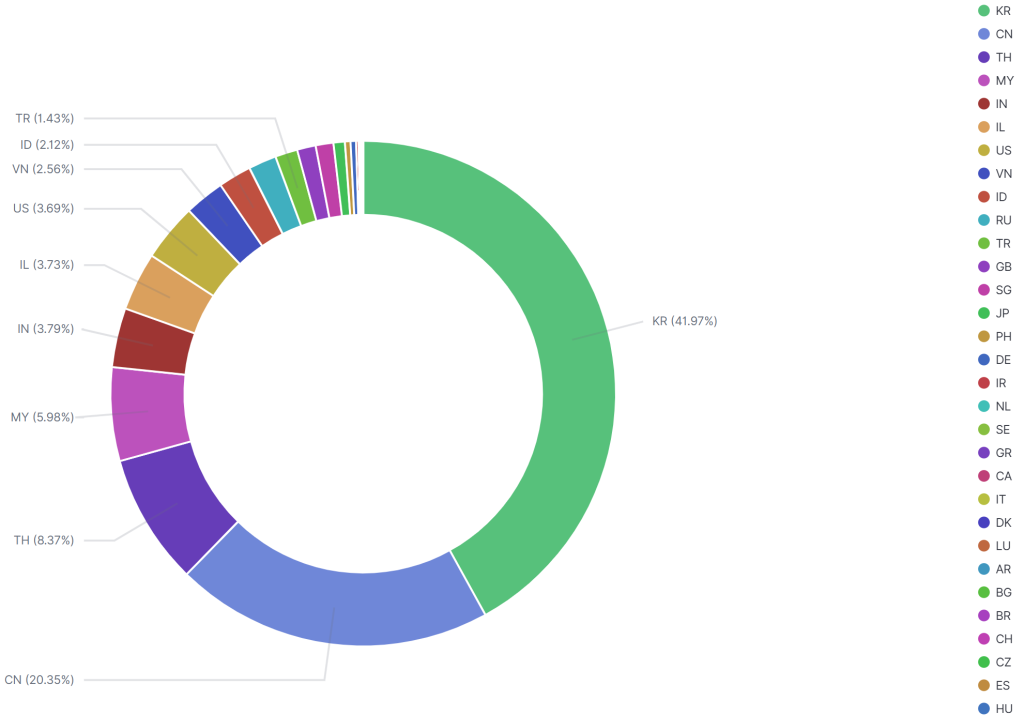
The infected devices span Southeast Asia and North America, with South Korea bearing the heaviest impact at 41.97% of compromised systems, followed by China at 20.35% and Thailand at 8.37%.
Analysis of the device fingerprints reveals that over 90% of infections target KT CCTV surveillance cameras and Shenzhen TVT digital video recorders. However, the malware also compromises Asus routers, Cyberoam UTM appliances, Cisco RV340 VPN routers, D-Link routers, and Uniview webcams.
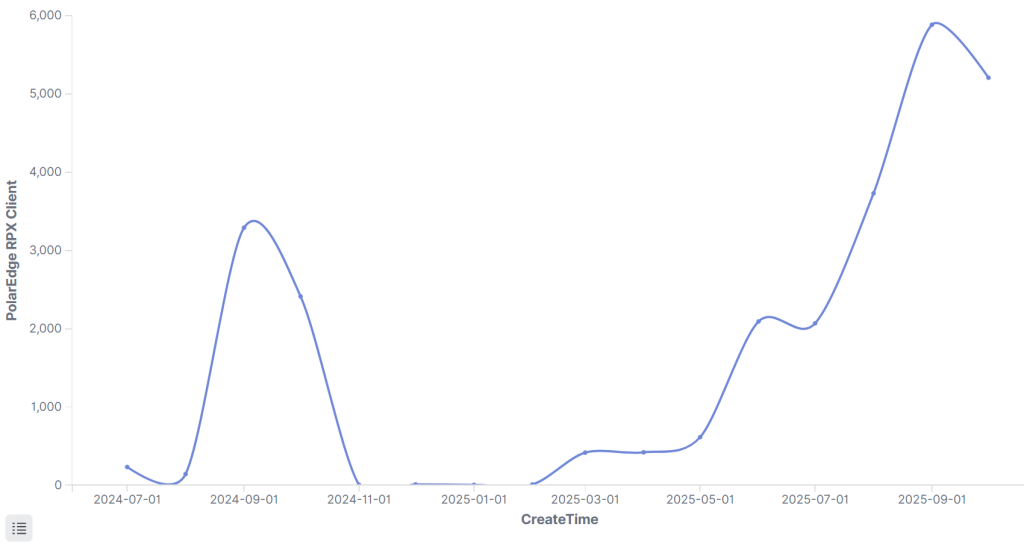
The 140 confirmed RPX_Server nodes operate exclusively on virtual private servers within three autonomous system numbers 45102, 37963, and 132203, and are primarily hosted on Alibaba Cloud and Tencent Cloud infrastructure.
Each server uses port 55555 and shares an identical public PolarSSL test certificate originally from Mbed TLS version 3.4.0, creating a distinctive infrastructure fingerprint that enabled XLab to validate active servers through reverse-engineered communication protocols.
Technical Architecture and Attribution
RPX_Client version 0.0.13 establishes two independent connections to compromise handlers: port 55555 for node registration and traffic proxying through RPX_Server, and port 55560 for remote command execution via Go-Admin.
The malware disguises its process as “connect_server” and enforces single-instance execution through a PID file at /tmp/.msc, while maintaining persistence by injecting itself into the rcS initialization script.
XLab researchers attribute RPX infrastructure to PolarEdge with high confidence based on multiple indicators.
The coding style of propagation scripts matches known PolarEdge samples, and IP 82.118.22.155, which distributed the initial downloader chain in December 2023, resolves to domains with CNAME records pointing to jurgencindy.asuscomm.com, the same host used by Sekoia-disclosed PolarEdge C2 servers icecreand.cc and centrequ.cc.
Database records from captured RPX_Server instances contain distribution logs confirming that 111.119.223.196 delivered RPX_Client payloads, while server logs show the actual execution of infrastructure management commands such as change_pub_ip.
The multi-hop proxy architecture effectively obscures the origins of attacks, with compromised IoT devices serving as the first line of defense and inexpensive VPS nodes providing a secondary layer of obfuscation.
This design significantly complicates attribution efforts and validates Mandiant’s assessment that ORB networks undermine traditional indicator-based detection methodologies.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates