Security researchers have uncovered a new wave of PowerShell-based malware loaders using in-memory execution techniques to evade disk-based security defenses.
The operation, first traced to a suspicious PowerShell script (y1.ps1) found on a Chinese server (IP: 123.207.215.76), highlights how attackers are leveraging reflective code loading and sophisticated obfuscation to quietly deploy post-exploitation frameworks such as Cobalt Strike.
In-Memory Execution
Technical analysis of the y1.ps1 script revealed hallmark features of advanced post-exploitation tooling.
The loader functions as a shellcode dropper, using reflective techniques to dynamically resolve Windows API functions and decrypt embedded shellcode directly in memory.
By avoiding traditional disk writes, these loaders can circumvent endpoint detection and response (EDR) products and static file scanning engines.
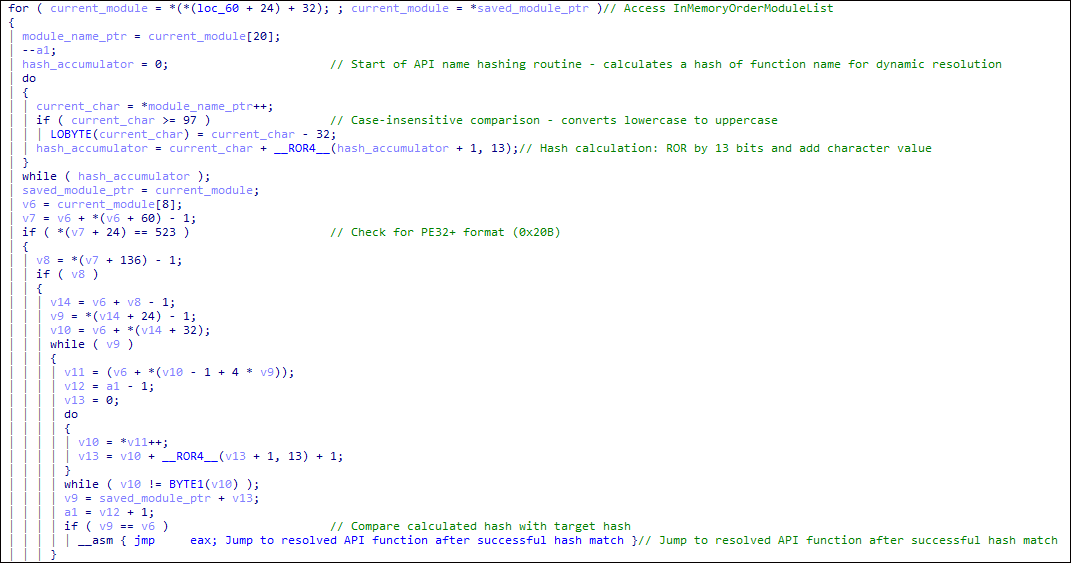
The script, first seen on June 1, 2025, begins by establishing a strict PowerShell execution environment, then employs functions like func_get_proc_address and func_get_delegate_type to access and execute APIs in memory.
The core shellcode is stored as a Base64-encoded byte array, XOR-decrypted at runtime, and executed from a memory region allocated via VirtualAlloc.
This approach enables the malware to operate without leaving a traditional file footprint, complicating forensic efforts.
A notable evasion technique involves API hashing, where function names are obfuscated through hash calculations.
The shellcode traverses the Process Environment Block (PEB), locates critical DLLs (e.g., wininet.dll), and resolves necessary functions by comparing hash values instead of readable API names. This frustrates both static analysis and signature-based detection.
Cobalt Strike Beacon
Upon decryption, the shellcode initiates a covert connection to a second-stage command-and-control (C2) server hosted on Baidu Cloud Function Compute (y2n273y10j.cfc-execute.bj.baidubce.com).
Using the resolved network APIs, it transmits HTTP requests over HTTPS (port 443) with custom User-Agent strings designed to evade network filtering (e.g., “Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; yie9)”).
The downloaded payload is executed in memory using a retry logic, further increasing resilience against interruptions.
Forensic analysis linked the C2 communications to a known Cobalt Strike Beacon infrastructure in Russia (IP: 46.173.27.142, ASN 198610/Beget LLC), with SSL certificate metadata (“Major Cobalt Strike” as subject, “cobaltstrike” as issuer) confirming toolset provenance.
According to the Report, Researchers traced additional loader distribution across open directories and cloud infrastructure in China, Russia, Singapore, the US, and elsewhere, suggesting a broad staging footprint.
Open certificate datasets corroborated links to hundreds of Cobalt Strike instances, reinforcing concerns about widespread abuse of the framework in both red teaming and criminal campaigns.
To defend against such threats, experts recommend tightening PowerShell usage policies, enabling comprehensive script logging, and monitoring for abnormal memory operations and suspicious User-Agent strings.
Blocking identified IOCs (IPs, domains) and deploying advanced EDR solutions with in-memory detection capabilities are essential.
Additionally, monitoring for SSL certificates referencing “cobaltstrike” can surface related infrastructure.
Organizations should restrict unnecessary scripting tools and educate users to avoid interacting with untrusted web resources.
Indicators of Compromise (IOC)
| Type | Value | Details/Attribution |
|---|---|---|
| PowerShell Script | y1.ps1 | Loader, found on open directory |
| SHA-256 Hashes | See table below | Known malicious loader scripts |
| C2 Domain | y2n273y10j.cfc-execute.bj.baidubce.com | Baidu Cloud Function Compute, second-stage download |
| C2 IP | 46.173.27.142 | Beget LLC, Russia, Cobalt Strike Beacon C2 |
| Open Directory Hosts | 123.207.215.76, 182.92.76.239, 35.240.168.8, etc. (See below for details) | Used for hosting loader scripts |
| SSL Certificate | Subject: “Major Cobalt Strike”; Issuer: “cobaltstrike” | Beacon signature, post-exploitation infrastructure |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates