A new Python-based remote-access trojan (RAT), identified by Netskope researchers, has emerged targeting gamers through a malicious impersonation of the “Nursultan Client,” a legitimate Minecraft application popular among Eastern European users.
This multifunctional malware uses the Telegram Bot API as its command-and-control (C2) channel, enabling attackers to exfiltrate data and remotely interact with victim systems across Windows, Linux, and macOS platforms.
Malware Deception and Capabilities
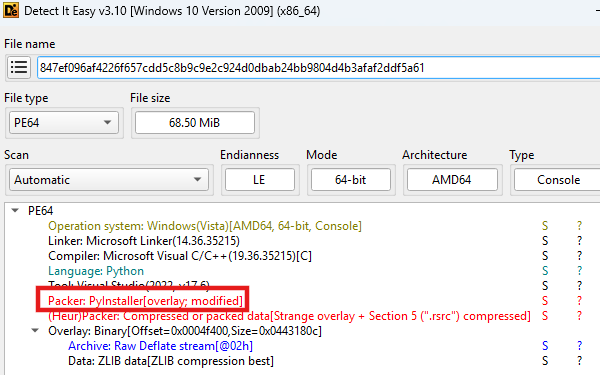
Disguised under the name “Nursultan Client,” the malware presents fake installation screens and registers deceptive startup keys in the Windows registry to appear as legitimate gaming software.
However, the persistence mechanism is poorly implemented, failing to survive system reboots due to incorrect path handling in its PyInstaller-based executable.
The trojan’s Telegram-based C2 design allows attackers to control infected systems via bot commands. Hardcoded credentials within the malware include a Telegram Bot Token and a single authorized user ID, ensuring that only a specific attacker can manage compromised devices.
Through this channel, the RAT supports multiple functionalities, including system reconnaissance, data theft, and remote surveillance.
A key focus of the malware is the theft of Discord authentication tokens. By scanning local storage and browser directories, including Chrome, Edge, Firefox, Opera, and Brave, the RAT identifies and exfiltrates tokens, providing attackers with unauthorized access to victims’ Discord accounts.
It also executes the “/info” command to gather extensive system information, including hardware specifications, OS details, and both local and public IP addresses, all of which are sent back to the attacker in Russian-formatted reports signed “by fifetka.”
Telegram C2 and Surveillance Functions
The RAT’s surveillance capabilities include commands such as “/screenshot” to capture desktop snapshots and “/camera” to activate the webcam.
These images are transmitted through the Telegram API, which further blurs detection boundaries because the traffic appears to involve legitimate encrypted communication with Telegram servers.
The malware also contains adware-type features: when it receives messages containing URLs or images, it displays them on the victim’s system, enabling phishing, fake alerts, or intrusive advertisements.
Researchers conclude that the malware is likely part of a developing Malware-as-a-Service (MaaS) ecosystem. Each build can be customized for different buyers by changing the authorized Telegram ID.
Despite its extensive toolkit, the RAT’s flawed persistence and lack of obfuscation suggest a mid-level actor relying heavily on open-source components rather than advanced coding.
Netskope’s Advanced Threat Protection detects this threat under the signature QD:Trojan.GenericKDQ.F8A018F2A0, emphasizing the need for organizations to monitor legitimate encrypted traffic for hidden C2 communications that exploit platforms like Telegram.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates