The Qilin ransomware group has once again dominated the cyberthreat landscape in July 2025, claiming 73 victims and accounting for 17% of the month’s total ransomware incidents.
This marks the third time in four months that the Russian-tied cybercriminal organization has topped global ransomware activity charts, capitalizing on the operational disruption of former leader RansomHub since April.
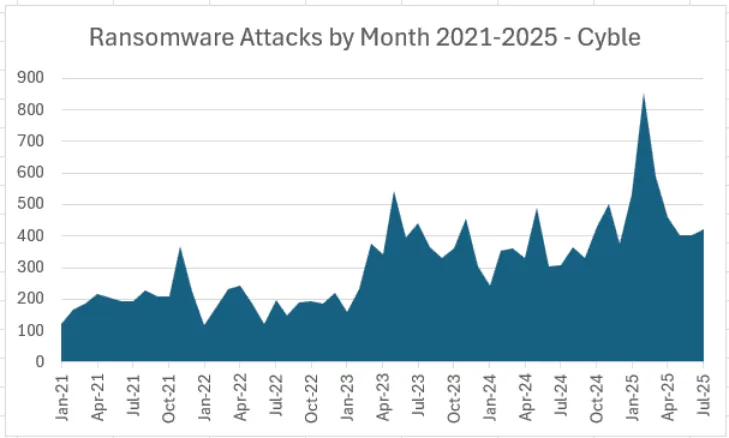
July’s ransomware landscape witnessed a concerning upward trajectory, with 423 total victims representing the third consecutive monthly increase following a three-month decline from February’s record-breaking 854 attacks.
Despite being roughly half of February’s peak numbers, current attack volumes remain significantly elevated compared to historical lows, with May’s 402 attacks still exceeding 2023’s lowest point of 161 incidents in January.
Critical Infrastructure Under Siege
The month saw particularly troubling developments in critical infrastructure targeting, with researchers identifying 25 possible incidents affecting government, law enforcement, energy utilities, and telecommunications sectors.
An additional 20 incidents involved organizations with potential supply chain implications, amplifying the downstream risk to interconnected systems and services.
INC Ransom emerged as the second most active group with 59 claimed victims, driven by aggressive campaigns targeting critical infrastructure providers.
Notable incidents included attacks on U.S.-based building automation system developers, power transmission companies, and Canadian underwater infrastructure inspection firms.
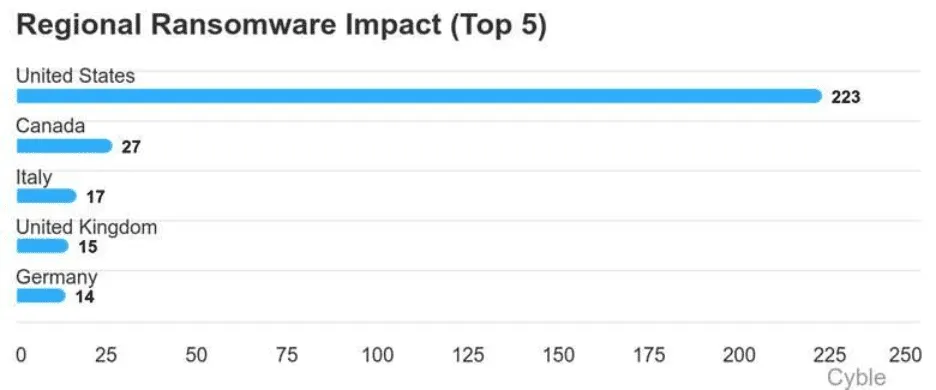
The geographical distribution remained heavily skewed toward North America, with the United States suffering 223 attacks—eight times more than second-place Canada.
Professional services and construction sectors bore the brunt of attacks, accounting for over 25% of incidents, followed by manufacturing, healthcare, and information technology organizations.
Europe represented the second most targeted region after North America, with Italy, the United Kingdom, Germany, France, and Spain experiencing the highest victim counts.
Evolving Technical Landscape
July’s ransomware ecosystem demonstrated continued innovation with nearly 40 new variants identified alongside several emerging threat groups.
Security researchers highlighted seven particularly concerning vulnerabilities being weaponized in campaigns, including CVE-2023-48788 affecting Fortinet FortiClientEMS and multiple Microsoft SharePoint vulnerabilities.
New entrants like D4RK4RMY introduced novel ransomware-as-a-service models combining base salaries with 50% ransom commissions.
At the same time, groups like AiLock demonstrated advanced technical capabilities through multithreaded encryption mechanisms using ChaCha20 and NTRUEncrypt algorithms.
The Gunra group’s expansion into Linux environments with support for up to 100 parallel encryption threads signals the growing sophistication of cross-platform ransomware operations.
The persistent evolution of ransomware groups underscores the critical need for enhanced cyber resilience strategies, including network segmentation, zero-trust architectures, immutable backup systems, and comprehensive vulnerability management programs to counter these escalating threats.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates