Cisco Talos has identified a sophisticated technique employed by the Qilin ransomware group, in which threat actors leverage legitimate Windows utilities, specifically MSPaint and Notepad, to inspect and locate high-sensitivity information across compromised networks manually.
This methodical approach represents a critical evolution in the group’s post-compromise activity, demonstrating their focus on maximizing data exfiltration before encryption deployment.
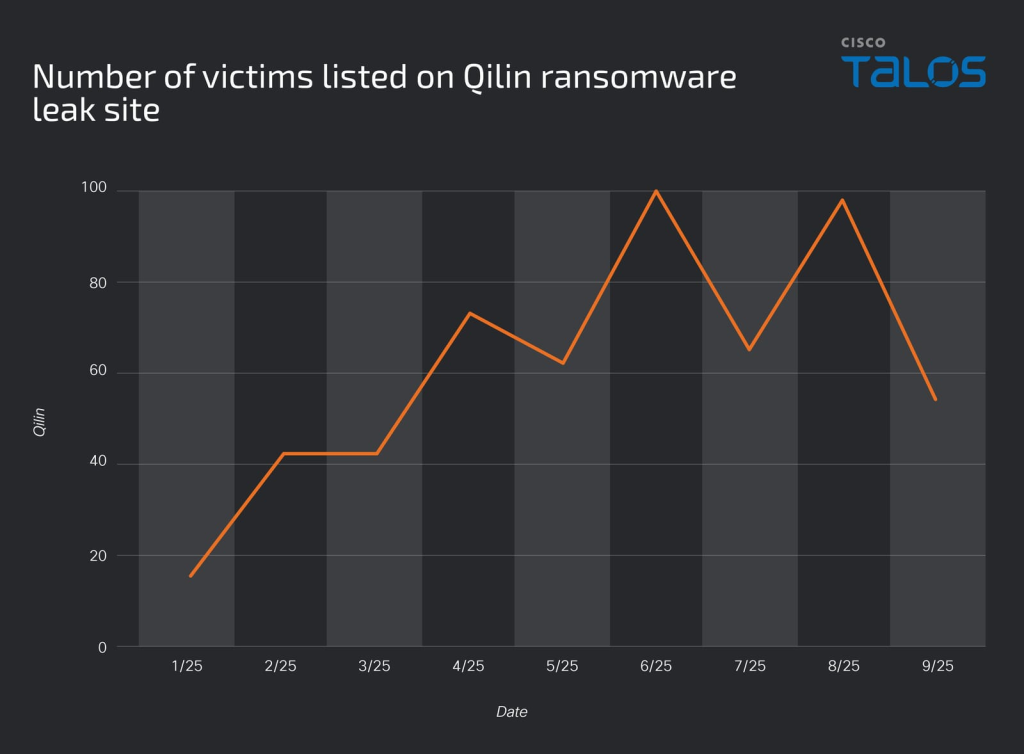
The Qilin group, which has maintained operations since July 2022, continues to pose a significant threat with over 40 victim postings per month on its leak site during the second half of 2025.
Talos researchers discovered that after successfully gaining network access and harvesting credentials, attackers use these benign applications to review files during their reconnaissance phase, effectively bypassing traditional detection mechanisms that might flag specialized data-discovery tools.
Tactical Implementation and Data Exfiltration
During the credential access and exfiltration phase, attackers execute a comprehensive credential-harvesting workflow using tools such as Mimikatz, NirSoft password recovery utilities, and custom scripts.
Following successful credential collection, they package targeted data using WinRAR with specific command-line arguments configured to exclude base folders and prevent recursive subdirectory processing.
The attackers then manually browse file systems using notepad.exe and mspaint.exe, examining numerous files to identify sensitive information worthy of exfiltration.
This manual inspection technique proves particularly effective in enterprise environments where security teams focus monitoring on known data discovery and exfiltration tools.
By utilizing legitimate Windows applications already whitelisted in most environments, the threat actors significantly reduce their detection footprint while maintaining the ability to target high-value data selectively.
The exfiltration infrastructure has evolved substantially. Talos identified widespread abuse of Cyberduck, an open-source file transfer tool that enables uploads to cloud servers, including Backblaze.
By leveraging legitimate cloud services, attackers obfuscate their activities within trusted domains and encrypted traffic, making detection considerably more challenging for network defenders.
The Cyberduck history files examined during the investigation revealed custom multipart upload configurations designed to efficiently transfer large file volumes.
Attribution and Operational Scope
Code analysis revealed character encodings and linguistic patterns suggesting operator origins from Eastern Europe or Russian-speaking regions, though Talos notes this could potentially constitute a false flag operation.
The manufacturing sector remains the most heavily impacted vertical, representing approximately 23% of all reported Qilin cases, followed by professional and scientific services at 18% and wholesale trade at 10%.
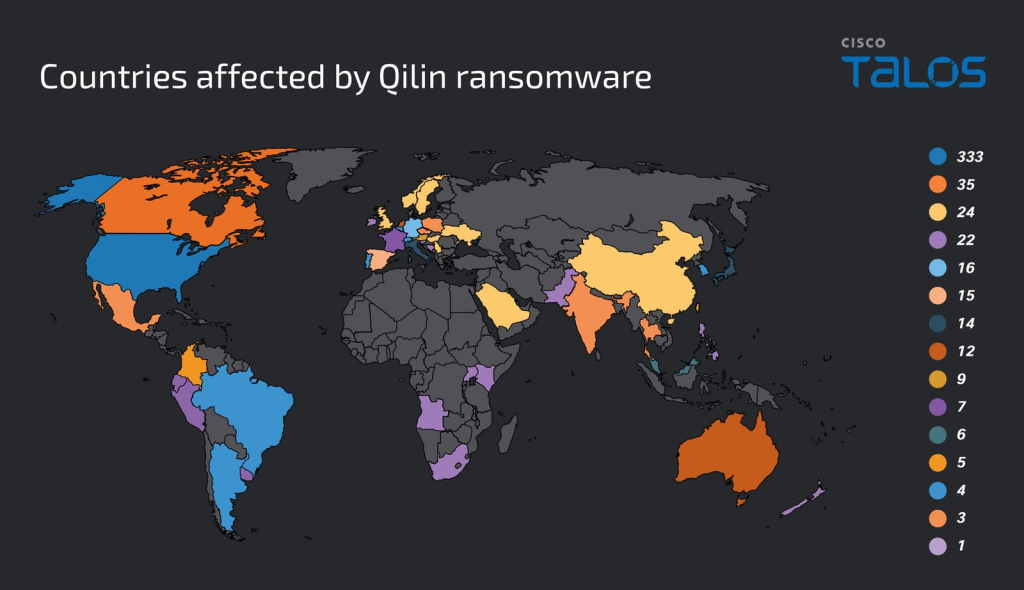
The group’s Ransomware-as-a-Service model continues to enable numerous affiliate operations globally, with the United States, Canada, the United Kingdom, France, and Germany among the most affected countries.
Talos observations indicate that attackers deploy dual encryption payloads encryptor_1.exe, distributed via PsExec across network hosts, and encryptor_2.exe, executing from single systems to encrypt multiple network shares.
Defense evasion techniques include AMSI disabling, obfuscated PowerShell commands, and EDR removal using open-source tools such as dark-kill and HRSword.
Organizations should implement robust network segmentation, enforce multifactor authentication on VPN access, monitor for legitimate application abuse patterns, and maintain an immutable backup infrastructure to effectively mitigate Qilin’s evolving threat profile.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates