In early 2025, ZenSec investigations uncovered a significant wave of ransomware incidents exploiting critical vulnerabilities in the SimpleHelp Remote Monitoring and Management (RMM) platform.
The flaws, tracked as CVE‑2024‑57726, CVE‑2024‑57727, and CVE‑2024‑57728, allowed attackers to execute code remotely and seize complete control when SimpleHelp instances ran as SYSTEM.
Two ransomware-as-a-service (RaaS) groups, Medusa and DragonForce, weaponized these weaknesses to breach Managed Service Providers (MSPs) and propagate into downstream customer systems. Patches were available before the attacks, but many organisations had delayed deployment.
Once the adversaries compromised supplier‑hosted RMM servers, they leveraged them to access enterprise networks, turn off security tools, steal data, and encrypt systems, demonstrating once again how supply‑chain trust relationships can magnify impact.
Medusa: PDQ Deploy and RClone in Action
During Q1 2025, the Medusa ransomware group launched coordinated attacks across multiple UK organisations using compromised SimpleHelp servers.
Once inside, operators used PDQ Inventory and PDQ Deploy to distribute their payloads, deploying executables such as “Gaze.exe” via base64‑encoded PowerShell commands that disabled Microsoft Defender and added extensive exclusion paths.
Lateral movement was aided by network-scanning tools such as netscan.exe, while persistence was achieved through additional C2 utilities, including AnyDesk and repurposed SimpleHelp instances pointing to actor‑controlled servers.
In about half of the breaches, data was siphoned off via RClone (renamed lsp.exe), configured to exfiltrate moderately sized and aged files to avoid detection.
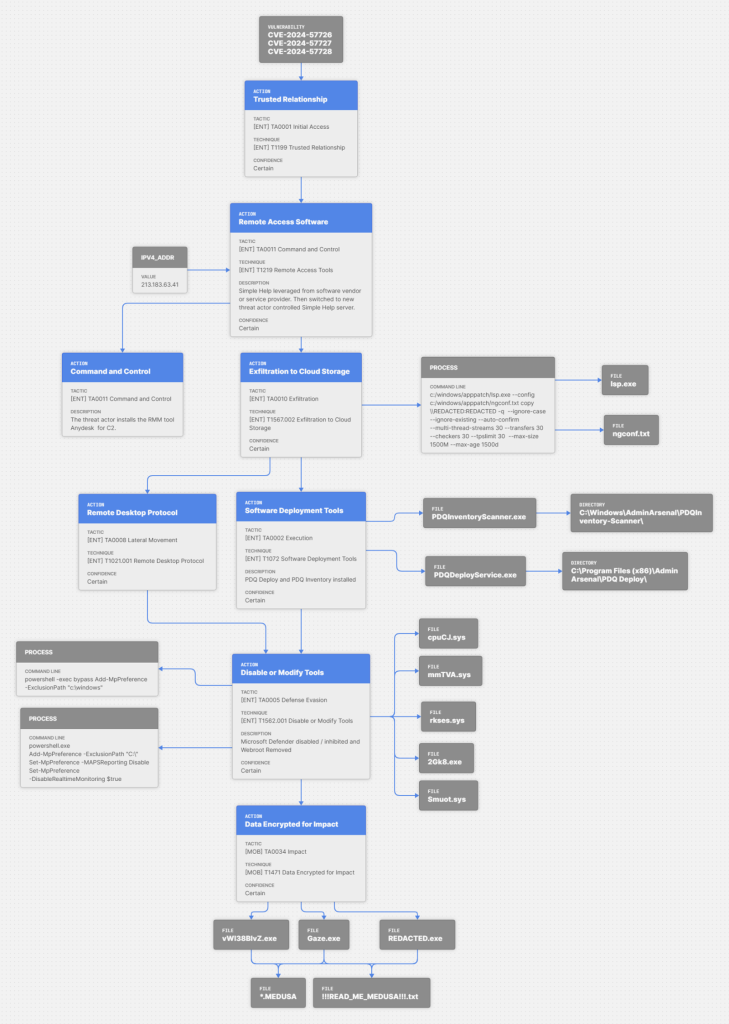
Encryption events appended files with “.MEDUSA” and dropped ransom notes titled “!!!READ_ME_MEDUSA!!!.txt.” Victim entries soon appeared on Medusa’s darknet leak portal, complete with proof‑of‑life screenshots and document previews, reinforcing the group’s double‑extortion strategy.
DragonForce: Restic‑Based Exfiltration and Credential Harvesting
By Q2 2025, DragonForce operators adopted similar methods, targeting MSP‑controlled SimpleHelp environments to pivot into clients. The group created local “admin” accounts and installed AnyDesk for hands‑on control, while disabling Microsoft Defender to evade detection.
Credential theft was a key step: attackers executed Get‑Veeam‑Creds.ps1 to harvest backup credentials from Veeam servers. Exfiltration was then performed using the open‑source backup utility Restic, configured to transfer stolen data to S3‑compatible storage such as wasabisys.com.
The encryption phase appended “.dragonforce_encrypted” extensions to victim files, scrambled file names, and placed “readme.txt” ransom notes containing a TOX ID for negotiation. Compromised data later surfaced on DragonForce’s Tor‑hosted leak site, where files were browsable and downloadable.
These campaigns underscore the systemic risk posed by compromised RMM infrastructure and highlight the urgency of rigorous patch management within supply‑chain dependencies.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates