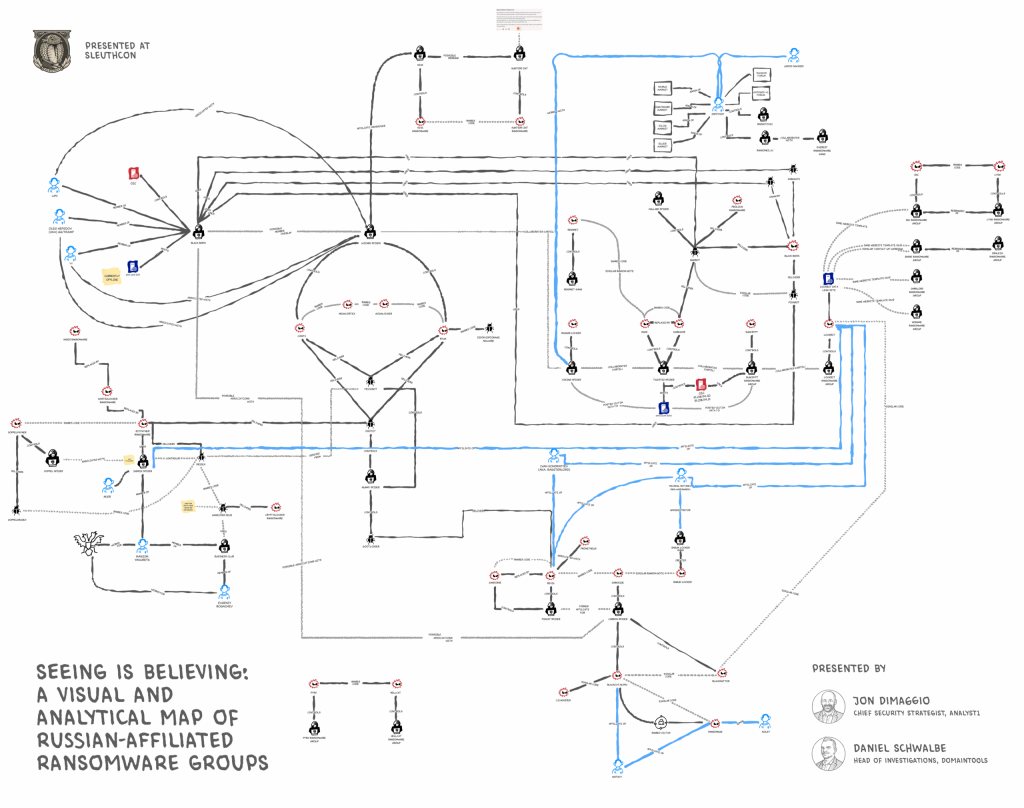
A collaborative research effort by Analyst1’s Jon DiMaggio, Scylla Intel, and the DomainTools Investigations Team has produced a groundbreaking visual map of Russian-affiliated ransomware operations.
Departing from the traditional model of tracking monolithic ransomware families, the project charts overlapping infrastructure, shared code fragments, and human capital migration across multiple criminal clusters.
Dubbed a “spider-out” investigation, the methodology began with well-known groups such as Conti, LockBit, and Evil Corp, then expanded outward by tracing passive DNS records, IP address overlaps, SSL certificate reuse, and delivery vectors such as phishing domains and exploit kits.
This approach revealed a fractured marketplace in which ransomware entities act as interchangeable modules rather than centralized organizations.
The analysis leveraged a blend of OSINT, historic infrastructure data, proprietary threat intelligence feeds, and HUMINT reporting to isolate high-signal overlaps from ambient noise.
Infrastructure intersections such as shared bulletproof hosting providers and reused C2 domains suggest affiliate-level resource pooling. Notably, DomainTools data highlighted IP clusters that proved resilient across multiple group takedowns, indicating enduring infrastructure networks.
Code-level analysis uncovered standard ransomware loaders and encryption routines, with some groups integrating legacy TrickBot and Qakbot components as initial access vectors.
Researchers also cataloged the widespread use of remote-access utilities, such as AnyDesk, Quick Assist, and Cobalt Strike, which hints at standardized tooling and operator playbooks.
Human Capital as the Core Asset
Beyond infrastructure and code, the infographic’s most striking revelations concern the movement of individual operators between ostensibly distinct ransomware brands.
Detailed profiles track actors like “Wazawaka” (Mikhail Matveev), whose known aliases span REvil, Babuk, LockBit, Hive, and Conti. Similarly, “Bassterlord” has navigated from REvil to Avaddon to LockBit and finally to Hive, illustrating that brand allegiance is fluid and subordinate to personal networks.
This operator drift underscores that human capital, specialized developers, negotiators, and infrastructure managers, is the primary asset within the ransomware economy. Rebranding emerges as a feature of the marketplace rather than an operational security lapse.
When law enforcement disruption or sanction pressures threaten a ransomware brand, operators migrate into new “cloned” identities, carrying over encryption toolkits, negotiation frameworks, and victim-engagement scripts.
The map shows distinct clusters of negotiators, developers, and infrastructure teams collaborating across multiple affiliate campaigns, suggesting a de facto division of labor.
The resulting ecosystem resembles a franchise model more than a hierarchy, with talented individuals rotating among brands based on profitability and trust relationships, rather than enduring corporate structures.
This reframing of the ransomware threat landscape carries immediate implications for defenders. Static group labeling no longer suffices; security teams must instead monitor clusters of activity typified by shared TTPs and infrastructure fingerprints.
Disruption strategies should prioritize takedowns of shared bulletproof hosting and affiliate-management platforms. Equally, law enforcement should focus on the human networks that bridge multiple brands, as targeting high-value operators can fracture entire clusters.
The new visual and analytical map provides a strategic lens, inviting the community to shift from tracking names to mapping modular capabilities and human alliances that sustain today’s ransomware marketplace.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates