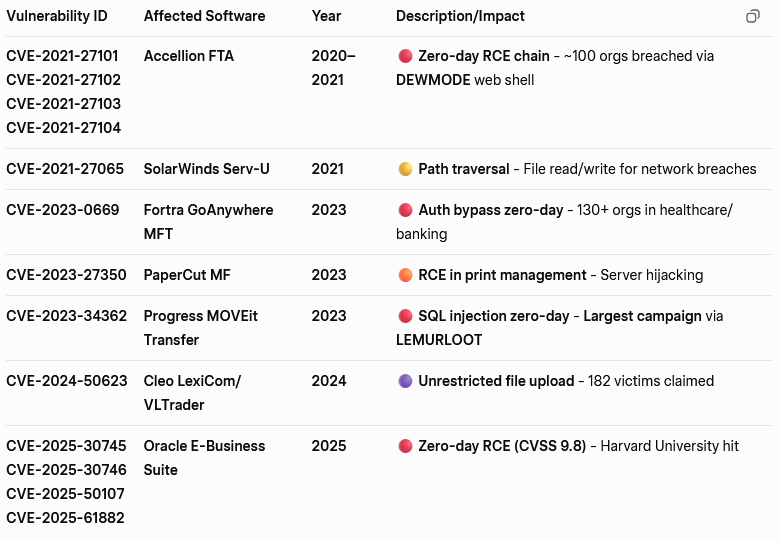
The Clop ransomware group, known for its extensive campaigns against global enterprises, has once again resurfaced with a fresh exploitation campaign abusing a newly identified zero-day in Oracle E‑Business Suite (CVE‑2025‑61882).
The flaw, first detected in June 2025 and later confirmed by Oracle in October, grants remote attackers unauthorized access to critical ERP functions such as procurement and logistics.
During the investigation, two initial command-and-control IPs, 185.181.60.11 (AS56655, Gigahost) and 200.107.207.26 (AS273045, DATAHOME S.A.) were identified. Further scanning uncovered over 90 additional active nodes across multiple countries.
These servers exhibited recurrent cryptographic fingerprints identical to previously documented Clop infrastructure, confirming operational continuity between their 2023 and 2025 campaigns.
Germany hosted the highest number of active servers, while Brazil, Panama, and Hong Kong followed closely. Notably, Russia’s direct hosting footprint has diminished, suggesting Clop’s strategic shift toward offshore ASNs to evade geopolitical blocks and threat intelligence filters.
Infrastructure Reuse and Network Correlation
A significant overlap was observed between the networks tied to the Oracle EBS exploits and those previously linked to the 2023 MOVEit Transfer (CVE‑2023‑34362) and Fortra GoAnywhere (CVE‑2023‑0669) campaigns.
Over 40 reused IP subnets, including ranges like 5.188.86., 88.214.27., and 45.182.189. Highlight Clop’s reliance on persistent backend infrastructure.
Pivoting through these subnets and correlating fingerprints revealed repeated identifiers such as f95812cbb46f0a664a8f2200592369b105d17dfe8255054963aac4e2df53df51, indicating tooling consistency across multiple years.
Attribution confidence was strengthened when matching these elements with historic CISA reports from the 2023 ransomware wave.
Emerging ASNs such as Batterflyai Media Ltd and Global Layer B.V. showed heavy clustering of these malicious endpoints, while entities like Alviva Holding Limited continued to appear as recurring facilitators of the threat actor’s network operations.
Transition to a Hybrid Network Model
Investigations further confirmed that Clop is gradually transitioning toward hybridized network layers blending legacy subnets from 2023 exploits with newly acquired server blocks in Latin America and the Middle East.
Approximately 77.8% of IP subnets analyzed show reuse patterns, confirming a resilient infrastructure recycling model that allows the group to sustain operations despite global takedown efforts.
Organizations relying on ERP systems like Oracle EBS should implement network-level monitoring across these subnet families and register them in observation lists rather than direct blocking. Even intermittent beaconing to these networks could indicate lateral intrusion or reconnaissance attempts.
Security specialists emphasize that Clop remains a high-priority ransomware actor, consistently exploiting unpatched enterprise software to secure footholds and exfiltrate sensitive data before deploying encryption payloads.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates