In early 2025, security researchers uncovered RapperBot. This sophisticated IoT botnet exploits zero-day vulnerabilities in network video recorders (NVRs) to orchestrate massive distributed denial-of-service (DDoS) attacks within seconds.
By harnessing legacy devices, many of which are no longer supported by manufacturers, the operators of RapperBot can unleash floods exceeding terabits per second, crippling high-profile targets in record time.
Exploit and Infection Chain
RapperBot’s infection begins with an Internet-wide scan targeting HTTP ports and UPnP-exposed devices.
Once a vulnerable NVR is identified, attackers employ a two-step exploit: first, a path traversal against the built-in web server to retrieve administrator credentials in both hash and plaintext; second, a forged firmware update delivered over TCP port 34567.
The malicious update mounts a remote NFS share. It executes a compact “z” script, which in turn deploys one of several architecture-specific binaries (ARMv4–v7, MIPS, PowerPC, RISC-V, x86, and more), ensuring compatibility across diverse IoT devices.
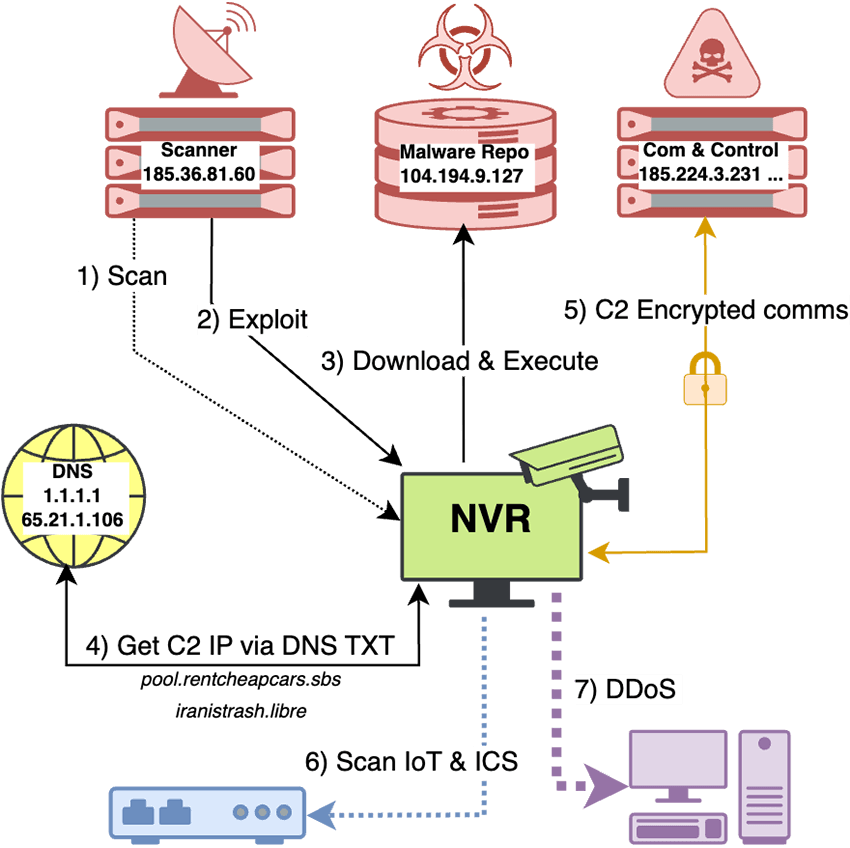
Within moments of execution, the malware vanishes from the disk and runs entirely in memory, sidestepping the need for persistence.
Infected devices immediately begin scanning the Internet for additional targets, most notably Telnet on port 23, while awaiting commands from the botnet’s command-and-control (C2) servers.
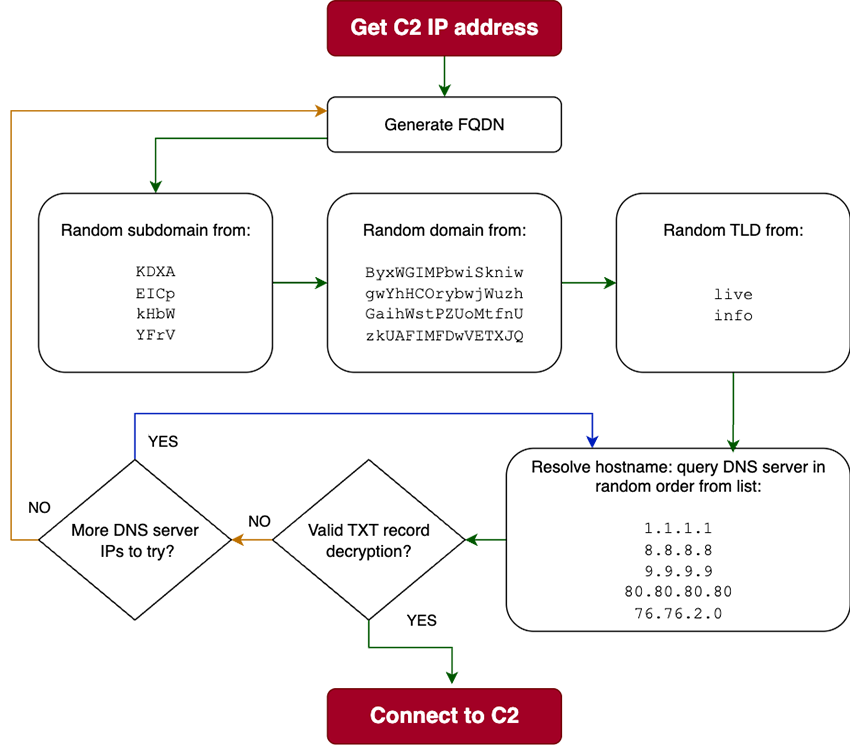
Instead of hardcoding C2 IP addresses, RapperBot employs an innovative mechanism using custom DNS TXT records served over the OpenNIC “.libre” top-level domain.
The malware cycles through a finite set of 32 possible FQDNs composed of four subdomains, four second-level domains, and two TLDs, and queries dedicated OpenNIC resolvers. Each TXT record contains a pipe-delimited, encrypted list of C2 IPs.
A bespoke decryption routine, akin to a truncated RC4 KSA combined with two-pass base-56 decoding, transforms the obfuscated payload into plaintext IP addresses, dynamically updating the bot’s C2 endpoints without direct server enumeration.
Rapid DDoS Execution and Takedown
Upon establishing an encrypted socket, typically on ports such as 4444, 1935, 3074, or 34567, devices await instructions to launch DDoS campaigns.
The lightweight packet format includes a one-byte XOR key, padded payloads, and a header checksum, enabling swift command delivery and evasion of simple IDS rules.
In July and August 2025, RapperBot-driven attacks exceeded 7 Tbps, leveraging tens of thousands of compromised IoT devices worldwide. A spike in bot-to-C2 traffic on August 6–7 foreshadowed a coordinated law enforcement intervention.
On August 19, U.S. authorities announced charges against an Oregon man alleged to operate “RapperBot,” as part of Operation PowerOFF.
Post-takedown observations show C2 servers rejecting or silently dropping connections, indicating a successful disruption at least temporarily of this devastating botnet.
As legacy IoT devices remain exposed in droves, RapperBot’s emergence underscores the urgent need for robust asset inventories, rigorous patch management, and disabling of unused services like UPnP.
Without such measures, threat actors will continue to exploit unpatched edge devices to power the next generation of ultra-fast DDoS attacks.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates