North Korean cyber actors have deployed a new Remote Access Trojan (RAT) targeting human rights defenders (HRDs) in South Korea and abroad, leveraging stolen code-signing certificates to bypass antivirus and Windows SmartScreen protections.
The malware, dubbed “EndClient RAT,” was discovered during a joint investigation with PSCORE, a leading NGO advocating for North Korean human rights.
The attack highlights the persistent threat posed by state-sponsored actors against civil society and the need for proactive threat intelligence sharing.
EndClient RAT Abuses Stolen Code-Signing Certificate to Evade Antivirus Detection
The EndClient RAT is delivered via a Microsoft Installer (MSI) package named “StressClear.msi,” which is code-signed by Chengdu Huifenghe Science and Technology Co Ltd, a Chinese mineral excavation company.
The certificate, valid until October 2025, was likely stolen, allowing the malware to appear legitimate to antivirus solutions and avoid triggering Windows SmartScreen alerts.
The MSI also bundles a legitimate South Korean banking software module, WIZVERA VeraPort’s Delphino package, which may serve as a decoy to reduce suspicion.
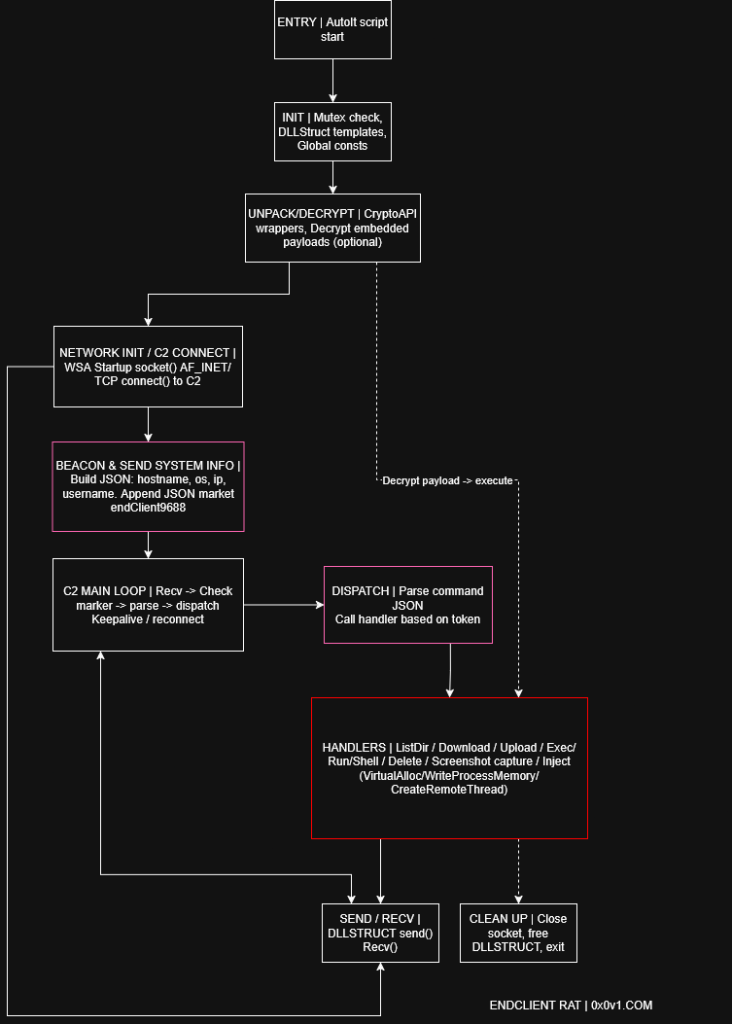
Once executed, the malware drops an AutoIT-based payload and establishes persistence by creating a scheduled task that runs every minute from the Public\Music directory.
The RAT uses a global mutex (Global\AB732E15-D8DD-87A1-7464-CE6698819E701) to prevent multiple instances and employs polymorphic mutation if Avast antivirus is detected, though Avast is uncommon in Korea, suggesting the attackers may be reusing code from other campaigns.
Technical Details and Command-and-Control Protocol
The EndClient RAT communicates with its command-and-control (C2) server at 116[.]202[.]99[.]218:443 using a custom protocol with sentinel-based framing.
The client sends system information in JSON format, marked with “endClient9688,” and receives commands marked with “endServer9688.” The protocol supports remote shell execution, file upload/download (limited to 30MB), and other standard RAT functionalities.
The malware creates four named pipes for remote shell communication and uses in-memory modules for protocol marker handling, Base64 encoding/decoding, and LZMA decompression.
Detection fidelity for the EndClient RAT is extremely low, with only 7/64 detections on the dropper and 1/64 on the payload script.
The attackers’ use of AutoIT, a common choice for North Korean threat actors, further complicates detection, as compiled AutoIT scripts are difficult for antivirus solutions to analyze.
Organizations and individuals should block the identified IOCs, hunt for the unique protocol markers (“endClient9688,” “endServer9688”), and monitor for scheduled-task artifacts and mutex usage. Signed MSIs should be treated as untrusted until their provenance is verified.
The discovery of EndClient RAT underscores the importance of democratic threat intelligence and collaboration between civil society and technical researchers to protect vulnerable communities from sophisticated cyber threats.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates