Security researchers have uncovered a sophisticated technique that exploits call gadgets to bypass Elastic EDR’s signature-based detection mechanisms.
The method works by inserting arbitrary modules into the call stack during module loading, effectively breaking the detection patterns that Elastic’s EDR engine relies upon to identify malicious activity.
This development underscores the ongoing cat-and-mouse game between threat actors and endpoint detection platforms.
The breakthrough leverages Elastic’s commitment to transparency, a double-edged sword in the security landscape.
Unlike many enterprise security vendors that keep their detection logic proprietary, Elastic publicly shares its detection rules and payload testing tools.
This openness enables the security community to thoroughly understand and challenge EDR mechanisms, fostering innovation and collaboration.
However, it also provides attackers with a clear roadmap to identify and circumvent detection strategies.
How Elastic’s Detection Framework Works
Elastic EDR’s detection engine prioritizes call stack analysis to identify suspicious activity. The system closely monitors module loads initiated from unbacked memory regions, code that exists only in RAM rather than on disk.
This behavior is a hallmark of malicious techniques like shellcode injection and in-memory code execution commonly employed by command-and-control implants.
Specific detection rules search for network modules loaded from unbacked memory, flagging patterns that deviate from legitimate application behavior.
Previous evasion attempts used techniques such as call stack spoofing and API proxying, which Elastic countered by introducing additional detection rules targeting these tactics.
syscall instruction, the alert will trigger:The vendor refined its approach by focusing on specific system libraries to reduce false positives while maintaining detection efficacy.
The newly disclosed research introduces a novel method: exploiting controllable call instructions known as gadgets found within system DLLs that aren’t currently targeted by EDR signatures.
By manipulating these gadgets during network library loading operations, researchers insert an arbitrary module into the observed call stack, disrupting the signature patterns that trigger Elastic’s alerts.
The proof-of-concept demonstration utilized a specific call-return gadget from an older version of dsdmo.dll.
When this gadget is invoked during network library loading, such as with wininet.dll, the inserted module appears in the call stack, breaking the expected detection signature.
The result: previously detectable operations now go unnoticed by the EDR agent.
This approach builds upon established research into shellcode obfuscation and callback-based API proxying, but demonstrates a practical methodology for discovering real gadgets in widely available system DLLs.
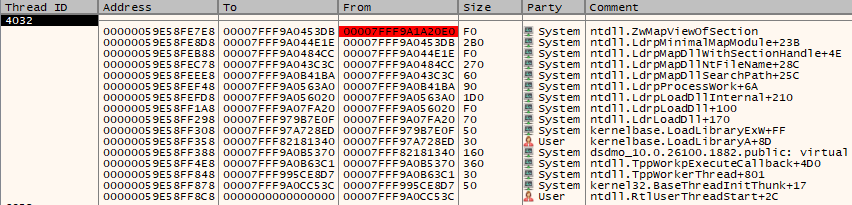
Although the tested gadget originates from a deprecated library version, the research provides a reproducible process for identifying similar gadgets in current DLL sets.
The researchers responsibly disclosed this evasion technique to Elastic, which is actively developing updated detection rules to address this bypass vector.
This finding highlights the critical importance of ongoing collaboration and transparency within the cybersecurity community.
While this specific technique targets one detection mechanism, Elastic EDR maintains numerous additional detection opportunities throughout an attack’s lifecycle, making it far from obsolete.
Cyber Awareness Month Offer: Upskill With 100+ Premium Cybersecurity Courses From EHA's Diamond Membership: Join Today