In a worrying trend, cybercriminals are increasingly hijacking Remote Monitoring and Management (RMM) tools, the same software trusted by IT departments for legitimate remote access, to breach organizations, exfiltrate data, and even deploy ransomware.
A recent attack analyzed in Sublime Security’s “Attack Spotlight” series reveals the evolving sophistication of these threats and highlights the urgent need for adaptive, AI-driven email security.
Double Trouble: Two RMMs, One Attack
The attack began with a phishing email sent from a compromised Microsoft 365 account. Disguised as an official Microsoft OneDrive notification, the email contained convincing branding and a link encouraging recipients to access a shared file.
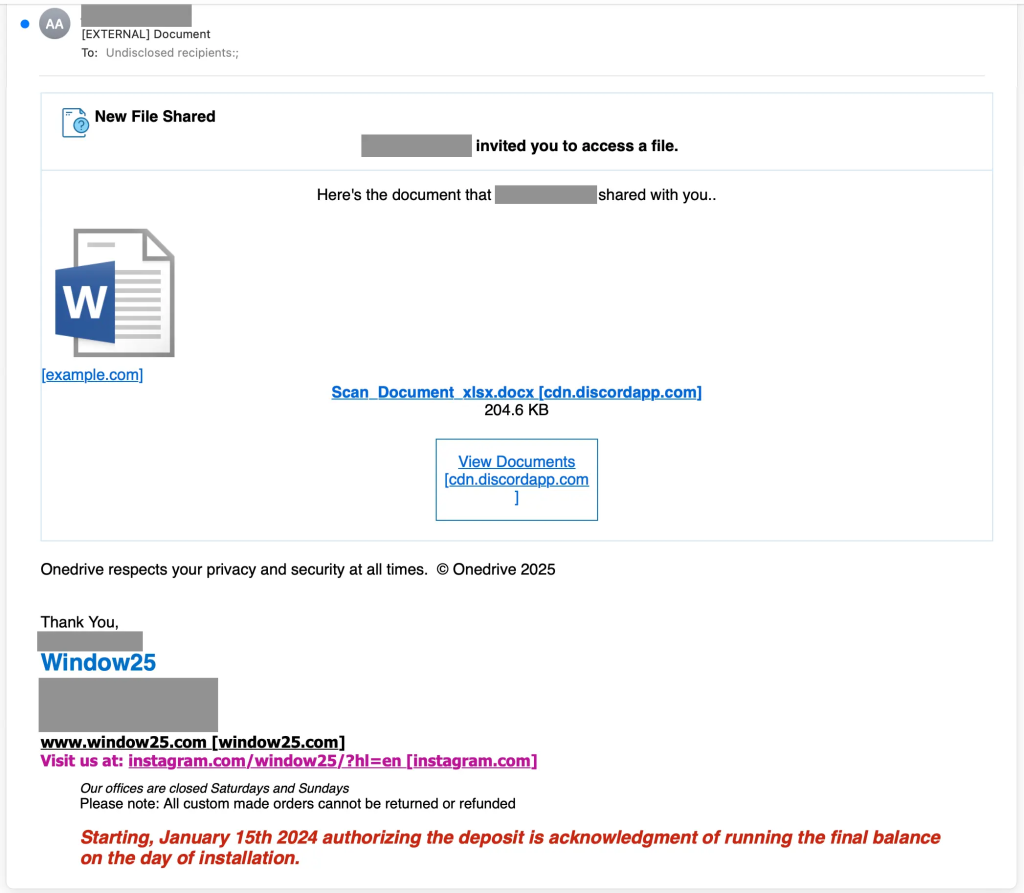
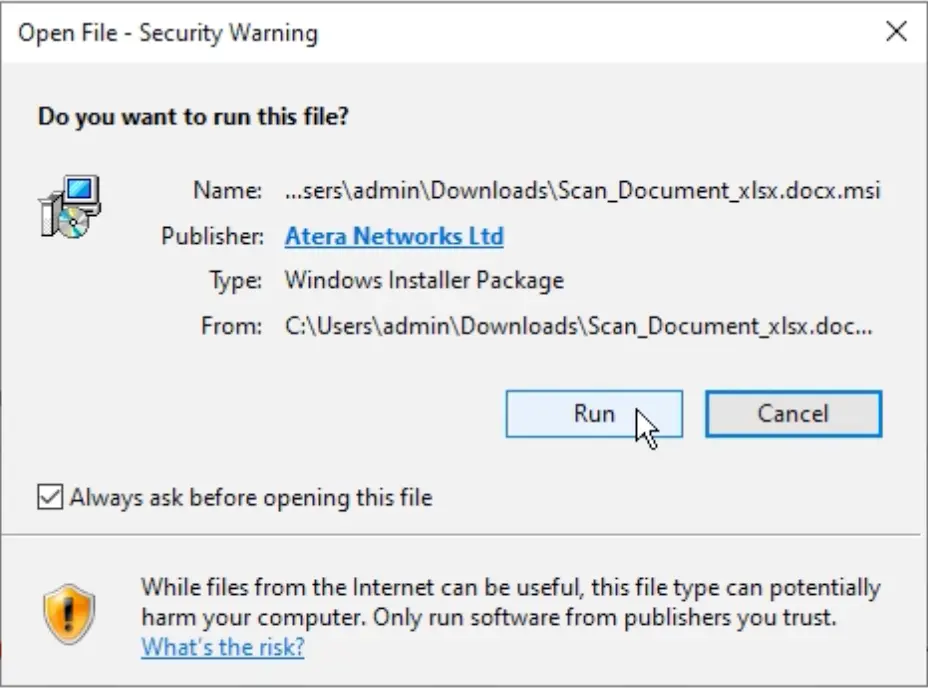
However, the download was not a legitimate Word document, as suggested by the .docx extension, but rather a malicious .msi installer, a classic case of file extension manipulation.
Once executed, the payload installed two RMM tools: Atera and Splashtop Streamer. While the Atera Agent’s setup was user-attended, Splashtop and a necessary .NET runtime were quietly installed in the background via silent processes.
By deploying two RMM platforms, attackers ensured redundancy: if one tool was detected and removed, they could maintain access through the other.
Both RMMs are legitimate IT tools, which means their network activity and presence can easily be overlooked in noisy enterprise environments.
The payload was distributed using the Discord CDN, a free hosting service popular among threat actors for its ability to fly under the radar of many security filters. The attack also targeted an undisclosed recipient list, making it challenging to pinpoint affected parties and track its spread.
Anatomy of a Modern Malware Delivery
Each step of the attack exploited common business workflows and weaknesses in legacy email security:
- File extension manipulation: The email promised a .docx but delivered a .msi file, increasing the probability of execution by unsuspecting users.
- OneDrive impersonation: Meticulous use of branding and familiar corporate footers lulled recipients into a false sense of trust.
- Legitimate infrastructure abuse: Downloads for Splashtop Streamer and the .NET runtime originated from official sources, masking installation traffic as routine endpoint activity.
- Stealth and redundancy: Dual RMM installs enhanced attacker persistence, enabling ongoing access even if one avenue is closed.
- Free, popular hosting: Leveraging Discord’s CDN allowed attackers to bypass many conventional URL-blocking mechanisms.
Defense in Depth: Adaptive Security is Essential
Sublime Security’s AI-based detection engine flagged this attack using signals such as mismatched file types, brand impersonation, and traffic analysis.
This incident underscores the rise in abuse of RMM tools in real-world attacks and why organizations need adaptive security that detects subtle, context-based anomalies rather than relying solely on static indicators.
The use of RMMs as covert footholds will likely grow, making proactive, AI-driven detection and education the frontline defenses against these new avenues of control and compromise.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates