A sophisticated botnet campaign identified by Trend Micro’s Zero Day Initiative has expanded its operations to exploit over 50 vulnerabilities across more than 30 vendors, targeting internet-facing network infrastructure, including routers, digital video recorders, network video recorders, CCTV systems, and web servers.
The RondoDox campaign represents a significant evolution in automated exploitation techniques, employing what researchers describe as an “exploit shotgun” approach that deploys multiple attack vectors simultaneously.
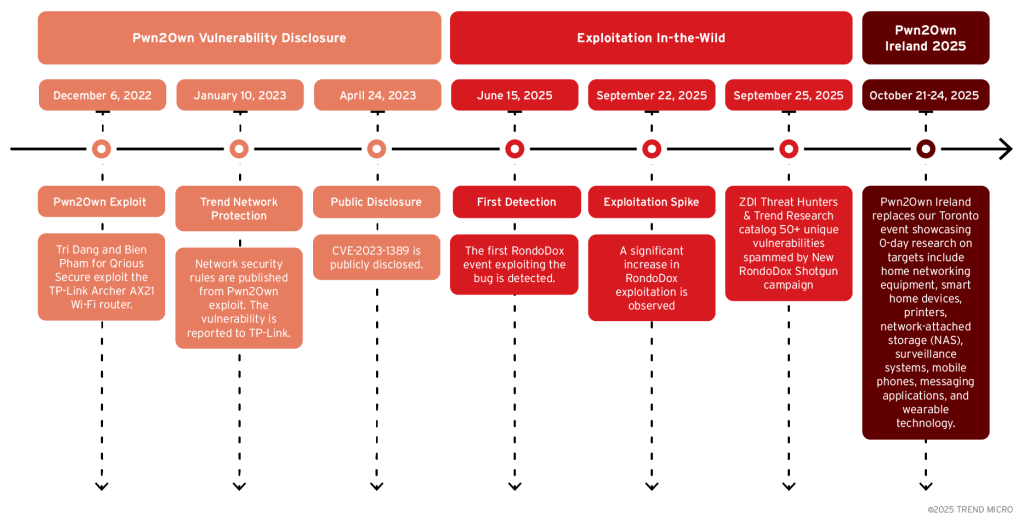
From Pwn2Own Discovery to Active Exploitation
The campaign’s origins trace back to vulnerabilities discovered during cybersecurity competitions. Researchers first detected RondoDox intrusion attempts on June 15, 2025, using CVE-2023-1389, a vulnerability initially demonstrated at Pwn2Own Toronto 2022 targeting TP-Link Archer AX21 Wi-Fi routers.
This particular flaw affects the WAN interface and enables command injection attacks, allowing attackers to gain shell access and deploy multi-architecture payloads.

Initial analysis revealed that RondoDox began by focusing on specific vulnerabilities, including CVE-2024-3721 affecting TBK DVRs and CVE-2024-12856 targeting Four-Faith routers.
However, the campaign has since evolved into a comprehensive multi-vector operation that weaponizes both publicly disclosed vulnerabilities and zero-day exploits discovered at security competitions.
Comprehensive Vulnerability Arsenal
Technical analysis of the RondoDox campaign reveals exploitation of 56 total vulnerabilities, with 38 assigned CVE identifiers and 18 remaining unassigned.
Command injection vulnerabilities represent the primary attack vector, accounting for 50% of the exploited flaws. The remaining vulnerabilities include path traversal, buffer overflow, authentication bypass, and memory corruption issues.
The campaign targets devices from major vendors, including D-Link, TP-Link, Netgear, Cisco, TOTOLINK, Linksys, and numerous others.
Notable vulnerabilities include the decade-old Shellshock bug (CVE-2014-6271) affecting GNU Bash, Apache HTTP Server path traversal flaws (CVE-2021-41773 and CVE-2021-42013), and various router-specific command injection vulnerabilities spanning multiple device generations.
Several of the exploited vulnerabilities have been added to CISA’s Known Exploited Vulnerabilities catalog, elevating them to high-priority patching targets.
The campaign‘s loader-as-a-service infrastructure co-packages RondoDox with Mirai and Morte payloads, significantly increasing the complexity of detection and remediation efforts.
Organizations operating internet-exposed network devices face heightened risk from this campaign, which enables data exfiltration, persistent network compromise, and operational disruption.
Security researchers emphasize that the vulnerability lifecycle reveals an uncomfortable reality: the window between public disclosure and widespread exploitation continues to shrink.
This makes immediate patching and proactive security measures essential for defending against sophisticated automated attacks targeting network edge infrastructure.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates