Cybersecurity researchers at ANY.RUN has identified a previously undocumented PhaaS framework dubbed “Salty 2FA” that targets explicitly Microsoft 365 credentials and can bypass multiple two-factor authentication methods.
The platform represents a significant evolution in phishing attack sophistication, employing advanced evasion techniques and multi-stage execution chains to avoid detection.
Unique Infrastructure and Execution Chain
Salty 2FA distinguishes itself through a distinctive domain infrastructure pattern combining .com subdomains with .ru top-level domains, following the format. <subdomain>.<maindomain>.??.com.
This unique fingerprint emerged during threat hunting activities when analysts noticed recurring domain patterns across multiple sandbox sessions that had initially evaded detection.
The framework operates through a complex five-stage execution chain. Stage 1 begins with an obfuscated JavaScript “trampoline” that initializes Cloudflare Turnstile validation and decodes the following payload URL.
Stage 2 delivers an encrypted payload containing a fake Microsoft login page with embedded obfuscation techniques.
The attack progresses through client-side logic implementation, data exfiltration via .ru domains using encoded POST requests, and culminates in sophisticated 2FA handling capable of processing phone app notifications, SMS OTP, voice calls, and companion app authentication methods.
Advanced Evasion and Anti-Analysis Capabilities
The platform implements multiple defense mechanisms to hinder analysis and detection.
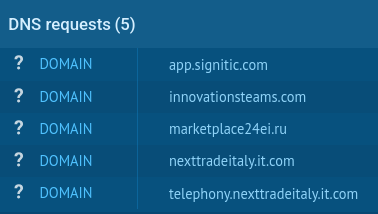
These include blocking keyboard shortcuts for developer tools, measuring debugger execution time to detect sandbox environments, and employing dynamic jQuery element ID generation combined with Base64 and XOR encoding.
Data exfiltration utilizes session-derived encryption keys, with stolen credentials transmitted to endpoints following the format. /<5-6_digits>.php.
Global Target Profile and Attribution Challenges
Analysis of phishing campaigns reveals Salty 2FA targets span multiple industries, including financial services, telecommunications, energy, logistics, healthcare, and government sectors across the United States, Europe, and other regions.
Standard lures include voice message notifications, document access requests, and billing statements.
While some infrastructure overlap exists with Storm-1575 and Storm-1747 threat groups, researchers determined Salty 2FA possesses sufficient unique characteristics to warrant separate classification.
Activity monitoring indicates the framework gained momentum in June 2025, with confirmed attribution beginning in late July 2025 and continuing through current observations.
Detection Recommendations
Traditional signature-based detection proves ineffective against Salty 2FA due to constant code mutation and obfuscation.
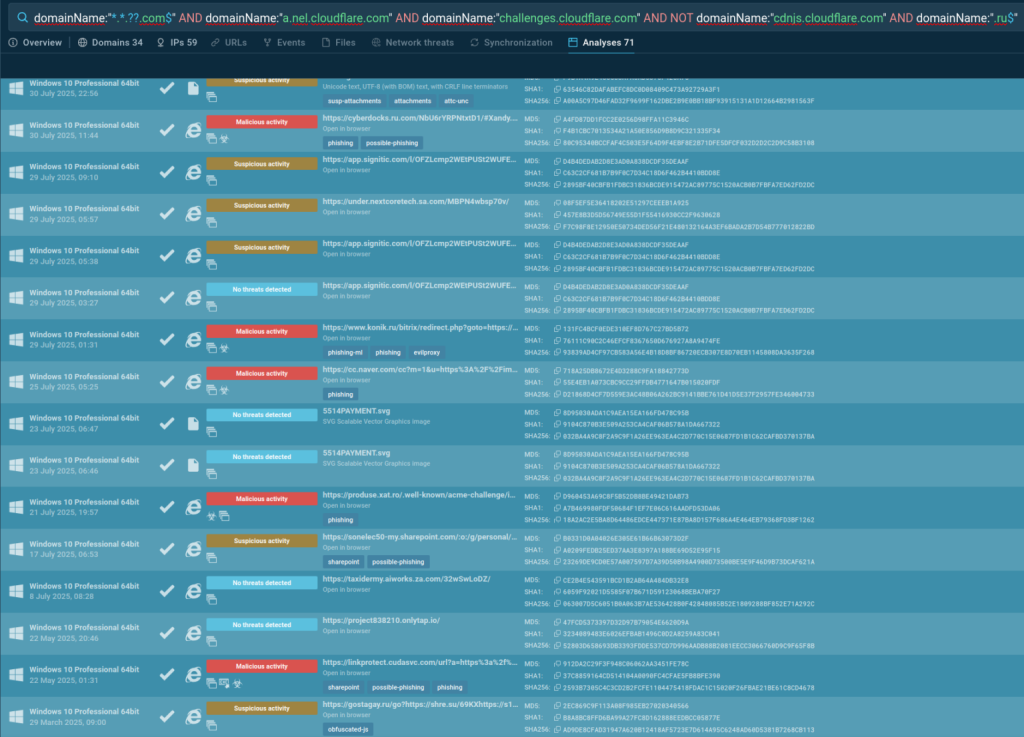
Security teams should focus on behavioral pattern recognition, including the characteristic domain pairing, specific JavaScript library loading patterns, and the three-domain C2 architecture consisting of primary phishing, controller, and exfiltration domains.
Interactive sandbox analysis remains essential for exposing the complete execution chain and infrastructure elements in real-time environments.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates