A newly exposed zero-day vulnerability, CVE-2025–31324, in SAP NetWeaver’s Visual Composer Metadata Uploader component has ignited concern across enterprise IT and cybersecurity circles.
The flaw enables attackers to perform unauthenticated file uploads to a SAP server, paving the way for remote code execution under privileged SAP service accounts. This scenario could spell disaster for affected organizations.
How the Script Works
At the heart of this threat is a Python-based exploit script tailored to abuse a missing authorization check on the vulnerable endpoint: /developmentserver/metadatauploader. This script automates exploitation via carefully sequenced steps:
- Argument Parsing and Concurrency: Upon launch, the script parses target details, protocols, and concurrency parameters. It provides both “check” mode (safe vulnerability testing using out-of-band Java deserialization payloads) and “exploit” mode (actual web shell deployment), with support for multi-host parallel scanning.
- OAST Payload for Stealth Checking: In vulnerability-check mode, the script sends a serialized Java object (often concealed with Base64 encoding) which, if processed by SAP, triggers an out-of-band callback (OAST)—a silent indicator that a system is exploitable without dropping a visible web shell.
- JSP Web Shell Upload: Exploit mode prompts the upload of a malicious JSP file by default, a simple command-execution shell named
helper.jsp. This is transmitted inside a multipart/form-data HTTP POST, leveraging Python’srequestslibrary. The file lands in the easily accessible directory/irj/servlet_jsp/irj/root/, enabling the attacker to invoke system commands remotely by accessing the web shell via HTTP requests and passing commands via query-string parameters. - Obfuscation and Evasion: Malicious payloads and web shells are obfuscated within the script using Base64 encoding. File names may be randomized (e.g.,
cglswdjp.jsp) or disguised (e.g.,.webhelper.jsp) to evade standard defensive scans. The script’s default “python-requests” User-Agent string also appears in attack logs, further aiding detection for defenders.
Attack Flow, Detection, and Defense
The exploit chain unfolds in clear steps: initial access via file upload (MITRE T1190), web shell deployment (T1505.003), command execution (T1059.003), and persistence via the shell.
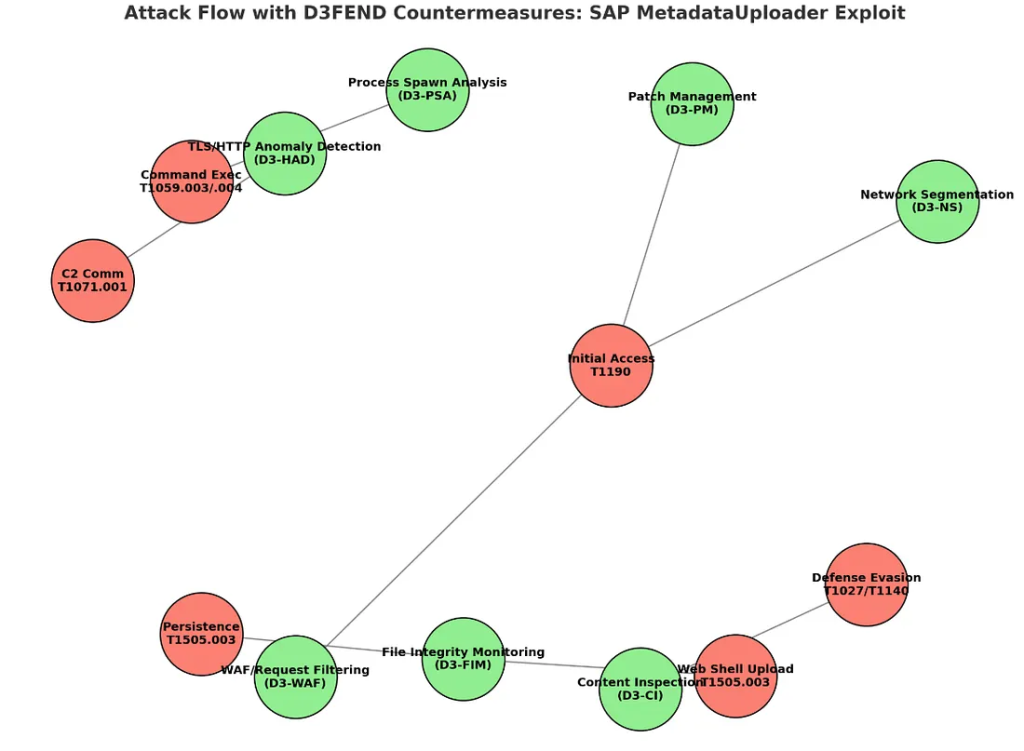
Indicators of compromise include unexplained POSTs to the vulnerable endpoint, the presence of odd JSP files in SAP directories, and suspicious process execution under SAP Java accounts.
SAP released Security Note 3594142 as an immediate patch. Network-level defenses, such as WAF rules, denying access to /developmentserver/, file integrity monitoring, and vigilant log analysis for exploit signatures (e.g., Base64 blobs, randomized .jsp filenames), remain crucial for organizations yet to patch.
Advanced monitoring should focus on SAP web path accesses, anomalous process spawns, and unusual outbound communications.
The emergence of CVE-2025–31324 highlights the importance of rapid vulnerability management and detection for business-critical applications, particularly in the face of ever-evolving threat actor tactics.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates