A new cybercriminal consortium calling itself Scattered LAPSUS$ Hunters (SLH) has emerged, consolidating three of the most infamous threat groups in recent years: Scattered Spider, ShinyHunters, and LAPSUS$.
Trustwave SpiderLabs’ threat intelligence team discovered the development, describing it as a “federated alliance” offering Extortion-as-a-Service (EaaS) and inheriting the operational DNA of The Com, a loosely connected cybercriminal ecosystem known for brand-sharing and fluid collaboration.
The first SLH channel appeared on Telegram on August 8, 2025, under the handle “scattered lapsu$ hunters – The Com HQ SCATTERED SP1D3R HUNTERS.”
The group utilizes Telegram not only as its coordination hub but also as a performative platform to stage its public identity, combining financial motivation with a hacktivist-like flair for spectacle.
Despite frequent takedowns at least 16 observed iterations of its channel, SLH has consistently reestablished its presence, emphasizing adaptability and determined persistence.
Blending Branding and Extortion Operations
Following the collapse of BreachForums earlier this year, SLH quickly occupied the resulting power vacuum by repackaging assets and reputational credibility from defunct collectives.
The group prominently promotes its EaaS model, inviting affiliates to “rent” its notorious branding for intimidation leverage in negotiation-driven extortion campaigns.
SLH’s communications combine mocking posts targeting law enforcement with proof-of-compromise teasers, doxing campaigns, and interactive polls aimed at enlisting followers into harassment or data pressure operations.
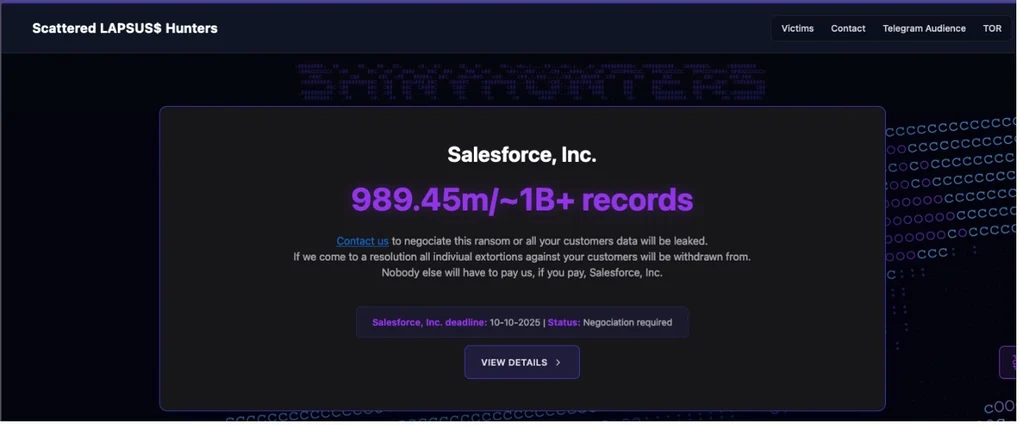
The group also references an in-development “Sh1nySp1d3r Ransomware,” reflecting its intent to integrate ransomware into its monetization pipeline, though analysts have found no evidence of active deployment.
Trustwave’s analysis attributes the core of SLH to fewer than five operators, despite the larger number of visible personas.
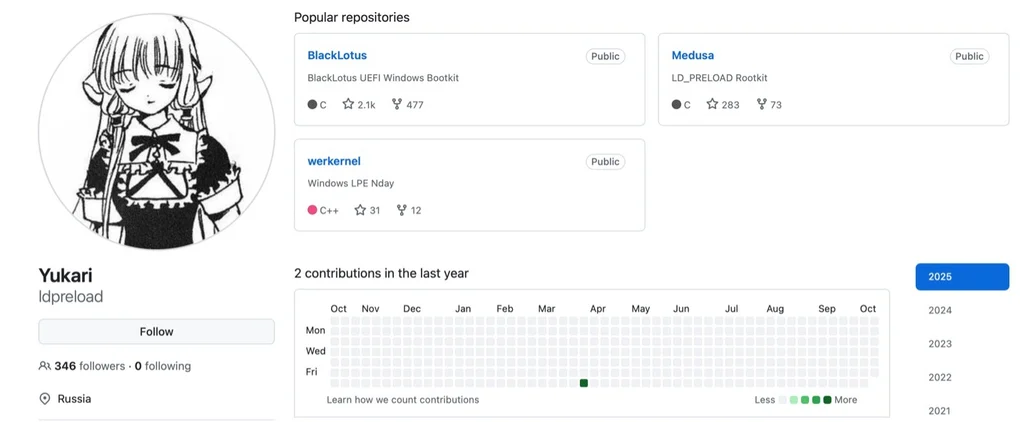
Key figures include the orchestrator “shinycorp,” data broker “Alg0d,” and exploit developer “Yukari/Cvsp,” who boasts verifiable experience in vulnerability development and underground brokerage involving projects such as BlackLotus and Medusa rootkits.
Technical Sophistication and Future Threat
SLH’s tactics reflect a mature blend of intrusion tradecraft and social engineering. The group demonstrates skill in AI-assisted vishing, spearphishing, privilege escalation, and rapid exfiltration of high-value data from cloud and CRM environments.
Its activity overlaps with the exploitation of vulnerabilities such as CVE‑2025‑31324 (SAP NetWeaver) and CVE‑2025‑61882 (Oracle E‑Business Suite), suggesting possible code sharing with other known ransomware operators.
Trustwave assesses that SLH represents not a new threat collective but a strategic reorganization of veteran operators adapting to disruption in underground markets.
By fusing communication theatrics with technical capability, the Scattered LAPSUS$ Hunters signal a next-generation model of cyber-extortion, one that leverages perception, branding, and persistence as operational weapons heading into 2026.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates