A sophisticated supply chain attack involving the “Scavenger” malware has recently rocked the JavaScript developer community.
Developers discovered unauthorized releases for the widely used eslint-config-prettier npm package, even though these changes did not appear in the official GitHub repository.
It was soon confirmed by the package maintainer that their npm account had been compromised, enabling threat actors to publish malicious versions of several packages, including eslint-config-prettier, eslint-plugin-prettier, snyckit, @pkgr/core, and napi-postinstall in specific versions.
Infection Mechanism
Investigation revealed that the compromised versions shipped a malicious install.js script.
Upon installation on Windows systems, this script executed a DLL named node-gyp.dll via rundll32.exe, invoking the logDiskSpace function.
The DLL, acting as the “Scavenger Loader,” was compiled the same day as the attack, hinting at a highly coordinated operation.
The loader is packed with anti-analysis measures, including detection of virtual machines (by hunting for SMBIOS signatures related to VMware or QEMU), process module scans for well-known antivirus tools and sandboxing DLLs (like Avast’s snxhk.dll, Sandboxie’s SbieDll.dll, and others), and refusal to execute if the system appears to be under analysis or emulation.
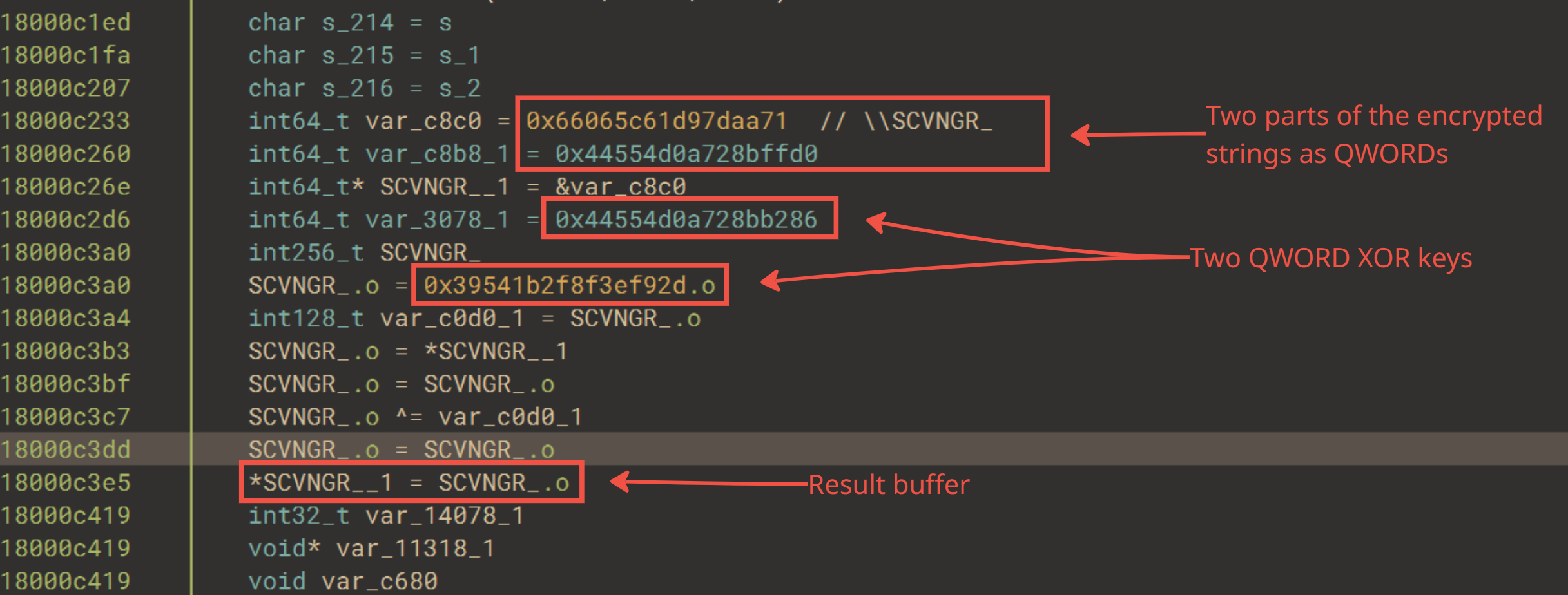
It uses indirect syscalls and function-level CRC32 hashing to complicate reverse engineering, and its routines dynamically resolve imports and decrypt strings stored with custom XOR and XXTEA encryption algorithms.
Chrome Data Targeting
Once past this filtering, the loader deploys a second stage: the Scavenger infostealer. Like its delivery loader, this component is heavily obfuscated and employs many of the same anti-debugging methods, function hashing, and custom string obfuscation.
Notably, it targets Chromium-based browsers, looking for internal artifacts such as Extensions, ServiceWorkerCache, DawnWebGPUCache, and Visited Links.
This configuration strongly suggests an intent to steal authentication tokens, session data, and browsing history, increasing the risk of credential theft and session hijacking for developers who installed the poisoned libraries.
Communication with attacker-controlled servers is handled via HTTPS and HTTP, with all payloads transmitted in base64 and encrypted using XXTEA.
The malware verifies server authenticity by expecting campaign IDs and responding to handshake integrity checks.
Network traffic is sent to a range of domains some previously seen in malware attached to the BeamNG gaming community indicating possible overlap or reuse by these actors.
Further analysis uncovered telltale signs confirming the link between the npm campaign and prior attacks.

For example, one lighter Scavenger variant left behind a debug path referencing the “scavenger” name and utilized a simple WinExec-initiated cURL download to fetch additional payloads. This, along with overlaps in command and control domain use, solidifies the attribution.
Security researchers and the npm ecosystem maintainers responded by removing the affected package versions and investigating related accounts.
The community continues to monitor post-compromise indicators and encourages developers to review dependencies installed during the incident window.
Indicators of Compromise
| Indicator Type | Value |
|---|---|
| URLs | https://ac7b2eda6f1.datahog.su https://datahog.su https://datacrab-analytics.com https://datalytica.su https://smartscreen-api.com https://dieorsuffer.com https://firebase.su https://fileservice.gtainside.com/fileservice/downloads/ftpk/1743451692_Visual%20Car%20Spawner%20v3.4.zip |
| Hashes | 877f40dda3d7998abda1f65364f50efb3b3aebef9020685f57f1ce292914feae 9ec86514d5993782d455a4c9717ec4f06d0dfcd556e8de6cf0f8346b8b8629d4 0254abb7ce025ac844429589e0fec98a84ccefae38e8e9807203438e2f387950 dd4c4ee21009701b4a29b9f25634f3eb0f3b7f4cc1f00b98fc55d784815ef35b c4504c579025dcd492611f3a175632e22c2d3b881fda403174499acd6ec39708 1aeab6b568c22d11258fb002ff230f439908ec376eb87ed8e24d102252c83a6e c3536b736c26cd5464c6f53ce8343d3fe540eb699abd05f496dcd3b8b47c5134 90291a2c53970e3d89bacce7b79d5fa540511ae920dd4447fc6182224bbe05c5 8c8965147d5b39cad109b578ddb4bfca50b66838779e6d3890eefc4818c79590 75c0aa897075a7bfa64d8a55be636a6984e2d1a5a05a54f0f01b0eb4653e9c7a 30295311d6289310f234bfff3d5c7c16fd5766ceb49dcb0be8bc33c8426f6dc4 c68e42f416f482d43653f36cd14384270b54b68d6496a8e34ce887687de5b441 80c1e732c745a12ff6623cbf51a002aa4630312e5d590cd60e621e6d714e06de d845688c4631da982cb2e2163929fe78a1d87d8e4b2fe39d2a27c582cfed3e15 |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.