Cybercriminals have launched sophisticated social engineering campaigns targeting seniors across multiple countries, using fake Facebook groups promoting “active senior trips” to distribute a newly discovered Android banking trojan dubbed “Datzbro.”
ThreatFabric researchers identified this threat in August 2025, revealing a coordinated fraud operation spanning Australia, Singapore, Malaysia, Canada, South Africa, and the UK.
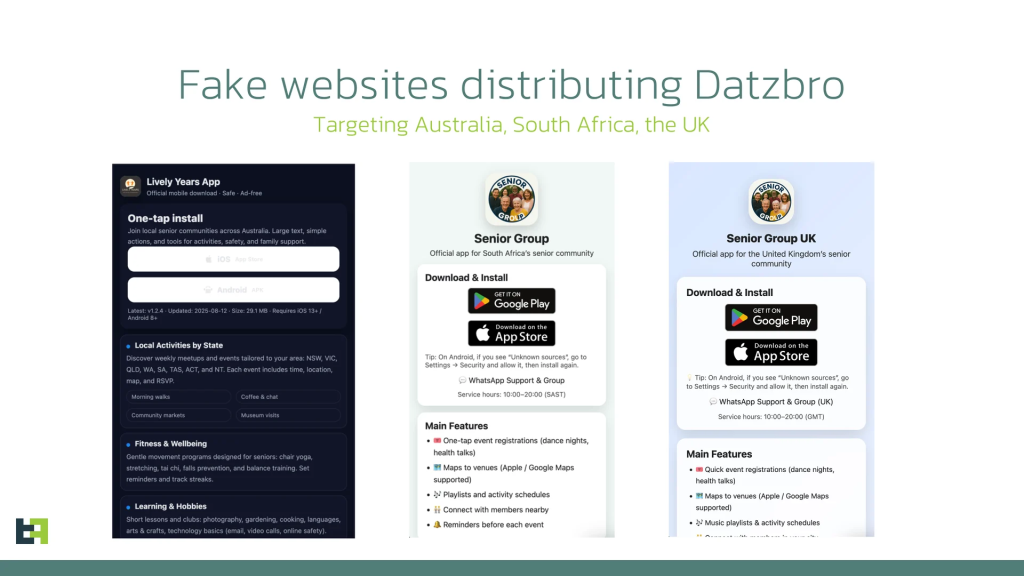
The attack begins with AI-generated Facebook groups featuring seemingly legitimate content about senior social activities, dance events, and travel opportunities. These groups successfully attract genuine engagement from elderly users seeking community activities.
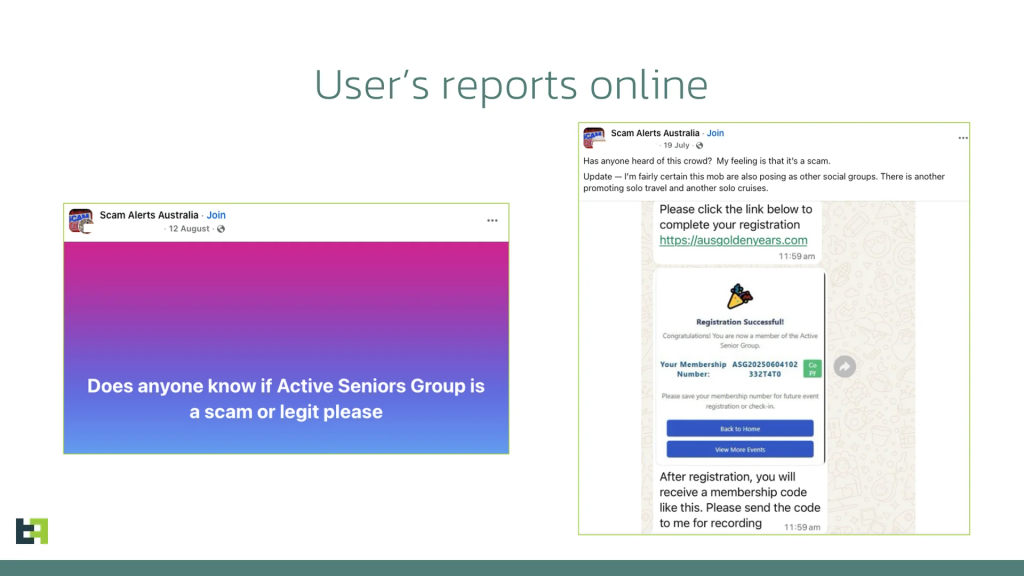
Once victims express interest, fraudsters contact them through Facebook Messenger or WhatsApp, sharing malicious links that appear to be event registration applications.
Advanced Remote Access Capabilities
Datzbro represents a hybrid threat combining traditional spyware functionality with banking trojan capabilities.
The malware leverages Android Accessibility Services to perform comprehensive device takeover operations, including remote screen sharing, interface manipulation, and a unique “schematic” remote control mode that recreates screen layouts for operators when video quality is insufficient.
The Trojan’s most concerning feature is its “black overlay” capability, which displays semi-transparent screens with customizable text to victims while remaining transparent to operators.
This technique effectively conceals fraudulent activities, allowing cybercriminals to access banking applications and steal credentials without detection.
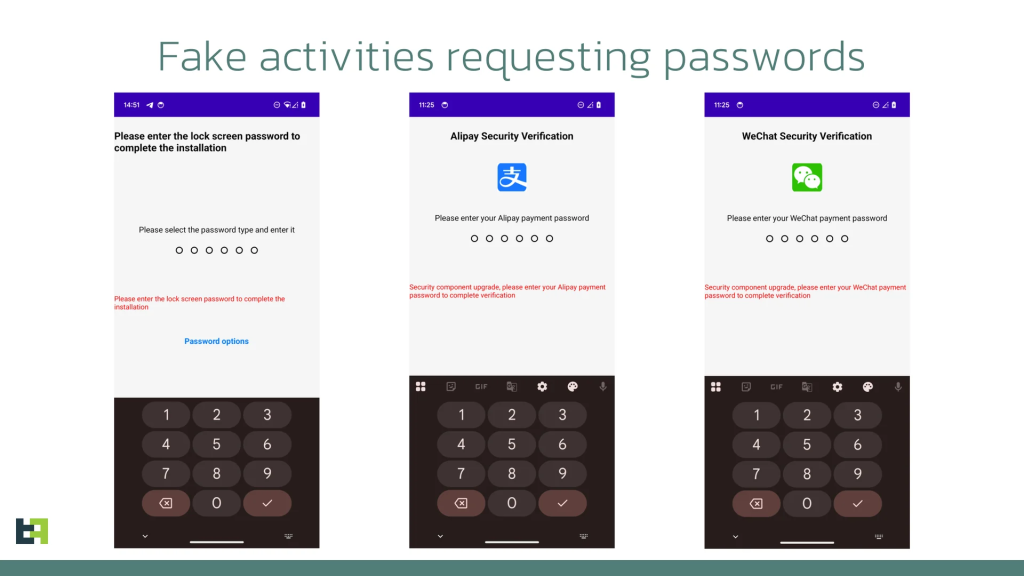
Datzbro specifically targets financial applications through hardcoded filters, monitoring accessibility events for banking and cryptocurrency-related activities.
The malware searches for package names containing terms such as “bank,” “pay,” “Alipay,” “WeChat,” “wallet,” and “finance,” while simultaneously capturing text containing “password,” “PIN,” and verification codes in both English and Chinese.
Chinese Origins and Global Distribution
Analysis reveals Datzbro’s Chinese origins through debug strings and interface elements written in the Chinese language. Researchers discovered samples named “最强远控.apk,” translating to “The most powerful remote control,” indicating the threat actors’ marketing approach.
Unlike typical web-based command and control systems, Datzbro utilizes a desktop application for malware management.
Critically, ThreatFabric’s Mobile Threat Intelligence service identified a leaked version of Datzbro’s command and control application and builder circulating on public virus-sharing platforms.
This development transforms Datzbro from a targeted threat into a globally accessible tool for cybercriminals worldwide.
The malware’s comprehensive feature set includes SMS management, contact manipulation, file system access, camera capture, audio recording, and photo theft capabilities.
It can bypass Android 13+ restrictions using droppers like Zombinder, ensuring successful installation across modern devices.
The discovery of Datzbro highlights the evolution of mobile threats, where social engineering targeting vulnerable populations leads to sophisticated device compromise.
As cybercriminals continue to refine these tactics, combining AI-generated content with advanced malware capabilities, organizations and individuals must maintain heightened vigilance against schemes targeting seniors through trusted social media platforms.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates