SetupHijack, a new open-source security research utility, weaponizes race conditions and lax file handling in Windows installers and updaters to achieve privilege escalation.
By monitoring world-writable directories such as %TEMP%, %APPDATA%, and %USERPROFILE%\Downloads, the tool stealthily replaces installer-dropped executables with attacker-supplied payloads, which execute with elevated rights before integrity checks complete.
Exploiting Race Conditions in Installer Workflows
Many Windows installers and updaters temporarily place executables, MSI packages, or batch scripts in user-writable locations before execution.
SetupHijack runs in the context of a non-privileged user, continuously scanning these directories for new or modified installer files.
When a target file appears, the tool rapidly substitutes it with a custom payload, preserving the original as a backup, creating a time-of-creation/time-of-use (TOCTOU) race window.
If the privileged process executes the hijacked file before verifying its authenticity, the attacker’s payload runs under SYSTEM or Administrator privileges, bypassing conventional user consent controls.
Seamless Payload Substitution via Continuous Polling
Unlike file-system notification-based approaches, SetupHijack employs lightweight polling to detect file drops with minimal dependencies or privileges.
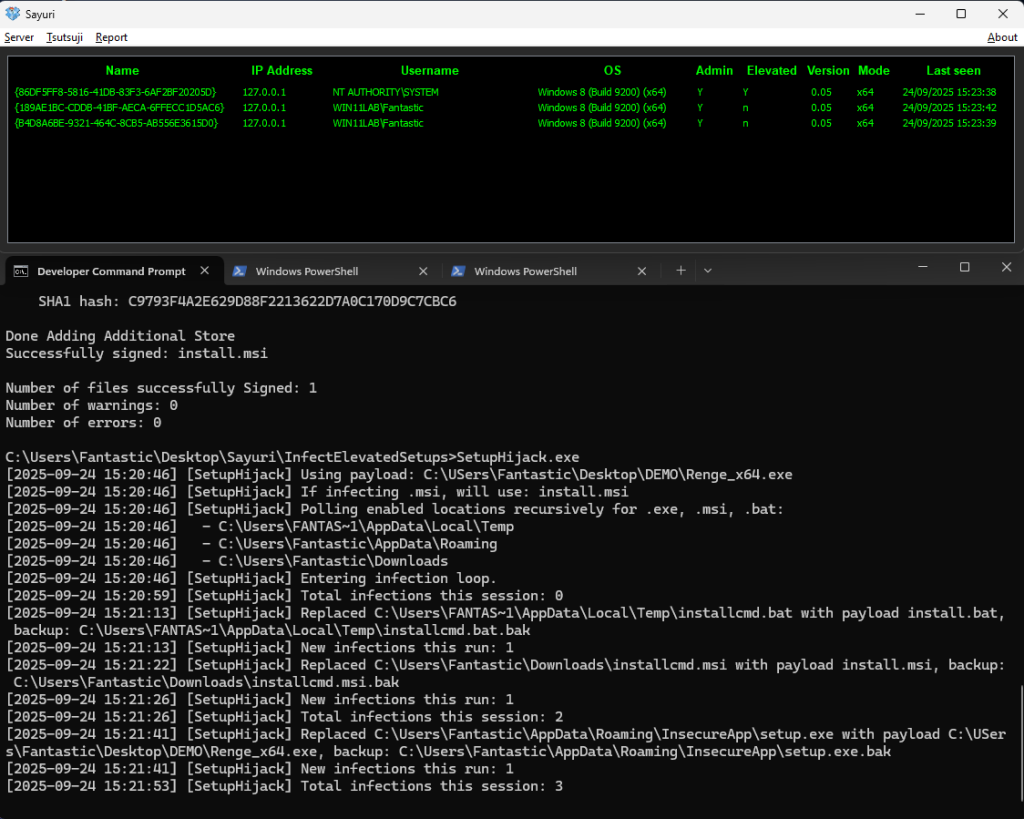
It supports a wide range of installers and file types, including .exe, .msi, and batch scripts (e.g., sysinfo, netstat, ipconfig).
The tool maintains a skiplist to avoid redundant replacements, and logs every action for auditing and debugging.
To enhance success rates, operators can integrate the provided SignToolEx hook to Authenticode-sign payloads with genuine certificates and timestamps, mitigating signature checks that some installers perform.
Operational Use and Security Considerations
SetupHijack is intended strictly for red-team engagements, penetration tests, and controlled research environments.
Running the tool requires no elevated privileges and offers granular control over monitored paths via flags:
- -notemp, -noappdata, -nodownloads disable specific directories
- clean restores original backups
- verbose enables detailed logging
- Specifying a payload executable overrides defaults
An exemplary attack flow involves building the payload (nmake PAYLOAD=c:\path\to\payload.exe), launching SetupHijack, and then initiating a privileged installer.
Real-world tests demonstrated successful infection of Zoom’s installer binaries in %APPDATA%, achieving lateral process spoofing and potential credential theft.
Mitigations and Defensive Recommendations
To guard against TOCTOU installer abuses, organizations should adopt the following practices:
- Restrict installer operations to secure, non-writable locations.
- Enforce integrity checks immediately before execution, including hash or signature validation.
- Monitor process creation events for anomalous child processes spawned from installer contexts.
- Employ application allow-listing that verifies executables by cryptographic hash and publisher.
By combining these measures with least-privilege principles and regular audits of installer behaviors, defenders can neutralize the primary vectors leveraged by SetupHijack.
Nonetheless, this tool underscores the enduring risks of installer races and the need for resilient trust models in software delivery pipelines.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates