A severe privilege escalation vulnerability (CVE-2025-49144) in Notepad++ v8.8.1 allows attackers to gain SYSTEM-level privileges through insecure executable search paths.
The flaw, classified as “High” severity, exploits the installer’s uncontrolled search for dependencies in the current working directory.
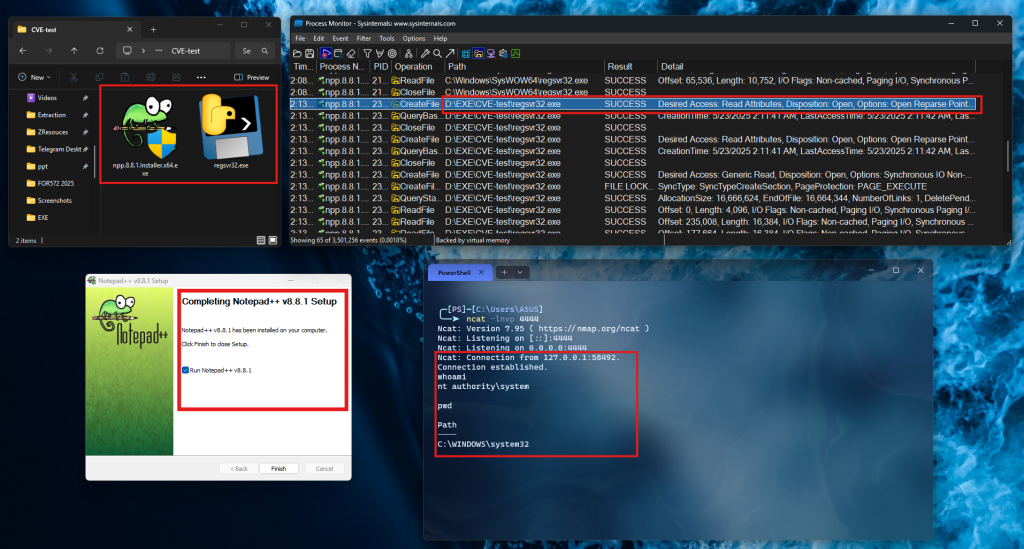
Attackers can plant malicious executables (e.g., regsvr32.exe) in the same directory as the installer, triggering automatic execution with elevated privileges upon installation.
Vulnerability Mechanics and Attack Vector
The vulnerability stems from an uncontrolled EXE/DLL search path (binary planting), where the installer fails to validate executable dependencies.
During installation, the process searches the current directory (e.g., Downloads) for required binaries before checking system paths.
Attackers leverage this by:
- Placing a malicious executable (e.g., disguised as
regsvr32.exe) in a user-accessible directory. - Tricking users into downloading both the legitimate installer and the malicious file to the same location via social engineering or clickjacking.
- Executing the installer, which automatically loads the malicious binary with NT AUTHORITY\SYSTEM privileges.
Proof-of-concept exploits demonstrate successful privilege escalation, including the ability to establish a reverse shell and gain complete system control.
According to researchers, the vulnerability could potentially allow an attacker to execute a malicious file with SYSTEM-level privileges. However, exploitation requires specific conditions: the attacker must either have local access to the system or successfully trick a user, through methods such as social engineering or clickjacking into downloading both the official Notepad++ installer and a specially crafted malicious executable into the same folder, typically the user’s Downloads directory.
Once the installer is launched from that location, it may inadvertently execute the attacker’s file due to the vulnerable search path, resulting in the escalation of privileges.
Users are advised to download installers from trusted sources and avoid running installation files from shared or untrusted directories. The Notepad++ development team is expected to address this issue in upcoming updates.
Technical Root Cause and Patching
The flaw originates in the installer’s use of relative paths for critical operations. Specifically, the vulnerable code invoked regsvr32 without absolute path specification:
textExecWait 'regsvr32 /u /s "$INSTDIR\NppShell_01.dll"' // Vulnerable
This allowed hijacking via malicious binaries in the working directory. The patch (v8.8.2) enforces absolute paths:
textExecWait '$SYSDIR\regsvr32.exe /u /s "$INSTDIR\NppShell_01.dll"' // Secure
The fix aligns with Microsoft’s secure library loading guidance, ensuring dependencies load exclusively from System32.
Security Implications and Mitigations
Successful exploitation enables:
- Arbitrary code execution with SYSTEM privileges.
- Data theft and lateral network movement.
- Persistent access via compromised systems.
Users must immediately upgrade to v8.8.2. Developers should:
- Use absolute paths for all executable dependencies.
- Implement digital signature verification for loaded binaries.
- Create secure temporary directories with randomized names.
This vulnerability underscores critical risks in software distribution workflows, emphasizing rigorous path validation to prevent binary planting attacks.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates