ShadowV2 represents a new breed of cybercrime-as-a-service, combining traditional malware techniques with cloud-native tooling and a complete operator interface.
Darktrace’s latest investigation revealed that threat actors are leveraging GitHub CodeSpaces and AWS EC2–hosted Docker daemons to orchestrate large-scale DDoS campaigns, all managed through a Python-powered backend and a polished web UI.
At the heart of ShadowV2 is a Python-based command-and-control (C2) framework that leverages the Docker SDK for Python to spawn containers directly on exposed AWS EC2 instances.
Attackers first create a “setup” container from a generic Ubuntu image, install the necessary tools, and then image it for deployment, passing malware arguments via environment variables.
This build-on-victim approach likely aims to minimize forensic artifacts by performing container assembly on the compromised host.
ShadowV2’s RAT and Spreader Components
The initially deployed spreader is a Python script hosted on GitHub CodeSpaces, as evidenced by HTTP headers such as docker-sdk-python/7.1.0 and X-Meta-Source-Client: github/codespaces. Once a container is running, it drops an unstripped ELF binary written in Go under /app/deployment.
This Go binary implements RESTful registration and polling endpoints, sending implant heartbeats every second to https://shadow.aurozacloud[.]xyz/api/vps/heartbeat and polling for commands every five seconds.
Each implant identifies itself via a unique VPS_ID, which is a concatenation of the container name and the current Unix timestamp, ensuring persistent session tracking.
Modular DDoS Capabilities and Evasion Techniques
Beyond basic HTTP floods, ShadowV2 supports advanced attack modes, including HTTP/2 rapid reset and a Cloudflare Under Attack Mode (UAM) bypass.
The UAM bypass utilizes a bundled headless Chrome instance via ChromeDP to solve JavaScript challenges and extract clearance cookies, although headless browsers often trigger additional CAPTCHAs.
The rapid reset mode exploits HTTP/2 multiplexing limits by issuing and immediately canceling streams, maximizing request throughput per connection. Additional evasion flags include randomized query strings, spoofed forwarding headers, and optional proxy chains.
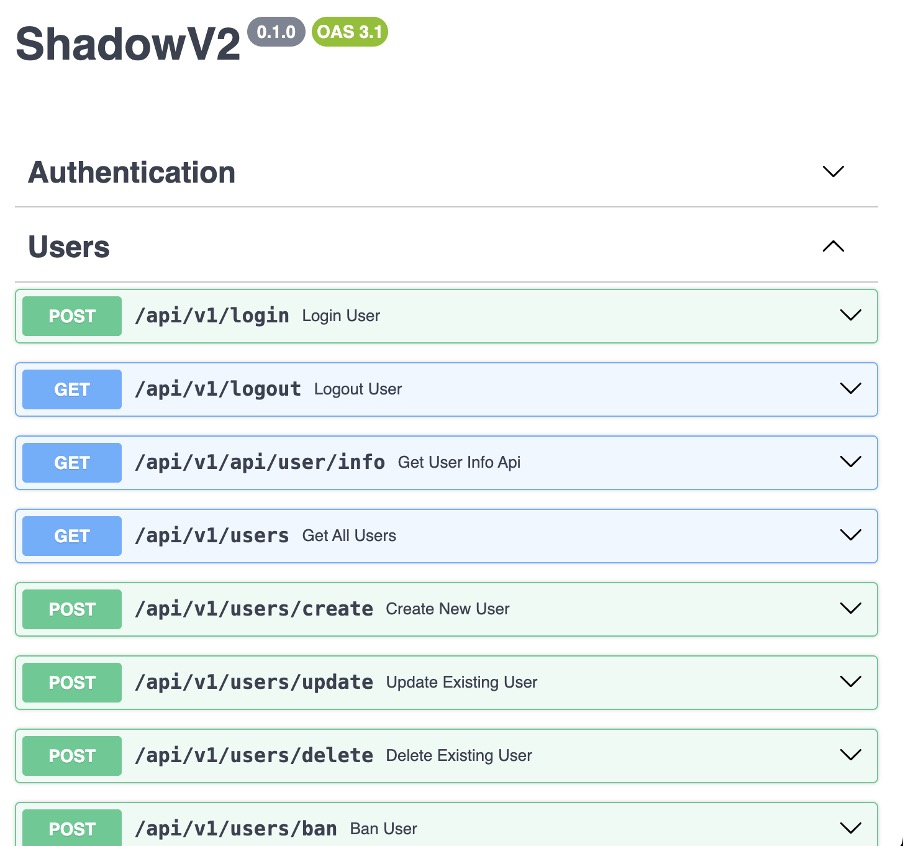
API-Driven Multi-Tenant Platform
ShadowV2’s FastAPI- and Pydantic-based backend once exposed a full OpenAPI specification, complete with Swagger UI documentation.
Although Darktrace researchers obtained a snapshot of the API before it was taken offline, the endpoints reveal multi-tenant DDoS-as-a-service functionality, including user authentication, privilege levels that distinguish between admin and regular user actions, and configurable attack parameters.
Unusually, the “start attack” endpoint requires clients to supply a list of zombie hosts, suggesting operators maintain custom bot inventories.
Administrative functions include creating new user accounts and managing blacklists of forbidden targets, which can help avoid collateral damage or upsell protection services.
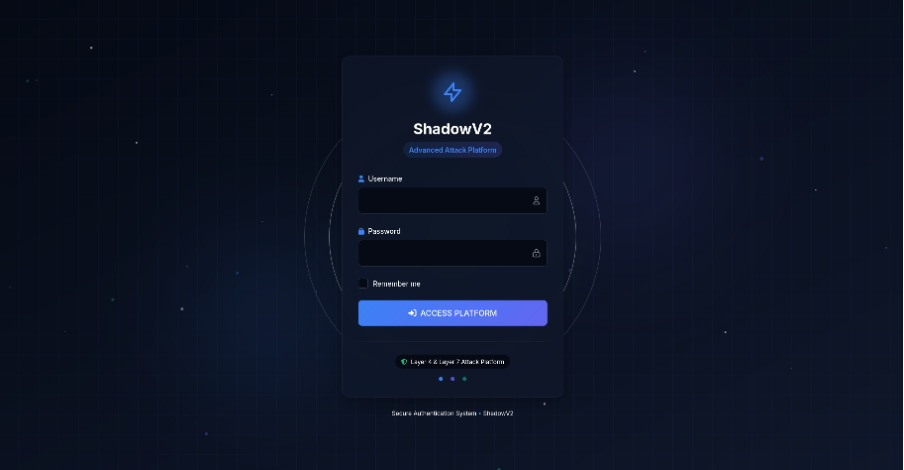
Operator UI Resembles Legitimate Cloud Service
Visiting the ShadowV2 C2 domain now returns a likely fabricated seizure notice, but the /login path still serves a Tailwind-styled login page describing an “Advanced Attack Platform.”
The high-quality interface and RESTful API design underscore how malware platforms increasingly adopt software engineering best practices, making them more user-friendly for non-technical operators.
To counter platforms like ShadowV2, organizations must monitor container orchestration and cloud workload behavior, enforce strict network access controls on Docker APIs, and deploy behavioral analytics to detect anomalous API calls and container creation patterns.
Continuous visibility into cloud metadata and proactive threat hunting for unexpected container spins can help identify compromise before a DDoS operation is launched.
Advanced attack platforms, such as ShadowV2, demonstrate that modern malware is no longer just code it’s a full-featured service, requiring defenders to rethink traditional perimeter-based defenses.
IoCs
Malware hashes (SHA256)
● 2462467c89b4a62619d0b2957b21876dc4871db41b5d5fe230aa7ad107504c99
● 1b552d19a3083572bc433714dfbc2b75eb6930a644696dedd600f9bd755042f6
● 1f70c78c018175a3e4fa2b3822f1a3bd48a3b923d1fbdeaa5446960ca8133e9c
C2 domain
● shadow.aurozacloud[.]xyz
Spreader IPs
● 23.97.62[.]139
● 23.97.62[.]136
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates