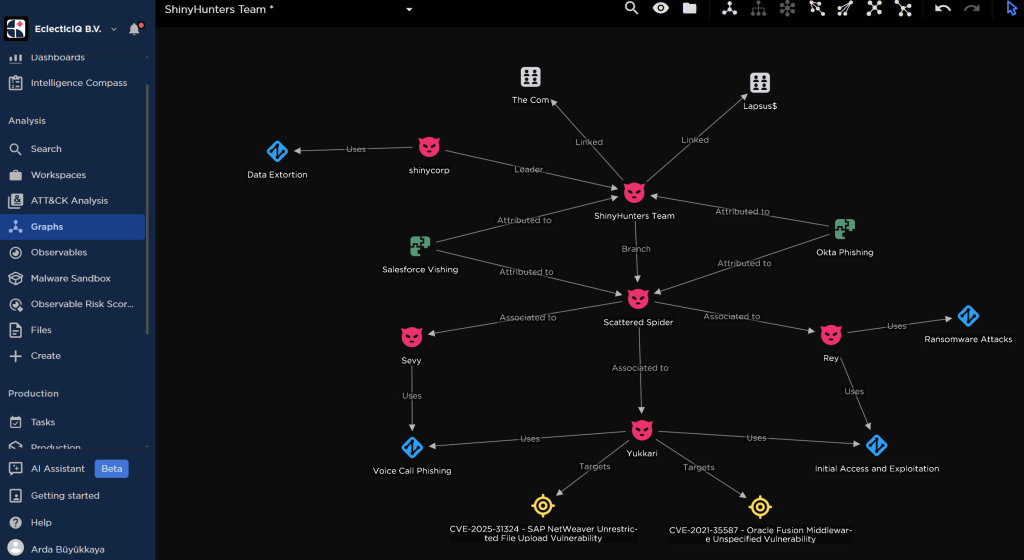
ShinyHunters, the financially motivated eCrime syndicate notorious for large-scale data extortion, has expanded its tactics in 2025 to include AI-enabled voice phishing, supply chain compromises, and the recruitment of malicious insiders.
By collaborating with Scattered Spider and The Com affiliates, the group now launches sophisticated vishing campaigns against SSO platforms in retail, airline, and telecom sectors, exfiltrates massive customer datasets, and prepares to deploy the new “shinysp1d3r” Ransomware-as-a-Service (RaaS) targeting VMware ESXi environments.
AI-Enabled Vishing Scaled through Voice Agents
ShinyHunters leverages VoIP services Twilio, Google Voice, and 3CX alongside AI voice platforms such as Vapi and Bland AI to automate adaptive social engineering calls.
Bland’s built-in LLM dynamically generates human-like dialogue, adjusting tone, accent, and narrative in real time to manipulate targets.
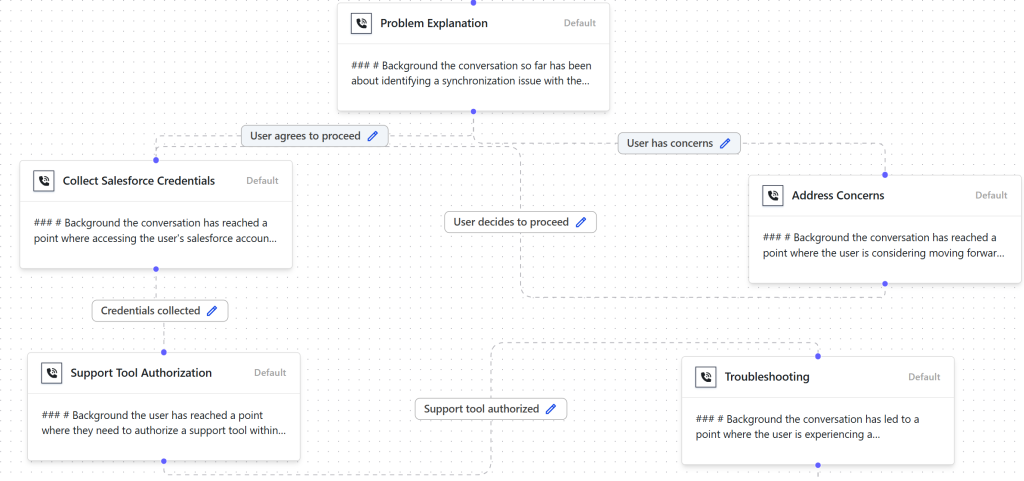
Scattered Spider affiliates guide victims through OAuth flows on Salesforce, Okta, and Microsoft 365 via voice calls, tricking employees into authorizing malicious applications.
Once access is granted, attackers exfiltrate customer data up to 26 GB of user accounts and 16 GB of contact records from airline victims and threaten seven-figure extortion demands, often publicizing stolen samples on LimeWire to pressure organizations.
Supply Chain Attacks and Insider Recruitment
To infiltrate CI/CD pipelines, ShinyHunters recruits insiders via Telegram channels, offering financial rewards to employees and contractors with access to Git repositories, BrowserStack, and remote management tools like ConnectWise ScreenConnect.
Leaked BrowserStack API keys provide footholds in testing environments, while stolen Cloudflare Zero Trust tokens suggest plans to expand network compromise.
This insider access enables ShinyHunters to embed malicious code in software builds and propagate supply chain attacks, compromising numerous enterprise systems through a single point of entry.
Emerging Shinysp1d3r RaaS Threatens ESXi Infrastructure
EclecticIQ analysts confirm that shinysp1d3r RaaS is under development, designed to encrypt VMware ESXi hypervisor clusters. Once operational, affiliates will deploy ransomware payloads across virtualized datacenters, disrupting critical business operations and amplifying extortion leverage.
Medium-confidence projections indicate that shinysp1d3r will attract affiliates seeking specialized ransomware tools for enterprise virtualization targets, broadening ShinyHunters’ reach beyond data theft.
ShinyCorp, the group’s leader, actively trades stolen datasets with ransomware affiliates Angel RaaS, DragonForce, and Lapsus$ via Telegram and qTox, fetching prices exceeding $1 million per corporate dataset.
Cross-membership with actors like Yukari and Sevy facilitates SIM swapping, brute-force VPN attacks, and CVE-based exploits (e.g., Oracle Access Manager CVE-2021-35587), enabling breaches of banks, automakers, and telecom providers.
Enterprises must enforce least-privilege access on SSO-connected applications, restrict mass-export permissions, and audit OAuth integrations. AI-driven anomaly detection within Salesforce Shield and Okta ThreatInsight can flag unusual data exports.
Insider threat defenses such as honeypots, strict role-based access, and SIEM/SOAR alerts for anomalous API key usage are essential. Employee training should include voice-based phishing simulations and challenge-response verification for high-risk requests.
As ShinyHunters professionalizes with AI-driven vishing and VMware-targeted ransomware, organizations must urgently harden cloud-centric security controls and incorporate insider threat scenarios into their risk models to thwart these evolving extortion tactics.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates