The Trellix Advanced Research Center has uncovered a new SideWinder APT campaign that leverages a PDF and ClickOnce-based infection chain to infiltrate South Asian government targets.
This marks a significant evolution from the group’s previously known Microsoft Word exploit vectors, indicating a shift in strategy designed to bypass detection and exploit geopolitical targets through enhanced social engineering and software sideloading.
Sophisticated Multi-Stage Attack Chain
According to Trellix researchers Ernesto Fernández Provecho and Pham Duy Phuc, the September 2025 campaign targeted diplomats from Sri Lanka, Pakistan, Bangladesh, and an unnamed European embassy in New Delhi.
Attackers distributed phishing emails using diplomatic and government-themed documents such as “Relieving order New Delhi.pdf” or “Inter-ministerial meeting Credentials.pdf”.
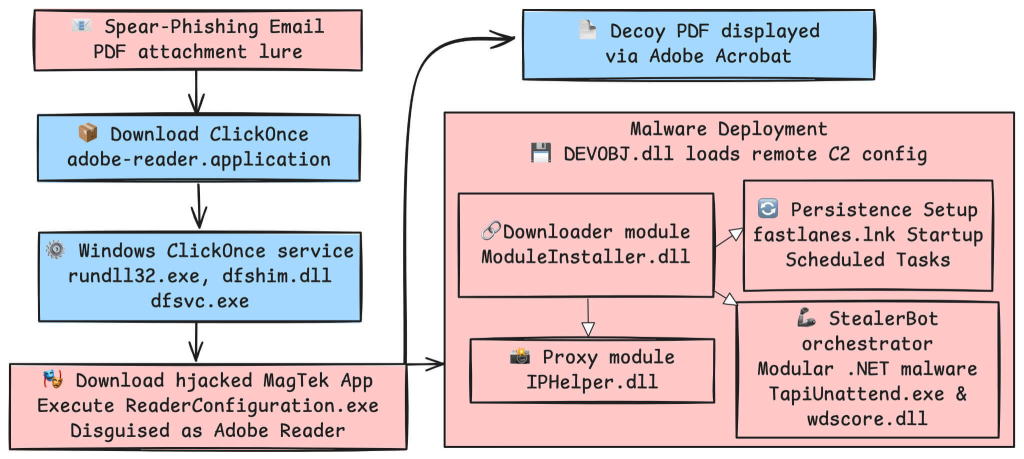
Upon clicking the embedded “Update Adobe Reader” button in the malicious PDF, victims unknowingly downloaded a ClickOnce application, which masqueraded as an Adobe Reader installer, from attacker-controlled domains like mofa-gov-bd[.]filenest[.]live.
The ClickOnce app, signed with a legitimate MagTek Inc. certificate, side-loaded a malicious DLL to deliver ModuleInstaller and StealerBot payloads.
Trellix’s analysis showed the threat actor exploited a weakness in Microsoft’s ClickOnce installation process. In contrast, Windows verifies the main application’s signature; additional dependencies downloaded during installation bypass signature checks.
SideWinder exploited this by embedding a malicious DLL named DEVOBJ.dll, replacing legitimate configuration files such as DeviceImages.json with trojanized binaries.
Sideloading and Evasion Tactics
The DEVOBJ.dll payload decrypted an embedded component using a 42-byte XOR key, which loaded a . NET-based downloader (App.dll) responsible for fetching the next stage malware ModuleInstaller.dll.
This module collected system data and fetched encrypted “configuration” files, which included the final StealerBot component.
ModuleInstaller used legitimate Windows executables like TapiUnattend.exe to sideload malicious libraries (wdscore.dll, IpHelper.dll) and establish persistence in %appdata%\fastlanes.
Trellix identified deliberate obfuscation methods, including dynamic URL generation, region-based geofencing, and short-lived payload hosting, designed to frustrate analysis and prevent sample retrieval by researchers outside South Asia.
The APT’s infrastructure relied heavily on fake government-themed domains such as cabinet-gov-pk[.]dytt888[.]net and www-treasury-gov-lk[.]snagdrive[.]com. These domains were actively rotated between campaign waves, each lasting a few weeks.
Trellix attributes the campaign to SideWinder with high confidence due to overlapping infrastructure, use of proprietary tools, and consistent targeting patterns.
The operation underscores the group’s increasing technical maturity and commitment to espionage through highly tailored lures and legitimate-signed malware delivery.
This campaign exemplifies the growing trend of adversaries weaponizing trusted mechanisms like ClickOnce and legitimate code-signing to propagate espionage malware while evading traditional endpoint defenses.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates