Security researchers at SentinelLABS have uncovered a sophisticated cryptocurrency scam operation that has drained over $900,000 from victim wallets using malicious smart contracts disguised as trading bots.
The campaign leverages aged YouTube accounts and AI-generated content to create false legitimacy while distributing weaponized Solidity contracts through social media platforms.
Advanced Obfuscation Techniques Hide Attacker Wallets
The threat actors employ multiple sophisticated obfuscation methods to conceal their wallet addresses within the malicious smart contracts, making detection significantly more challenging. Researchers identified three primary techniques used across different contract variations.
The most complex method involves XOR operations between two 32-byte constants with misleading names, such as “DexRouter” and “factory”.
When victims deploy the contract, these constants are XOR’ed together using the expression address(uint160(uint256(a) ^ uint256(b))) to reveal the attacker’s Externally Owned Account (EOA).
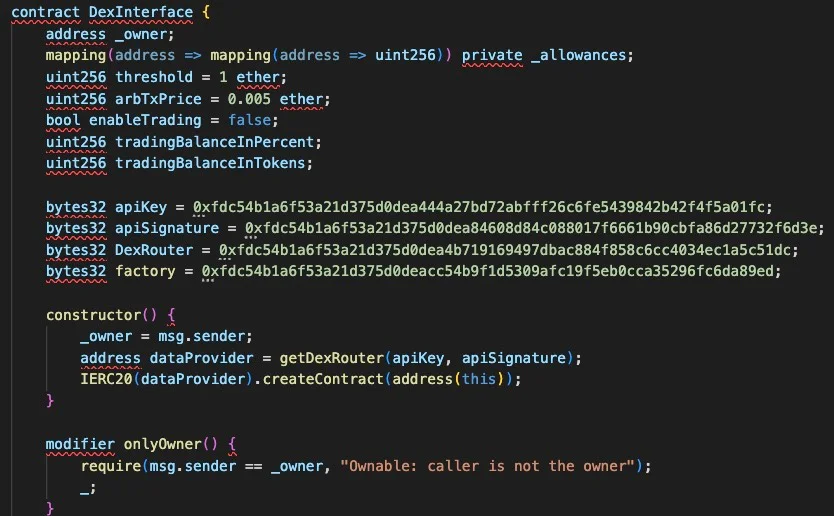
This technique consistently resolved to the same wallet address: 0x872528989c4D20349D0dB3Ca06751d83DC86D831.
Additional obfuscation methods include string concatenation, where address fragments are assembled as strings, and large decimal-to-hex conversion that transforms 256-bit integers to uint160 data types, effectively removing high bytes to reveal Ethereum wallet addresses.
These techniques ensure that even security-conscious users examining the source code cannot immediately identify the malicious destination addresses.
YouTube Distribution Network Employs AI-Generated Content
The scam operation utilizes a network of aged YouTube channels to distribute tutorial videos explaining how to deploy the malicious contracts as legitimate Maximum Extractable Value (MEV) trading bots.
The most successful video, posted by user @Jazz_Braze titled “How to Create Passive Income MEV Bot on Ethereum Full Tutorial,” generated over $900,000 in stolen funds and accumulated more than 387,000 views.
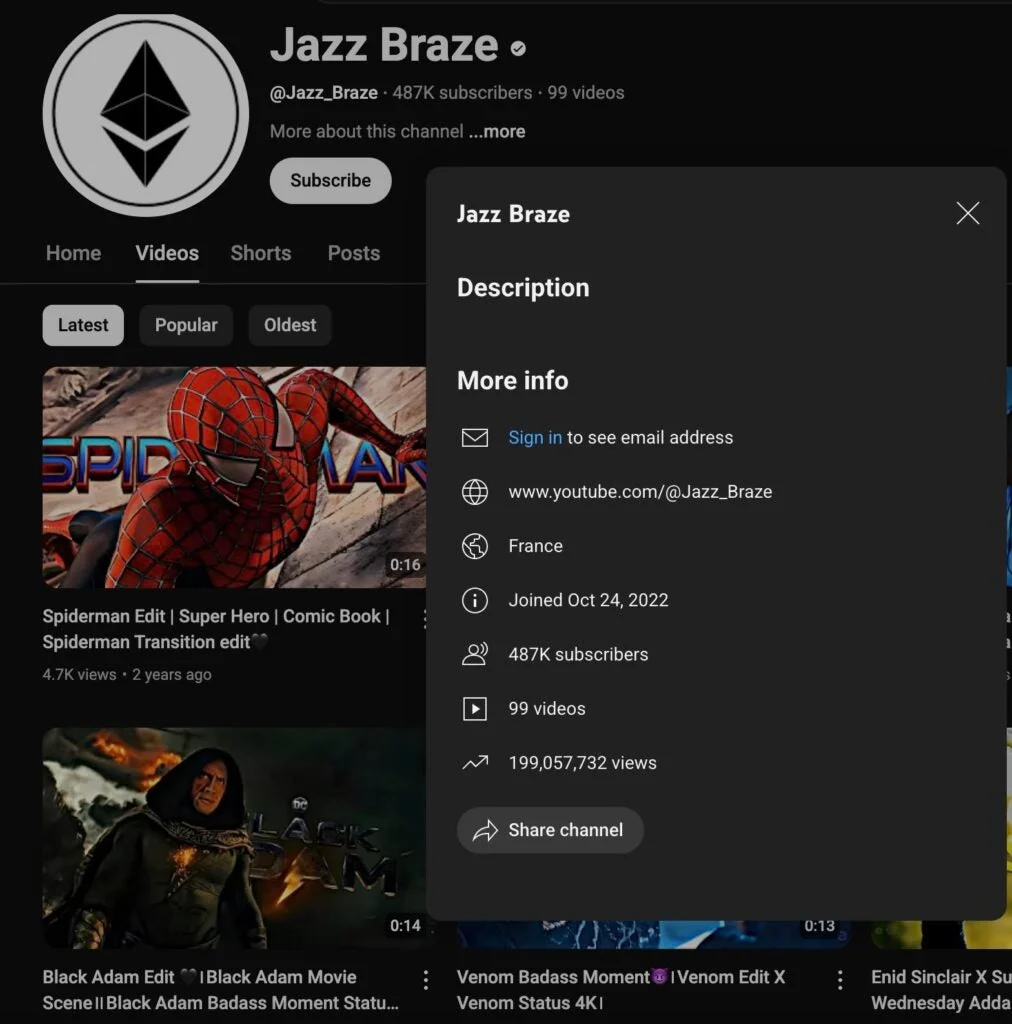
Several videos exhibit clear indicators of AI generation, including robotic voice patterns, inconsistent speech pacing, and unnatural facial movements where narrators only look directly at the camera.
The attackers likely use YouTube’s comment management features to filter negative feedback and promote fake positive testimonials.
The threat actors invest considerable effort in account aging, with some channels posting unrelated pop culture content over extended periods to build algorithmic credibility.
Services selling aged YouTube accounts are readily available on Telegram and through search engines, with prices ranging from $6 to thousands of dollars.
Analysis of blockchain transactions reveals varying degrees of success across different campaigns, with the most recent scam from April 2025 collecting 7.59 ETH (approximately $28,000).
Security experts recommend that cryptocurrency users exercise extreme caution when encountering trading tools promoted through unverified social media content and thoroughly analyze smart contract code before deployment.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates