A recent surge in targeted phishing attacks has placed Turkish defense and aerospace companies in the crosshairs of cybercriminals deploying the Snake Keylogger variant.
Under the guise of official contractual correspondence from Turkish Aerospace Industries (TUSAŞ), threat actors have crafted elaborate email campaigns designed to dupe enterprise recipients into executing weaponized attachments.
The malicious payload masquerades as legitimate documents most notably through filenames such as “TEKLİF İSTEĞİ – TUSAŞ TÜRK HAVACILIK UZAY SANAYİİ_xlsx.exe” in order to blend seamlessly into business communications within this high-stakes industry sector.
Persistence Techniques
Once unleashed on a victim’s system, this Snake Keylogger variant leverages a sophisticated suite of anti-detection and persistence strategies.
Initial analysis, validated by deep static and dynamic investigation, reveals that the sample is a .NET-based PE32 executable.
Upon execution, it rapidly attempts to bypass native Windows defenses by invoking PowerShell commands, specifically instructing the system to whitelist its own path within Windows Defender’s exclusion list.

Simultaneously, it employs process injection techniques to maintain stealth and evade security controls, as extensively observed in the Threat.Zone platform’s syscall monitoring.
Additionally, the malware ensures persistence through scheduled tasks, automatically configuring itself to re-execute at startup.
According to Malwation Report, the audit trail confirms that the executable spawns schtasks.exe to accomplish this, persistently embedding itself within the operational fabric of compromised endpoints.
At the core of its obfuscation is a multi-layered (matryoshka-style) payload delivery method, where benign-looking functionality a temperature converter application built with Windows Forms serves as a decoy while the main malicious logic is reflexively loaded and executed in-memory.
Chiron Unpacker, a dynamic .NET analysis utility, was instrumental in unpacking the secondary stage resource (named “Remington”), which encapsulates the true capabilities of the Snake Keylogger.
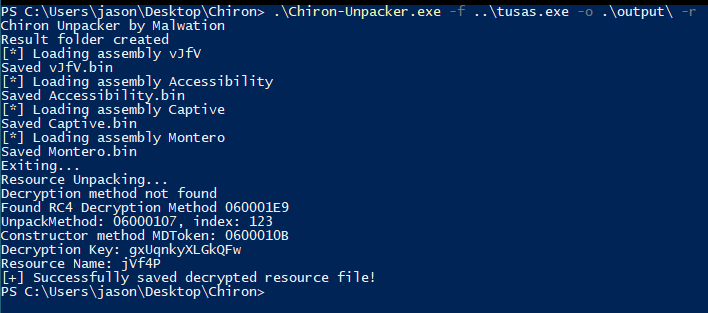
Multichannel Credential Theft
Snake Keylogger’s principal function is exfiltration of sensitive data at scale. Armed with modules to harvest credentials, cookies, autofill data, download histories, and credit card information from an exhaustive list of Chromium and Mozilla-based browsers inclusive of Chrome, Firefox, Edge, Brave, and over two dozen lesser-known variants the malware also targets email clients such as Outlook, FoxMail, and ThunderBird.
It systematically scours registry keys and local storage to extract and decrypt stored credentials, applying custom cryptographic functions to defeat data-at-rest protections.
Anti-sandbox techniques are also interspersed throughout its code, purpose-built to thwart automated analysis by cross-referencing its execution environment against known sandbox IP addresses.
For exfiltration, this campaign prefers SMTP as the command-and-control (C2) channel: credentials for the mail server are DES encrypted within the binary, successfully decrypted using analyst-supplied scripts to reveal hard-coded operational infrastructure.
Data flows from victim environments directly to the attacker-controlled mailbox, using a rogue domain (htcp.homes) over port 587.
In response, security teams can now leverage a freshly minted YARA signature, specifically tuned to detect .NET binaries protected with Cassandra and exhibiting entropy profiles consistent with this campaign’s obfuscated payloads.
The campaign’s operational footprint including file hashes from all observed stages is being actively disseminated through Turkey’s National Computer Emergency Response Team (USOM), with rapid coordination underway to notify exposed victims and stem further breaches.
The technical intelligence released thus far provides defenders with actionable details to tighten perimeter and endpoint restrictions, alongside tools to automate discovery of similar threats.
This campaign underscores the escalating sophistication of credential-theft toolkits in targeted spear-phishing, and highlights the critical need for defense-in-depth, timely threat intel sharing, and vigilant user education in high-risk enterprise environments.
Key Indicators of Compromise (IoCs)
| Filename | SHA256 Hash |
|---|---|
| Montero | 3c9cddf85962249a967b3827e3edb4acb710dc0e3088c619342e2ce6df35bfbc |
| vJfV | 82fa8156e9d4fb47cd20908818b9172f86ed13eb683041658f242c58ce0a9cff |
| jVf4P | 2859b8700fc6111c40b806d114c43e2e3b4faa536eeab57d604818562905b911 |
| Captive | 11f577cc6b6af304332d47fba2122ffb193e81378662ea7093ebe971107d89d6 |
| TEKLİF İSTEĞİ – TUSAŞ TÜRK HAVACILIK UZAY SANAYİİ_xlsx.exe | 0cb819d32cb3a2f218c5a17c02bb8c06935e926ebacf1e40a746b01e960c68e4 |
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant updates