Steam has officially confirmed that a recent update to the popular indie game BlockBlasters contained malicious code, following widespread player reports and security scans that flagged unusual activity within the game’s files.
The discovery has prompted Steam to remove the title from its storefront and disable access for all users until the issue is fully resolved, raising fresh concerns about the security of digital game distribution platforms and third-party integrations.
Background of the Incident
BlockBlasters, which launched earlier this month, quickly garnered praise for its vibrant graphics, inventive level designs, and streamlined controls.
Players celebrated the title’s fast-paced arcade action and community-driven map creations.
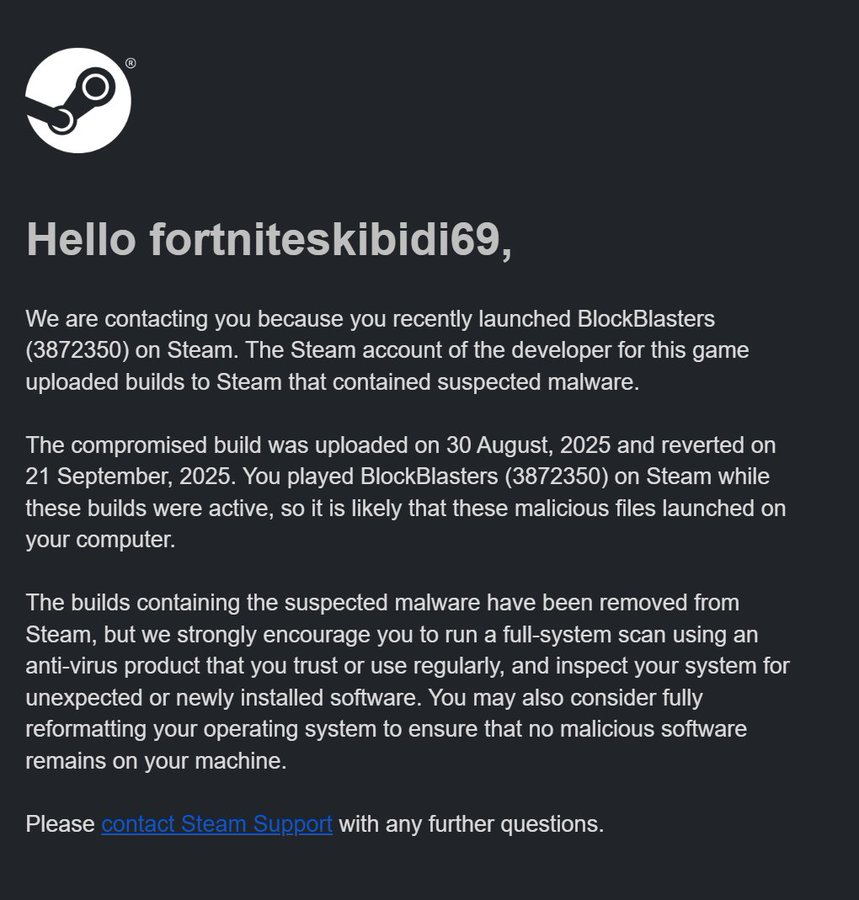
However, on September 23, several users on social media and community forums reported that Steam’s built-in virus scanner had detected malicious components in the game installation.
Early analyses by security enthusiasts suggested the malware had been introduced via a third-party ad management plugin incorporated by the developer to monetize free gameplay.
The plugin allegedly connected to an external server without proper encryption, risking interception of user data.
Investigations revealed that after applying the update released on September 20, some gamers encountered unexpected pop-up windows and noticeable system slowdowns.
Concerned users captured and shared logs showing unauthorized network requests originating from the game’s process.
As chatter escalated, Steam’s security team initiated a formal review of BlockBlasters’ executable and associated libraries.
On September 24, Steam issued a public statement acknowledging the malware discovery.
The platform temporarily delisted BlockBlasters and disabled access to existing installations.
Steam emphasized that the malicious code was not part of the original game design but was introduced through the third-party plugin.
In their notice, Steam pledged to work directly with the developer to remove the offending code and release a sanitized version of the game.
They also announced plans to enhance their scanning protocols for third-party components, including more rigorous checks for ad frameworks and external libraries.
Steam’s security team urged developers to proactively audit all plugins and scripts that interact with player systems and to ensure secure communication channels.
The platform reaffirmed its commitment to preventing similar incidents by refining its vetting processes and offering updated guidelines for safely integrating external modules.
Protective Measures for Players
Players who downloaded or played BlockBlasters between September 20 and 24 are advised to take immediate precautions.
First, uninstall the game and remove any residual files from the installation directory.
Next, perform a comprehensive antivirus and anti-malware scan using up-to-date security software to detect and eliminate any lingering threats.
Users should also change passwords for accounts accessed from the affected device during the period in question and enable two-factor authentication on critical services.
If unusual activity persists after these steps, consulting a cybersecurity professional for an in-depth system inspection is recommended.
Steam has confirmed that a thoroughly audited, malware-free version of BlockBlasters will be reinstated on the store only after passing all security checks.
In the interim, players should avoid downloading unofficial patches or reuploaded copies of the game.
Steam’s swift intervention underscores the vital importance of robust security checks for digital content and the shared responsibility of platforms, developers, and gamers to maintain a safe gaming ecosystem.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates