A notable rise in phishing campaigns leveraging spoofed Microsoft SharePoint domains and advanced Sneaky2FA techniques has been observed, signaling evolving attacker tactics and an escalating threat landscape.
Recent intelligence highlights a consistent escalation in malicious domain registrations and campaigns exploiting legitimate hosting services to harvest Microsoft credentials from unsuspecting users.
Consistent Domain Patterns Point
Threat analysts detected a significant increase in domains mimicking official Microsoft SharePoint infrastructure.
The malicious domains exhibit highly structured and repeatable naming conventions. Each third-level subdomain preceding the “-mysharepoint” segment features a 29-character alphanumeric sequence, where only specific numeric characters vary across the domain set.
The “-mysharepoint” portion itself remains static, while second-level domain labels are crafted to evoke authentic, US-based organizational resources such as tahofire (tied to tahoelivingwithfire.com), fencecorps (fencecorp.us), or laborers551 (laborers155.org).
All previously identified domains in this wave use the .org TLD, further cementing the illusion of legitimacy.
This level of uniformity in structure offers defenders a valuable vector for threat hunting, allowing the construction of targeted Threat Intelligence (TI) lookup queries such as domainName:"*-mysharepoint.*.org".
Utilizing this approach, security teams identified over 40 instances of matching sandbox analyses, consolidating evidence of an organized and systematic campaign.
Abuse of Legitimate Platforms
Alongside domain spoofing, threat actors are increasingly abusing reputable platforms like Alboompro.com a legitimate service for creating web portfolios and landing pages as a launch pad for phishing lures.
Since May, more than 250 suspected phishing tasks involving Alboompro subdomains have surfaced, with over 130 distinct malicious subdomains observed.
A typical attack flow involves an initial phishing email masquerading as a trusted entity, providing a link that appears to grant access to a document hosted on an Alboompro subdomain designed to resemble a real business (for example, midwesthose-specialty[.]alboompro.com mimics midwesthose.com).
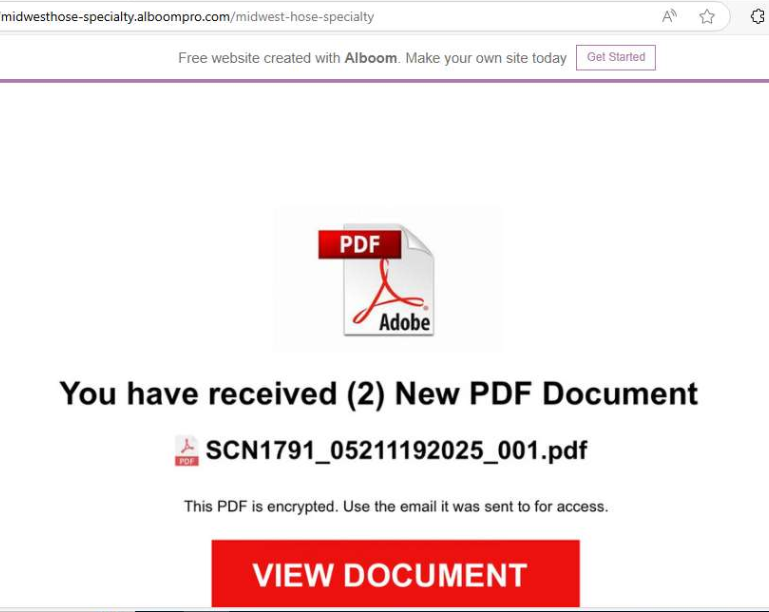
On clicking the embedded link, victims are redirected to a malicious SharePoint-themed page, often requiring them to solve a CAPTCHA to proceed.
The subsequent login interface faithfully mirrors the official Microsoft authentication experience, but is, in reality, rendered through an attacker-controlled proxy server.
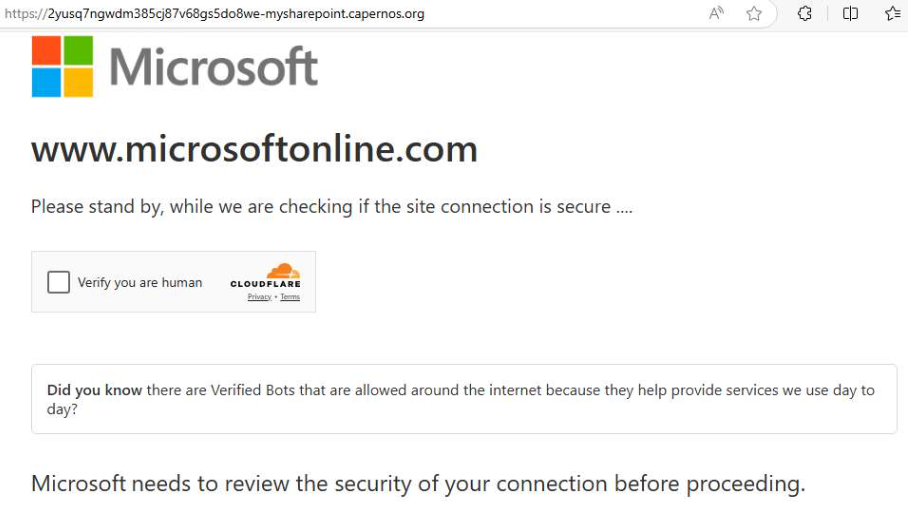
This methodology exemplifies Sneaky2FA attacks, where legitimate login content is proxied, enabling attackers to intercept credentials including authentication tokens or 2FA codes without arousing user suspicion. The victim is provided with a flawless user interface, while credentials are seamlessly siphoned off in real time.
The broad adoption of legitimate cloud and content hosting services for phishing purposes poses a growing challenge to enterprise security teams.
According to the Report, The ongoing abuse of Alboompro.com alone underlines the ease with which professional-looking attack infrastructure can be assembled using widely available, trustworthy services.
Combined with the recurring, programmatically-generated domain structure targeting SharePoint, these tactics greatly increase the likelihood of user compromise, especially in environments where cloud single sign-on (SSO) is broadly deployed.
Continuous monitoring and pattern-based detection of both malicious domain structures and credible service abuse are now essential for defense.
As threats evolve toward highly targeted and technically sophisticated phishing, integrating robust TI lookups and sandboxing tools becomes paramount in proactively neutralizing emerging campaigns.
The surge in SharePoint-themed phishing, leveraging predictable naming conventions and Sneaky2FA proxies, coupled with the widespread exploitation of trusted platforms like Alboompro, underscores the urgent need for adaptive, intelligence-driven defenses.
Cybersecurity practitioners are advised to intensify monitoring and leverage domain-pattern-based threat detection methodologies to stay ahead of these evolving attack vectors.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates