Late August saw a surge in highly targeted social engineering attacks across Latin America that deliver AsyncRAT via oversized SVG images, highlighting a significant evolution in phishing tactics.
While the lure’s courtroom-themed emails echo traditional urgency-driven scams, the multi-stage payload delivery and AI-generated customization distinguish this campaign.
SVG-Based Attacks Let Hackers Deliver Malicious Payloads Undetected
The attack chain begins with a spear-phishing email impersonating a judicial authority. The message warns of imminent lawsuits or court summons, prompting recipients to open an attached SVG file often exceeding 10 MB.
Unlike typical vector images, these SVGs contain embedded JavaScript and XML directives that render an interactive mock portal directly in the web browser.
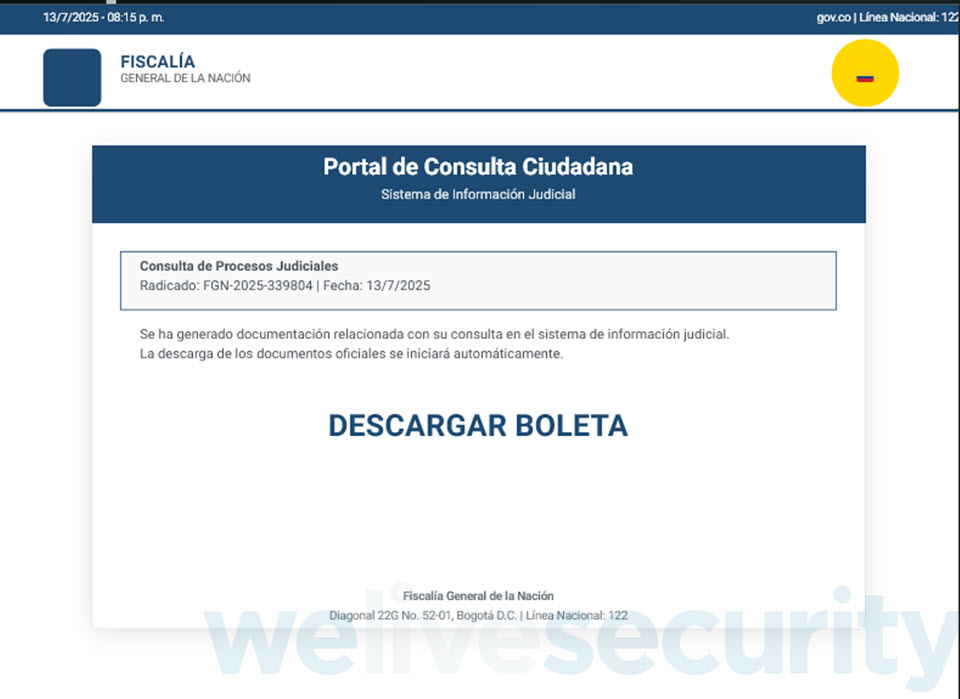
Victims navigate through fake verification screens and progress bars before being prompted to download a password-protected ZIP archive. The password is displayed on the page to reinforce authenticity.
Once the ZIP archive is extracted, it contains an executable dropper that leverages DLL sideloading.
By abusing a legitimate Windows application’s DLL search order, the dropper injects a malicious library, allowing AsyncRAT to load under the guise of normal system behavior. This technique evades many endpoint detection tools that whitelist known binaries while overlooking side-loaded modules.
AI-Assisted Customization and Self-Contained Payloads
A distinguishing feature of this campaign is the absence of external command-and-control (C&C) calls within the SVG files. Instead, all necessary payload components, including compressed RAT binaries, are base64-encoded directly in the SVG’s XML.
The dropper assembles and writes these components “on the fly,” eliminating network indicators that defenders commonly monitor.
Security telemetry indicates that each victim receives a uniquely generated SVG, likely produced by an AI-powered toolkit.
Analysis of sample XML templates reveals telltale signs of large language model authorship: repetitive class names, boilerplate text fragments, and invalid MD5-style “verification hashes.” This randomization frustrates static signatures and forces defenders to rely on behavioral analysis.
ESET researchers first identified this method in 2019; however, its refinement, particularly SVG smuggling, was added to the MITRE ATT&CK framework only recently, under T1027.017.
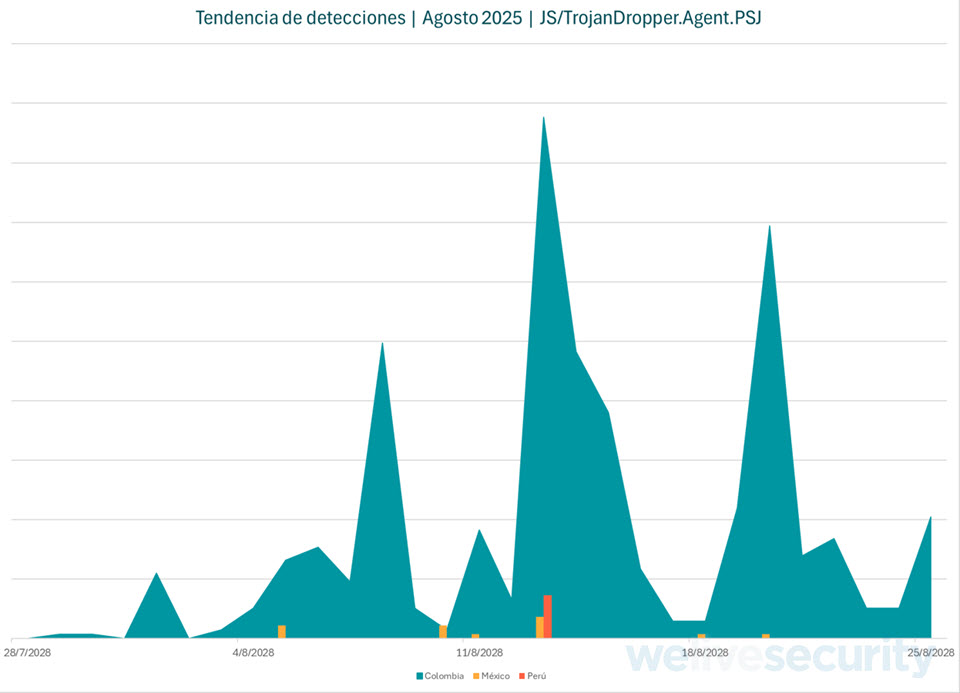
The current campaign’s mid-week activity spike throughout August, with Colombia the primary target, suggests a well-orchestrated operation rather than opportunistic blasts.
Despite the sophistication, the attack hinges on fundamental phishing psychology: fear and authority. The use of self-contained SVG deliverables and AI-generated uniqueness raises the bar, but also underscores a core lesson: vigilance remains the best defense.
Never enable scripts or macros from unsolicited files, and treat any SVG email attachment with extreme suspicion. Combining strong, unique passwords and two-factor authentication across accounts can limit post-infection damage.
Organizations should enforce rigorous email filtering, inspect large SVG attachments for embedded scripts, and deploy endpoint protection capable of detecting DLL sideloading anomalies.
In an age where attackers leverage AI to outpace traditional defenses, layered security and user education are more critical than ever.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates