The latest threat campaigns targeting enterprise and consumer environments have unveiled a sophisticated delivery mechanism that leverages SVG email attachments to distribute BAT-based loaders for XWorm and Remcos Remote Access Trojans (RATs).
By masquerading malicious content within seemingly innocuous image files and ZIP archives, attackers achieve fileless execution, evading static analysis and endpoint defenses.
Security teams are advised to update detection rules to incorporate behavioral indicators around SVG rendering and PowerShell invocation originating from non-traditional file formats.
Attack Chain and Loader Obfuscation
These campaigns initiate when a user receives an email containing an SVG attachment hosted on legitimate-looking platforms such as ImgKit.
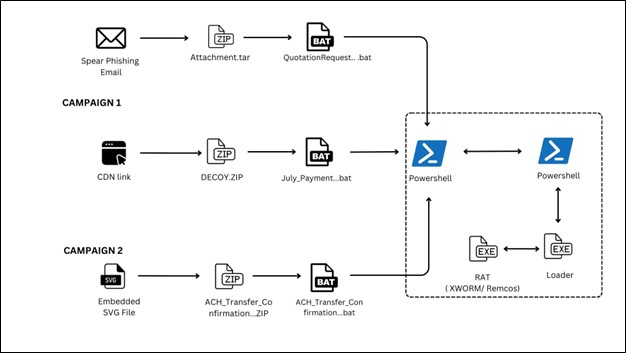
Upon rendering the SVG either in a vulnerable mail client or a phishing page, the embedded JavaScript silently requests a ZIP archive from a remote server.
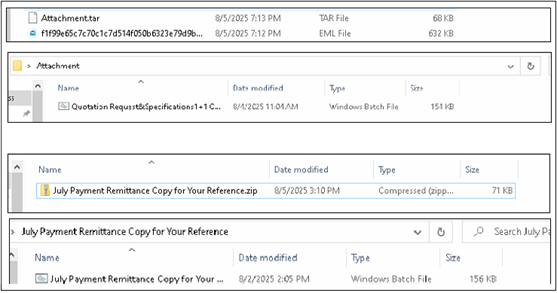
The downloaded archive contains an obfuscated BAT script that serves as the primary loader. Within the BAT file, multiple layers of command encoding and deliberate name collisions thwart signature-based scanning.
Once executed, the script invokes PowerShell with the flags -nop, -w hidden, and -enc to decode and run a Base64 payload in memory.
This approach circumvents disk writes entirely, loading the .NET-based loaders directly into RAM using dynamic assembly invocation or, in some variants, decrypting and executing raw shellcode via VirtualProtect and delegate functions resolved through Marshal.GetDelegateForFunctionPointer.
To maintain persistence, the loader copies itself to the user’s Startup folder as a BAT file, ensuring execution at each login. The PowerShell code further disables Windows security telemetry by patching AMSI and ETW functions in memory.
Employing .NET reflection and dynamic delegate creation, the script locates AmsiScanBuffer and EtwEventWrite in process memory and overwrites their prologues with instructions (mov eax,0; ret) that neutralize scanning and event tracing.
This combination of fileless execution, in-memory patching, and autostart registry manipulation enables the RATs to operate stealthily over extended periods.
RAT Deployment and Capabilities
Once the loader establishes persistence, it retrieves encrypted and compressed payloads embedded as Base64-encoded strings within comment lines of the BAT file.
The PowerShell logic splits the payload into segments, decodes them, applies AES-CBC decryption with a hardcoded key and IV, and performs GZIP decompression.
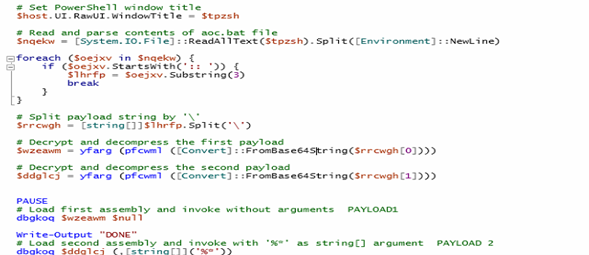
The resulting .NET assemblies are then executed one without parameters and another with '%*' to simulate command-line input.
These assemblies function as loaders for XWorm or Remcos, depending on the variant. XWorm provides comprehensive remote control features such as keylogging, remote shell execution, and file transfer, while Remcos adds capabilities including remote desktop viewing, screenshot capture, and credential harvesting.
Defenders should bolster content inspection to include SVG scripting behaviors, enforce strict PowerShell logging, and deploy runtime detection capable of identifying memory-only payloads.
Enhanced user awareness training around the risks of opening unexpected image attachments can further mitigate successful exploitation by these evolving campaigns.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates