Cybercriminals exploit malicious SVG files in phishing campaigns targeting Ukrainian organizations, deploying Amatera Stealer and PureMiner malware through sophisticated attack chains.
FortiGuard Labs has uncovered a sophisticated phishing campaign leveraging malicious Scalable Vector Graphics (SVG) files to impersonate Ukrainian government agencies and deploy multiple malware variants on Windows systems.
The attack targets any organization and poses a high-severity risk, enabling remote device control, theft of sensitive data, and cryptocurrency mining operations.
Advanced Attack Chain Exploits SVG Vulnerabilities
The campaign begins with fraudulent emails claiming to originate from Ukraine’s National Police, containing SVG attachments named “elektronni_zapit_NPU.svg.”
These files embed HTML iframe elements that reference external SVG resources, creating a multi-stage infection process that bypasses traditional security measures.
When victims open the attachment, the malicious SVG displays a spoofed Adobe Reader interface with Ukrainian text stating “Please wait, your document is loading.”
The file automatically redirects users to download a password-protected archive containing a Compiled HTML Help (CHM) file. The archive provides the extraction password, creating a false sense of legitimacy.
The CHM file contains a malicious HTML document with a shortcut object that executes remote HTML Application (HTA) resources in hidden mode.
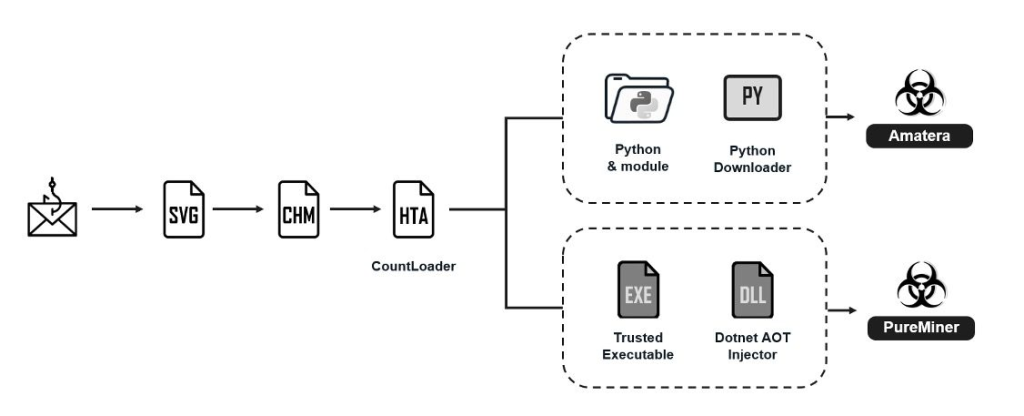
This HTA functions as a CountLoader, establishing Command and Control (C2) communications using XOR Base64 encoding. The loader supports six distinct commands for payload delivery, domain reconnaissance, and trace removal.
Dual Malware Deployment Through Fileless Techniques
CountLoader delivers two primary payloads: Amatera Stealer and PureMiner, both of which are executed using advanced fileless techniques to evade detection.
The ergosystem.zip archive deploys PureMiner through DLL sideloading and .NET Ahead-of-Time (AOT) compilation, utilizing process hollowing to inject the payload into legitimate .NET Framework processes.
PureMiner functions as a sophisticated cryptominer, collecting detailed hardware specifications through AMD Display Library and NVIDIA APIs.
The malware verifies systems have at least 4GB of memory before deploying CPU or GPU mining modules based on hardware capabilities. All C2 communications utilize 3DES encryption for operational security.
The second payload, Amatera Stealer, is loaded through smtpB.zip, which contains a Python interpreter and malicious scripts that utilize PythonMemoryModule for memory-only execution.
This stealer targets extensive data categories, including system information, browser credentials, cryptocurrency wallets, Steam accounts, Telegram data, and desktop files.
Amatera employs dual decryption techniques for Chromium-based browsers: legacy cookie decryption using CryptUnprotectData and App-Bound Encrypted (ABE) data decryption through COM API shellcode injection.
The malware targets popular cryptocurrency wallets, including MetaMask, Trust Wallet, Coinbase, and Phantom, as well as desktop applications such as FileZilla and AnyDesk.
Fortinet Protection: FortiGuard Antivirus detects this campaign under multiple signatures including HTML/Phish.09F5!tr, HTA/Agent.38f7!tr, and Python/Agent.3F5C!tr.dldr.
Organizations should implement comprehensive email security, endpoint detection, and user awareness training to defend against these evolving SVG-based attack vectors.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates