A sophisticated Advanced Persistent Threat (APT) campaign, identified as Swan Vector, has been uncovered by Seqrite Labs APT-Team.
The campaign is actively targeting nations across the East China Sea, notably Taiwan and Japan, with an emphasis on educational institutions and the mechanical engineering industry.
Attackers are leveraging spear-phishing tactics, distributing ZIP archives containing malicious LNK files disguised as candidate resumes.
These decoys act as the initial infection vector, setting off a multi-stage attack chain designed to stealthily compromise targeted systems.

Multi-Stage Malware Chain
The Swan Vector campaign is structured in four distinct stages, each demonstrating advanced evasion and persistence techniques:
- Stage 1: Malicious LNK Initiation: The attack begins with ZIP archives such as “歐買尬金流問題資料_20250413 (6).rar” containing a seemingly benign LNK file (“詳細記載提領延遲問題及相關交易紀錄.pdf.lnk”). Rather than opening a document, the LNK spawns the native Windows utility rundll32.exe to execute a disguised DLL implant named Pterois (embedded in a PNG file).
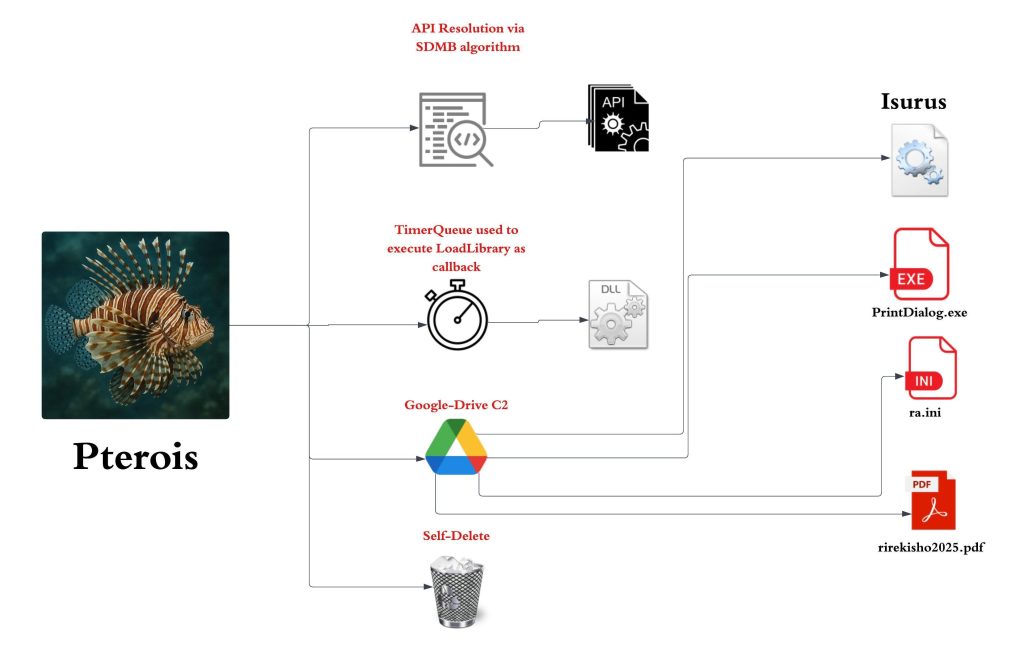
- Stage 2: Pterois DLL Loader: The Pterois DLL employs advanced API hashing and anti-analysis techniques. By directly accessing the Process Environment Block (PEB) and using SDBM-based hash comparisons, it dynamically resolves required APIs from core system libraries (ntdll.dll, kernel32.dll, etc.), making traditional detection difficult. The implant then authenticates with Google Drive’s OAuth APIs to obtain access tokens and downloads subsequent payloads-including decoy PDF files and additional malicious binaries-masquerading these as legitimate network traffic to evade network security controls.
- Stage 3: Isurus DLL Sideloading: In this phase, the malware leverages DLL sideloading through a legitimate Windows-signed binary (PrintDialog.exe) bundled with a malicious DLL (PrintDialog.dll). The Isurus implant further resolves APIs via CRC32 hashes, extracts an encrypted shellcode payload from a configuration file (ra.ini), and decrypts it using a hardcoded RC4 key. For execution, Isurus leverages direct system call injection techniques, minimizing reliance on high-level Windows APIs and evading EDR products.
- Stage 4: Cobalt Strike Shellcode Delivery: The decrypted shellcode is identified as a Cobalt Strike beacon, configured for process injection into system binaries (such as bootcfg.exe) and communicating with C2 infrastructure at
52.199.49.4:7284. Communication is disguised as ordinary HTTP traffic, further obfuscating the attack.
C2 Infrastructure and Attribution
According to Seqrite, the operation’s C2 uses Google Drive, with stolen OAuth credentials and hardcoded file IDs.
Digital forensics revealed an associated Gmail account ([email protected]) and uncovered numerous additional payloads likely prepped for future campaigns targeting other common binaries (Python, WMI, OneDrive Launcher, etc.).
Infrastructure analysis suggests strong links to East Asian APT groups, with notable overlaps in TTPs (Tactics, Techniques, and Procedures) including DLL sideloading and code similarities to observed Lazarus and APT10 campaigns.
Attribution is currently assessed at medium confidence, anchored to the East Asian cyber-geopolitical sphere.
Swan Vector demonstrates an emphasis on stealth and persistence:
- API and function hashing obscure malware activity.
- Direct system call execution (bypassing common API hooks).
- Legitimate Windows binaries for sideloading, increasing trust and lowering suspicion.
- Self-deletion routines ensure minimal forensic footprint post-infection.
- Google Drive C2 camouflages exfiltration among legitimate cloud service traffic.
The Swan Vector campaign exemplifies the evolution of East Asian APTs, highlighting a complex blend of custom malware components, abused cloud storage for C2, and advanced evasion.
Security teams in critical sectors across East Asia are advised to proactively hunt for the IOCs above and mitigate risks through advanced endpoint detection, network monitoring, and rigorous user awareness programs.
Indicators of Compromise (IOC)
| Type | Filename/Indicator | SHA-256 Hash / Details |
|---|---|---|
| Decoy PDF | rirekisho2021_01.pdf | 8710683d2ec2d04449b821a85b6ccd6b5cb874414fd4684702f88972a9d4cfdd |
| Decoy PDF | rirekisho2025.pdf | 8710683d2ec2d04449b821a85b6ccd6b5cb874414fd4684702f88972a9d4cfdd |
| Implant | wbemcomn.dll | c7b9ae61046eed01651a72afe7a31de088056f1c1430b368b1acda0b58299e28 |
| Implant | LoggingPlatform.dll | 9df9bb3c13e4d20a83b0ac453e6a2908b77fc2bf841761b798b903efb2d0f4f7 |
| Implant | PrintDialog.dll | a9b33572237b100edf1d4c7b0a2071d68406e5931ab3957a962fcce4bfc2cc49 |
| Implant | python310.dll | e1b2d0396914f84d27ef780dd6fdd8bae653d721eea523f0ade8f45ac9a10faf |
| Loader | Chen_YiChun.png | de839d6c361c7527eeaa4979b301ac408352b5b7edeb354536bd50225f19cfa5 |
| LNK File | 針對提領系統與客服流程的改進建議.pdf.lnk | 9c83faae850406df7dc991f335c049b0b6a64e12af4bf61d5fb7281ba889ca82 |
| Shellcode | 0g9pglZr74.ini | 9fb57a4c6576a98003de6bf441e4306f72c83f783630286758f5b468abaa105d |
| Shellcode | ra.ini | 0f303988e5905dffc3202ad371c3d1a49bd3ea5e22da697031751a80e21a13a7 |
| Config | python.xml | c8ed52278ec00a6fbc9697661db5ffbcbe19c5ab331b182f7fd0f9f7249b5896 |
| Crypto | KpEvjK3KG2.enc | e86feaa258df14e3023c7a74b7733f0b568cc75092248bec77de723dba52dd12 |
| C2 Server | IP Address | 52.199.49.4:7284 |
| C2 Email | Gmail | [email protected] |
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant updates