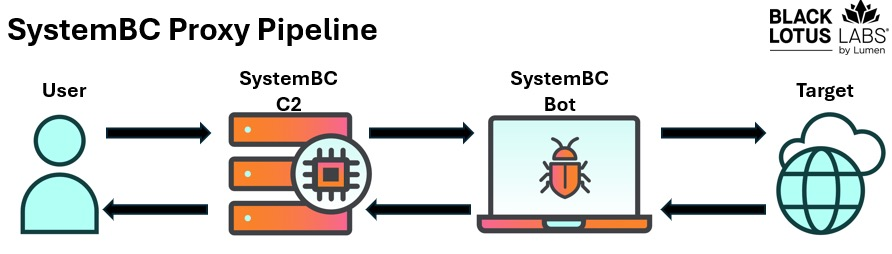
Documented initially by Proofpoint in 2019, the SystemBC botnet has morphed into a formidable proxy service that now operates more than 80 command-and-control (C2) servers and maintains an average of 1,500 active infections every day.
In a departure from the typical residential-IP botnet model, SystemBC exploits virtual private servers (VPS) provided by central cloud hosting companies, achieving continuous uptime and exceptionally high throughput.
During one 24-hour observation window, a single SystemBC-powered proxy channeled over 16 GB of malicious traffic, an order of magnitude beyond what residential devices can handle.
Nearly 80% of the botnet’s daily victims reside within just five commercial VPS clouds, underscoring the operators’ strategy of targeting high-capacity infrastructure for volumetric abuse.
Persistent infections are common, with nearly 40% of bots remaining active for over a month, a stark contrast to the frequent churn seen in consumer-grade endpoints.
Advanced Payload Encryption and C2 Communication
SystemBC’s payload loader, available in both Windows and Linux variants, begins by decrypting a 40-byte XOR key embedded in memory.
This key unlocks the C2 configuration server addresses, DNS resolvers, and port numbers before the malware establishes SOCKS5 proxy functionality on the victim host.
Initial beacon packets consist of the raw XOR key (bytes 0–49), the Windows build ID (bytes 50–51), the architecture flag (bytes 52–53), and the account name, padded to 100 bytes, all transmitted to a C2 on high-numbered TCP ports.
Response packets from the C2 incorporate a 4-byte header specifying packet type, proxy index, and payload length, followed by SOCKS5 instructions.
SystemBC employs a double-layer encryption scheme XOR, RC4, then XOR again to secure both outbound beacon traffic and inbound C2 commands, effectively concealing proxy commands within otherwise benign-appearing sessions.
In Linux samples, the malware configures an encrypted beacon comprising a 40-byte key, ten bytes of padding, and a 50-byte sequence beginning with 0xFFFF. After XORing and RC4 encryption, the beacon is XORed again before dispatch.
The C2 response follows a mirroring decryption workflow to instruct proxy instantiation, keep-alive messages, or an exit command (0xFF). All communication channels seamlessly integrate with HTTPS flows to mask illicit traffic.
Tiered Criminal Proxy Ecosystem Powered by SystemBC
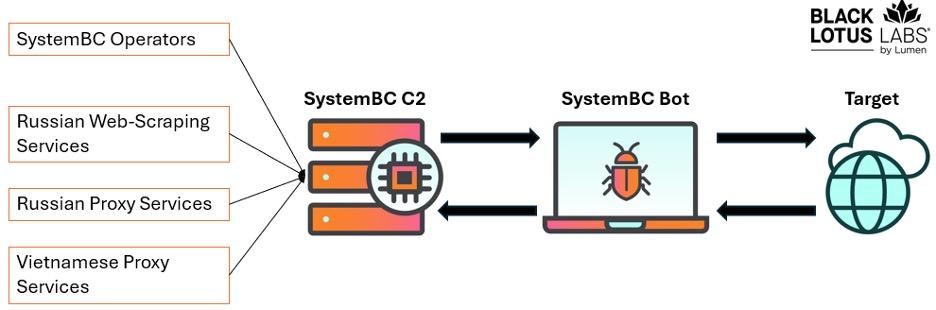
Black Lotus Labs telemetry links SystemBC victims to multiple underground proxy services, including at least two Russia-based providers, a Vietnamese storefront known as VN5Socks, and a Russian web-parsing operation.
The most prominent affiliate is “REM Proxy,” which sources roughly 80% of its proxy pool from SystemBC.
REM Proxy markets three service tiers: “Mix-Speed” offering low-detection Mikrotik and open proxies; “Mix-Economy” comprising high-detection, lower-quality bots ideal for credential stuffing; and “Mix-Mix,” a combination package.
Ransomware gangs such as Morpheus and AvosLocker leverage these proxies for tasks ranging from phishing distribution to data exfiltration and breach orchestration.
Netflow analysis confirmed direct links between REM Proxy user entry ports, Mikrotik SSH ports on 51922, and SystemBC C2 nodes, illustrating a tightly integrated criminal infrastructure.
Nearly all SystemBC-sourced IP addresses eventually appear on public blocklists due to aggressive scanning and brute-force activities. However, operators prioritize throughput over stealth, unleashing high volumes of malicious traffic without concern for detection.
One victim server, identified via Censys, hosted over 160 unpatched CVEs, highlighting how vulnerable cloud assets fuel the botnet’s expansion.
Long-Lived Infections Fueled by Vulnerable VPS
Investigation into initial access revealed that potential victims are probed on TCP port 443; successful exploits lead to callbacks on port 80, where a Russian-commented shell script downloads and executes upwards of 180 SystemBC samples concurrently.
The rapid parallel deployment of multiple payloads ensures a stable proxy mesh across compromised instances.
Over a span of months, Lumen’s global IP telemetry cataloged daily recruitment of approximately 2,500 new bots, 2,000 attributed to SystemBC and 500 to related proxy services, underscoring the network’s resilience.
Community Defense and Mitigation Strategies
Lumen Technologies’ Black Lotus Labs has disrupted SystemBC and REM Proxy traffic across its global backbone and published a comprehensive set of indicators of compromise (IoCs).
Network defenders should enforce strict egress filtering, block known SystemBC C2 endpoints, and monitor for credential-spraying events originating from commercial IP ranges.
Routine vulnerability management on VPS instances is critical: regular patching can invalidate dozens of exploit opportunities per host. SOHO router owners must install firmware updates, change default credentials, and disable remote management interfaces to thwart secondary pivoting.
Active collaboration, including real-time telemetry sharing and coordinated takedowns, remains essential to dismantle large-scale proxy networks like SystemBC.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates