A sophisticated South Asian advanced persistent threat (APT) group has been conducting an extensive espionage campaign targeting military personnel and defense organizations across Sri Lanka, Bangladesh, Pakistan, and Turkey.
The operation combines traditional phishing techniques with novel mobile malware deployment, successfully compromising smartphones belonging to military-adjacent individuals and exfiltrating sensitive communications, contact lists, and operational documents.
Multi-Vector Attack Campaign Exploits Military Themes
The threat actors initiated their campaign using carefully crafted PDF documents with military-specific themes, including “Coordination of the Chief of Army Staff’s Visit to China.pdf” and “Updated TOSAM 120 MM MORTAR ALKAR 110, 120, TURKIYE.pdf.”

These documents served as initial access vectors, redirecting victims through a sophisticated infrastructure of phishing domains hosted on legitimate services like Netlify and custom domains such as updatemind52.com and quickhelpsolve.com.
Analysis revealed over 40 phishing domains impersonating critical South Asian defense organizations, including the Directorate General of Forces Intelligence (DGFI), Bangladesh Air Force, Ministry of Defence, and Turkish defense contractors like Roketsan and Aselsan.
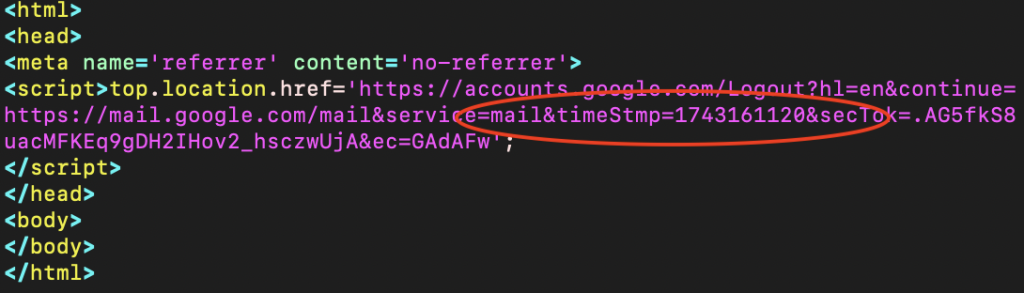
The threat actors demonstrated advanced operational security by utilizing JavaScript blockers to prevent source code analysis and hard-coding Unix timestamps corresponding to March 28th, 2025, across multiple landing pages.
Modified Android RAT Enables Comprehensive Device Compromise
The APT’s mobile component centers on a modified version of the open-source Rafel RAT, disguised as legitimate applications including “Love_Chat.apk,” “PvtChat.apk,” and “Social Chat.apk.”
These malicious Android packages (APKs) request extensive permissions, including ADD_DEVICE_ADMIN, READ_EXTERNAL_STORAGE, and READ_CONTACTS, enabling comprehensive device compromise.
The modified RAT communicates with command and control servers at kutcat-rat.com and quickhelpsolve.com, with the C2 panel publicly accessible and indexed by search engines before being disabled.
Analysis of the compromised data revealed extensive intelligence collection, including SMS messages, contact lists containing military ranks and duty stations, and sensitive documents from victims across multiple South Asian nations.
Extensive Intelligence Harvest Reveals Military Targeting
The operation’s success is evidenced by the substantial data theft observed on the threat actors’ servers.
Stolen content included raw SMS communications, comprehensive address books containing only military ranks and duty stations, and operational documents from defense personnel.
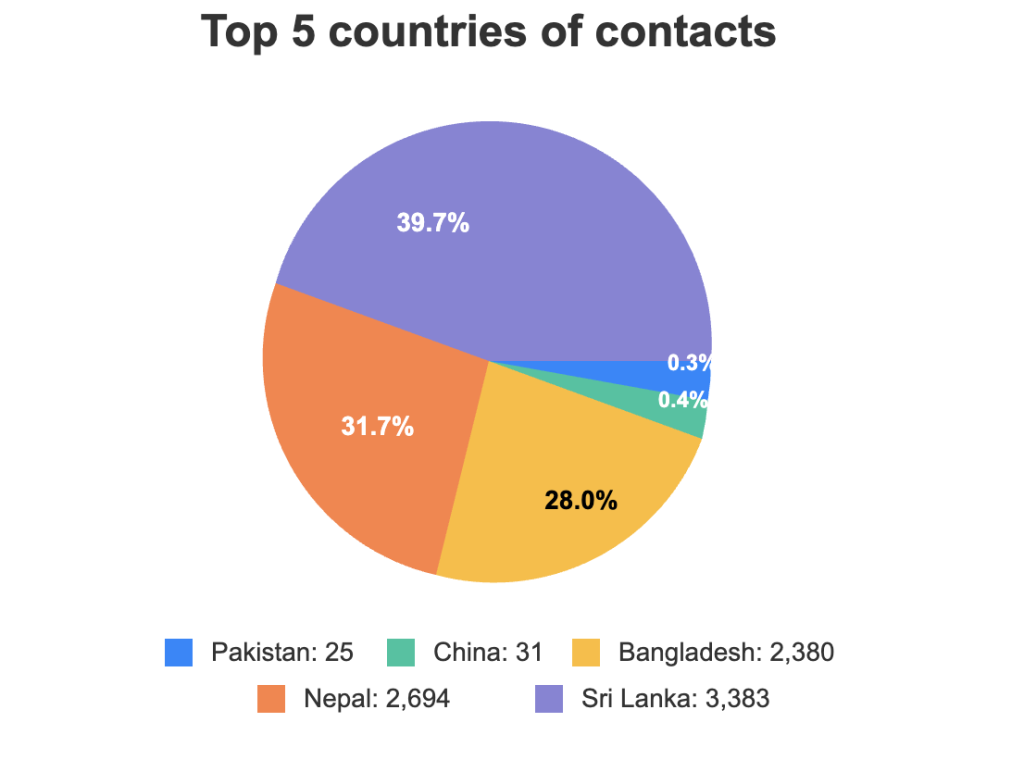
Geographic analysis of compromised devices indicates victims are primarily located across South Asia, with the highest concentration in Bangladesh and Pakistan.
Infrastructure analysis revealed that the threat actors also deploy Windows-based malware using the same C2 infrastructure, with samples containing debugging paths suggesting a developer environment username “Android.”
The campaign’s persistence and sophistication, combined with its focused targeting of military personnel, indicate a nation-state or nation-state adjacent threat actor conducting strategic intelligence collection operations across the South Asian defense sector.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates